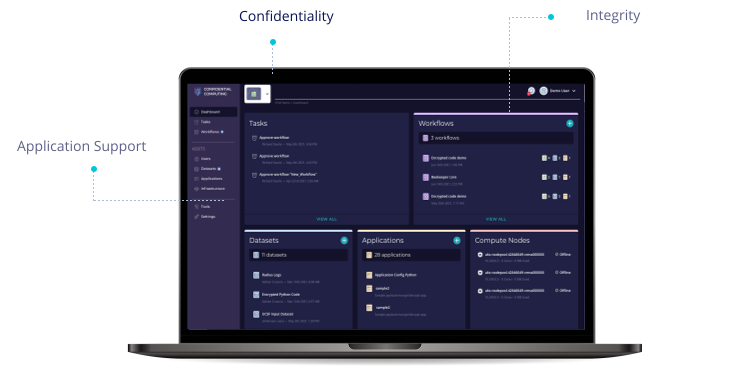
Confidential Computing Solution
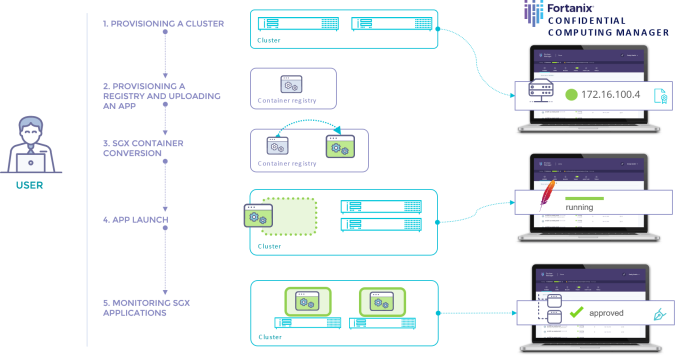
Fortanix offers application teams the fastest, easiest, and most complete solution to run enclave applications today. The Fortanix Confidential Computing Manager enables applications to run in confidential computing environments, verifies the integrity of those environments, and manages the enclave application lifecycle.


 |
Without Fortanix |
|
|---|---|---|

Simplicity |
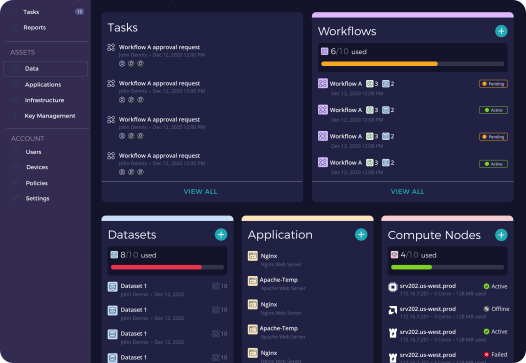
Enclave Lifecycle ManagementFortanix is the only turnkey solution that manages the entire confidential computing environment and enclave lifecycle. |
Manual ManagementGetting start using confidential computing requires the integration of multiple infrastructure components, rewriting applications and manually configuring and verifying applications running in enclaves. |

Application Support |
Broadest Set of Application SupportFortanix makes it possible to enable existing applications, enclave-native applications, and pre-packaged application to run in a secure enclave in minutes. This capability in unique and enables widespread adoption of confidential computing with no development or integration costs. |
Re-write ApplicationsTo get an application running in a secure enclave, developers must rewrite applications using open-source SDKs. This take time and often discourages the use of confidential computing. |

Security |
Cryptographically enforced policy and auditingFortanix manages and enforces security policies including identity verification, data access control, and attestation to ensure the integrity and confidentiality of data, code, and applications. Using these policies, businesses can implement geo-fencing, and compute affinity to support data regulation policies such as GDPR. Fortanix also provides audit logs to easily verify compliance requirements. |
Build your own securityTo securely implement confidential computing, critical services are required for authentication, encryption, attestation, and audit to ensure the integrity and confidentiality of data, code, and applications. These services are not built-into the infrastructure. |















 3910 Freedom Circle, Suite 104,
3910 Freedom Circle, Suite 104,