Reveal Risks Across Enterprise Silos

Discover At-Risk Keys and Services
Fortanix automatically scans your on-prem and multicloud environments to catalog every existing encryption key and data service, flagging and ranking each security risk in an intuitive dashboard view. Drill down into at-risk keys or data services, to ensure regulatory compliance and start your quantum-readiness journey.

Assess and Prioritize Security Gaps
Get an instant risk score based on your key analysis results. Fortanix highlights your top security risks so you know where to focus first and rapidly improve your security posture.
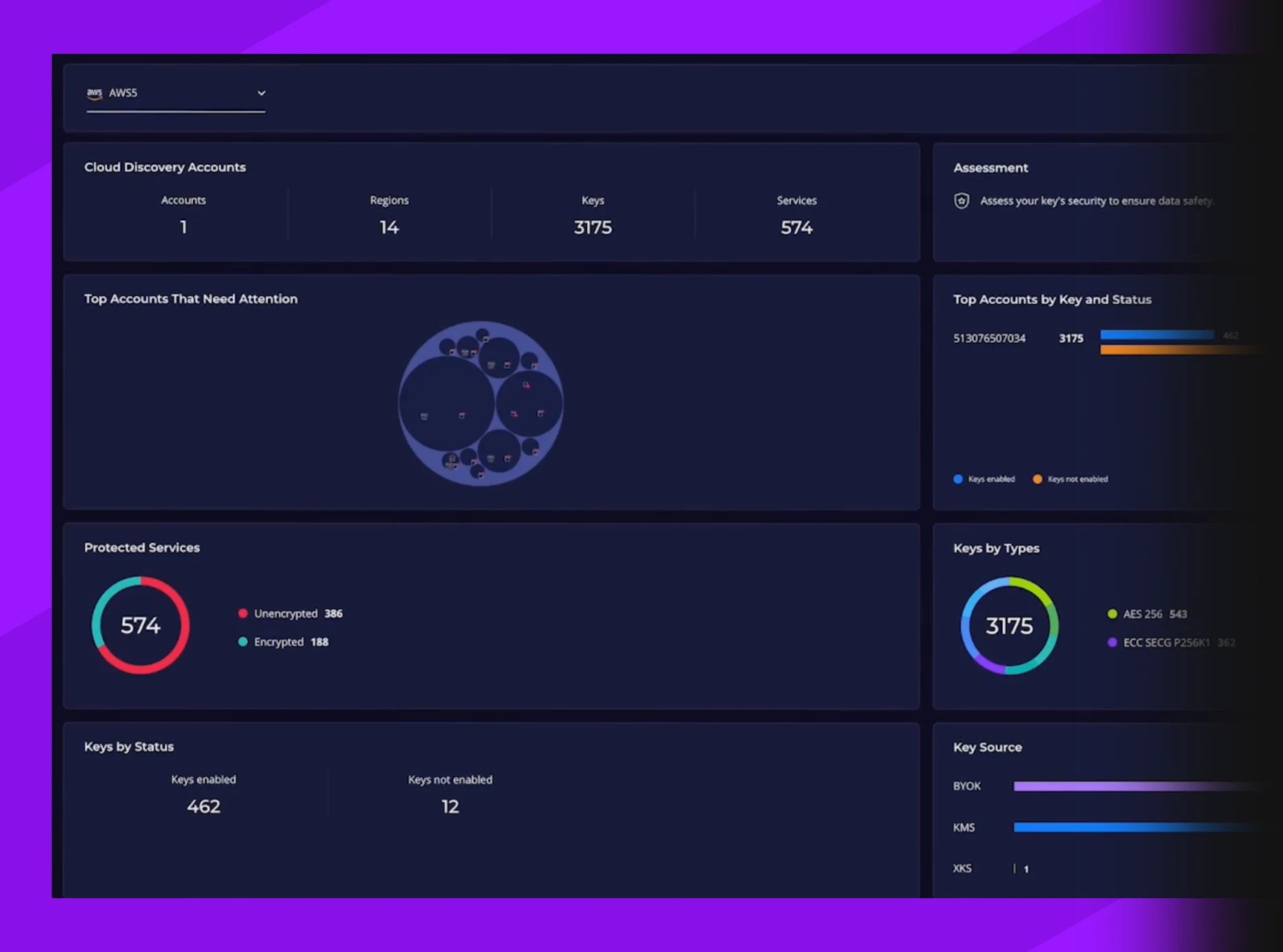
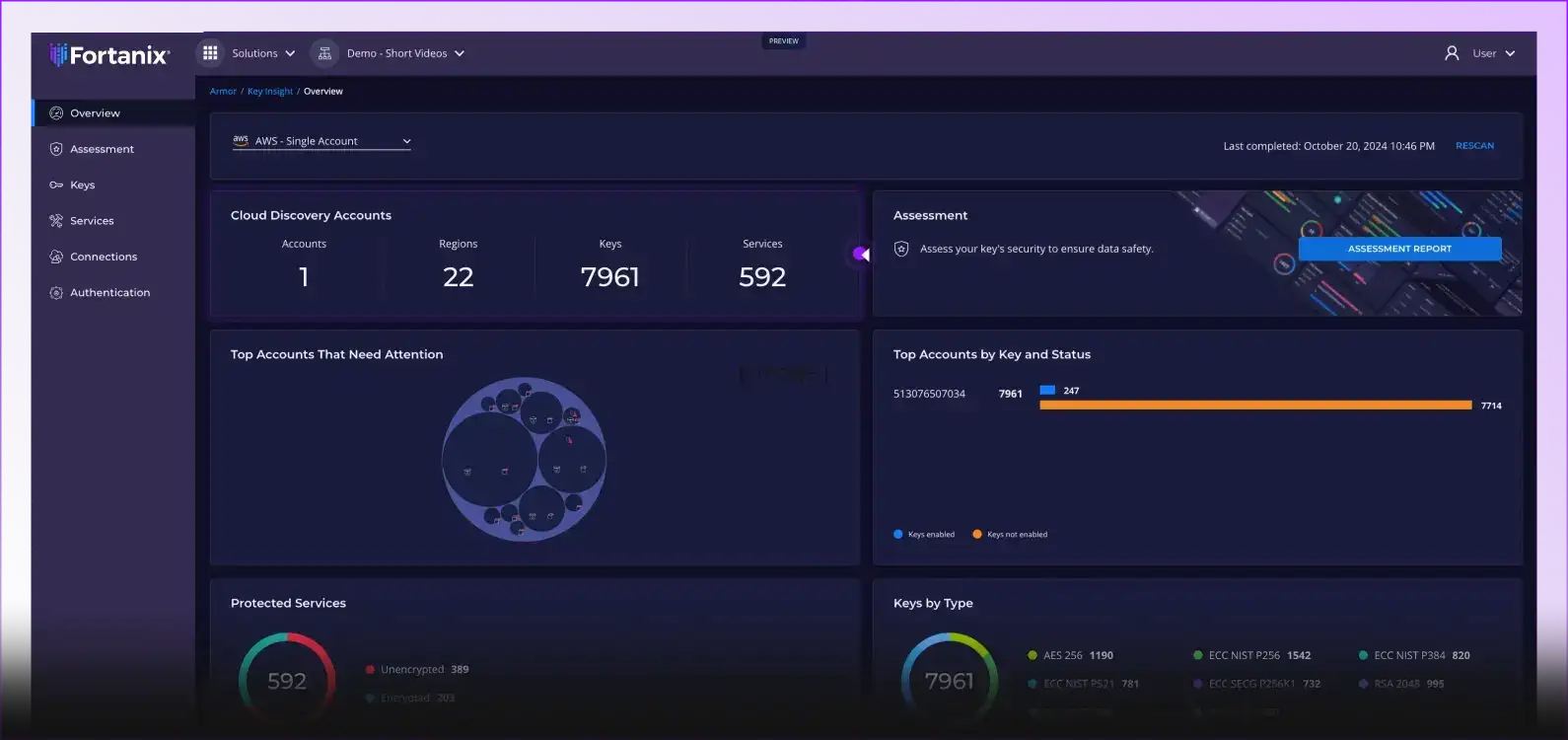
Discover ALL Encryption Keys and Data Services
Most organizations don’t know exactly where and how they apply cryptography. Discover all encryption keys in your on-premises and multicloud environment and see how they relate to data services, all from a central, unified dashboard. With read-only access permission, Key Insight scans your infrastructure. Your credentials and scanning results remain for your eyes only, protected by Confidential Computing technology.
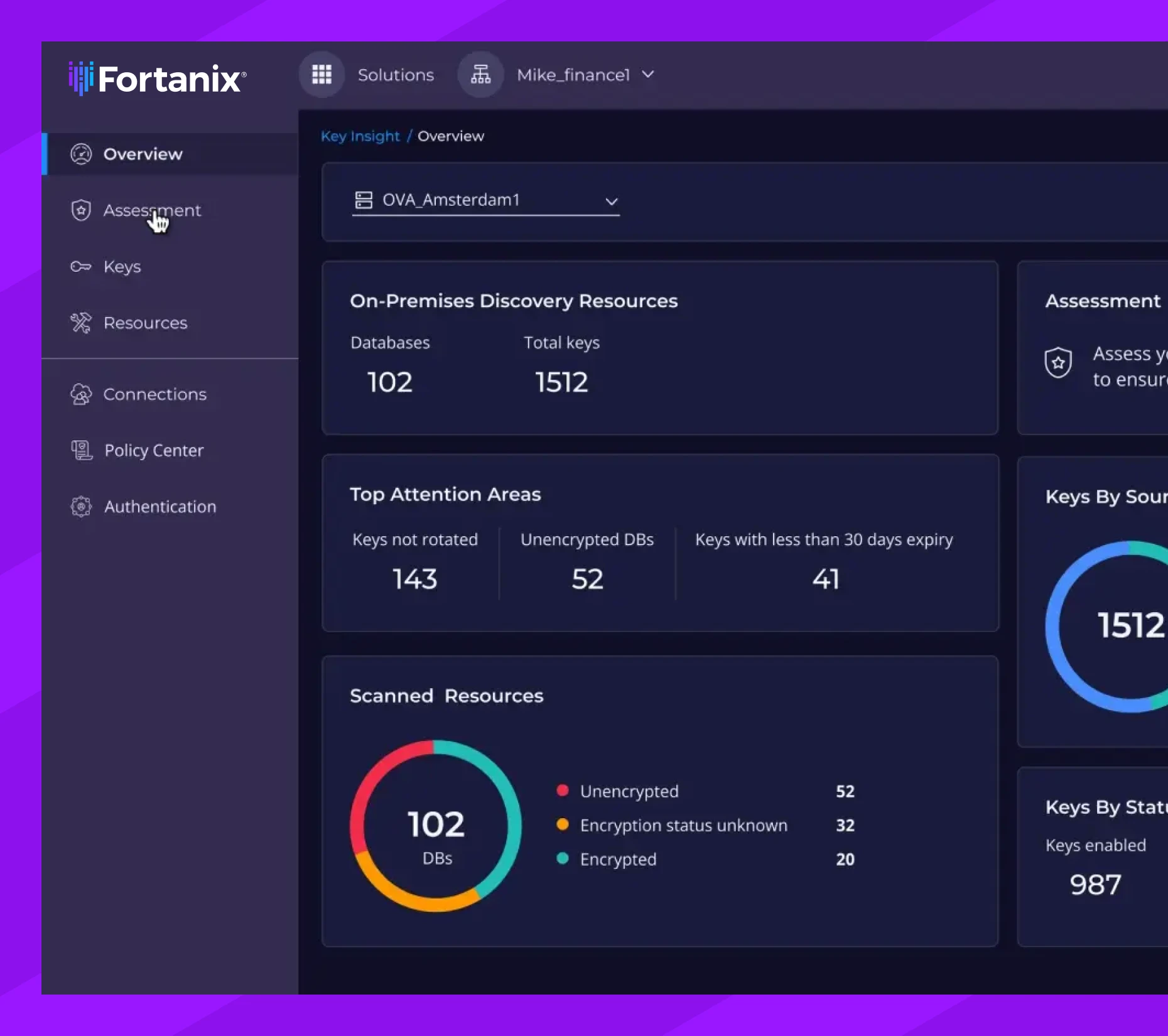
Data-Driven Risk Assessment
With the sprawl of data and encryption services across multicloud environments, it is difficult to see where your biggest data exposure risks are. Key Insight provides immediate insight into your biggest risks, including unencrypted services, keys shared by multiple services, keys without expiry (long-lived), or keys without scheduled rotation. Security teams can drill down further for more information about the key or service and devise a remediation path.
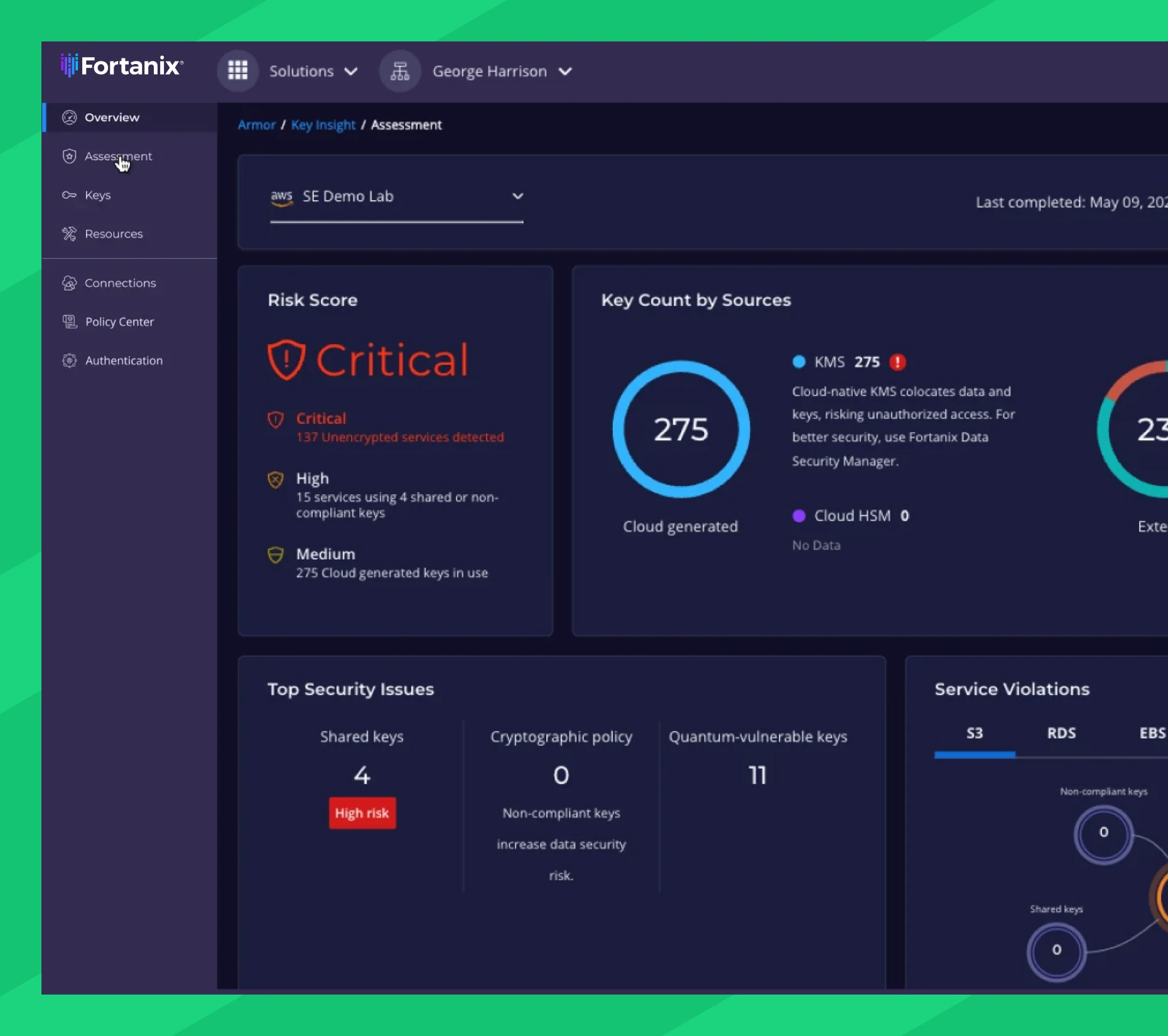
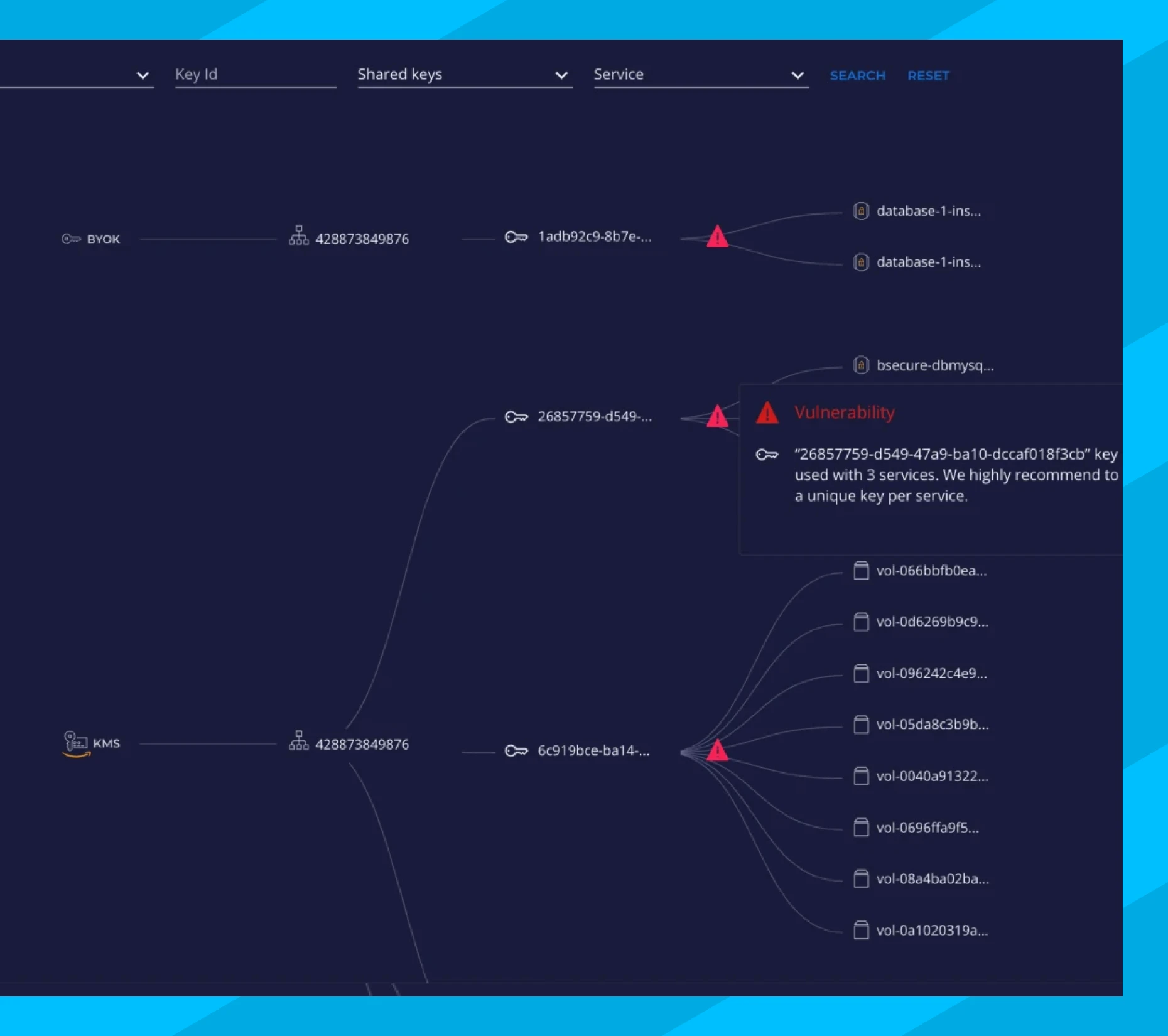
Assess Encryption Key Blast Radius
Encryption keys should only be used by a single service to contain risk and ensure accurate, granular logging. However, some organizations don’t know if they share keys between multiple services. Key Insight immediately shows which services use a key and which services are impacted if a key is compromised.
Detect Quantum-Vulnerabilities
Organizations that need their most sensitive data to remain secure for many years to come must start their post-quantum cryptography journey immediately. The journey starts with an in-depth assessment of where cryptography is applied and whether the algorithm is strong enough for the post-quantum era. Key Insight reveals where and how encryption keys are used across on-premises and multicloud environments, allowing you to identify and prioritize where and when to apply post-quantum cryptography.
Reveal Key Details
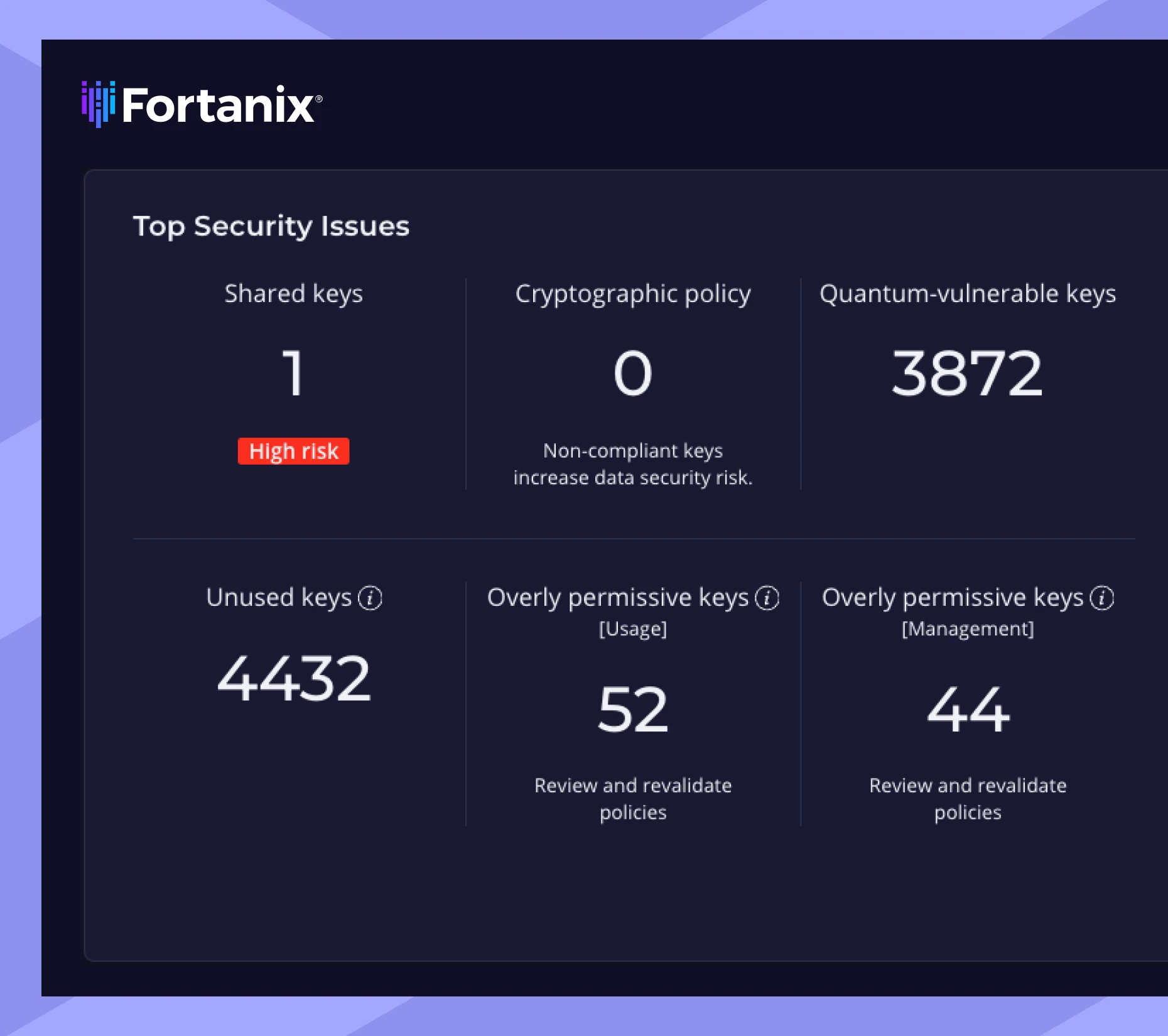
Immediately identify the most important risks, and drill down into the details.

Unencrypted services
Attackers get unhindered access to sensitive data

Services using deleted keys
Preserve data before a service reboot

Keys shared by multiple services
Unique keys limit the blast radius of a compromised key

Non-compliant keys
Identify keys that don’t align with security best practice policy

Overly permissive keys
Keys without administrative or usage limits are at increased risk of compromise

Quantum-vulnerable keys
Keys known to be breakable by quantum computers
Enforce Governance and Compliance Across the Org
With Fortanix, you get centralized visibility and control over the policies and procedures that keep you compliant with PCI-DSS, HIPAA, GDPR, SOX, and dozens of others. The platform makes compliance easy, helping you pass audits faster and report on company-wide activity.


Pass audits faster
Key Insight provides security teams and auditors with immediate access to all critical information from a single dashboard.


Maintain compliance
Continuously monitor hyper-dynamic enterprise for new pressing risks and ensure continuous compliance.


Pinpoint Quantum-Vulnerable Keys
Discover which algorithms are not ready for the post-quantum threat.