Secure Manufacturing with Fortanix
Limit the impact of cyber vulnerabilities and sophisticated security threats in your distributed factory operations. Rapidly update to post-quantum cryptography algorithms now to prevent quantum computers from breaking your operations or exposing your sensitive data. The Fortanix unified data security platform securely generates, manages, and stores cryptographic keys, certificates, and secrets, allowing you to implement advanced security measures to ensure resilient manufacturing workflows.
How Fortanix Helps
Future-proof Firmware and Software Supply Chain with PQC Security
By proactively implementing PQC for software signing, manufacturers can protect their devices from the emerging threat of quantum computing. Fortanix DSM supports the latest NIST PQC algorithms and enables cryptographic agility to ensure long-term confidentiality and integrity of your software, even if devices are not connected to the internet.
Secure Signing for IoT Devices
Fortanix delivers a scalable cloud-native solution for an end-to-end management of the manufacturing process across global sites, including those not connected to the Internet. Fortanix DSM is highly available, and horizontally scalable, and allows you to run custom code n a trusted execution environment. This allows policies for usage and access control of keys to be defined and enforced by a device manufacturer across multiple sites.

Protect Business-Critical Information and Safeguard IP
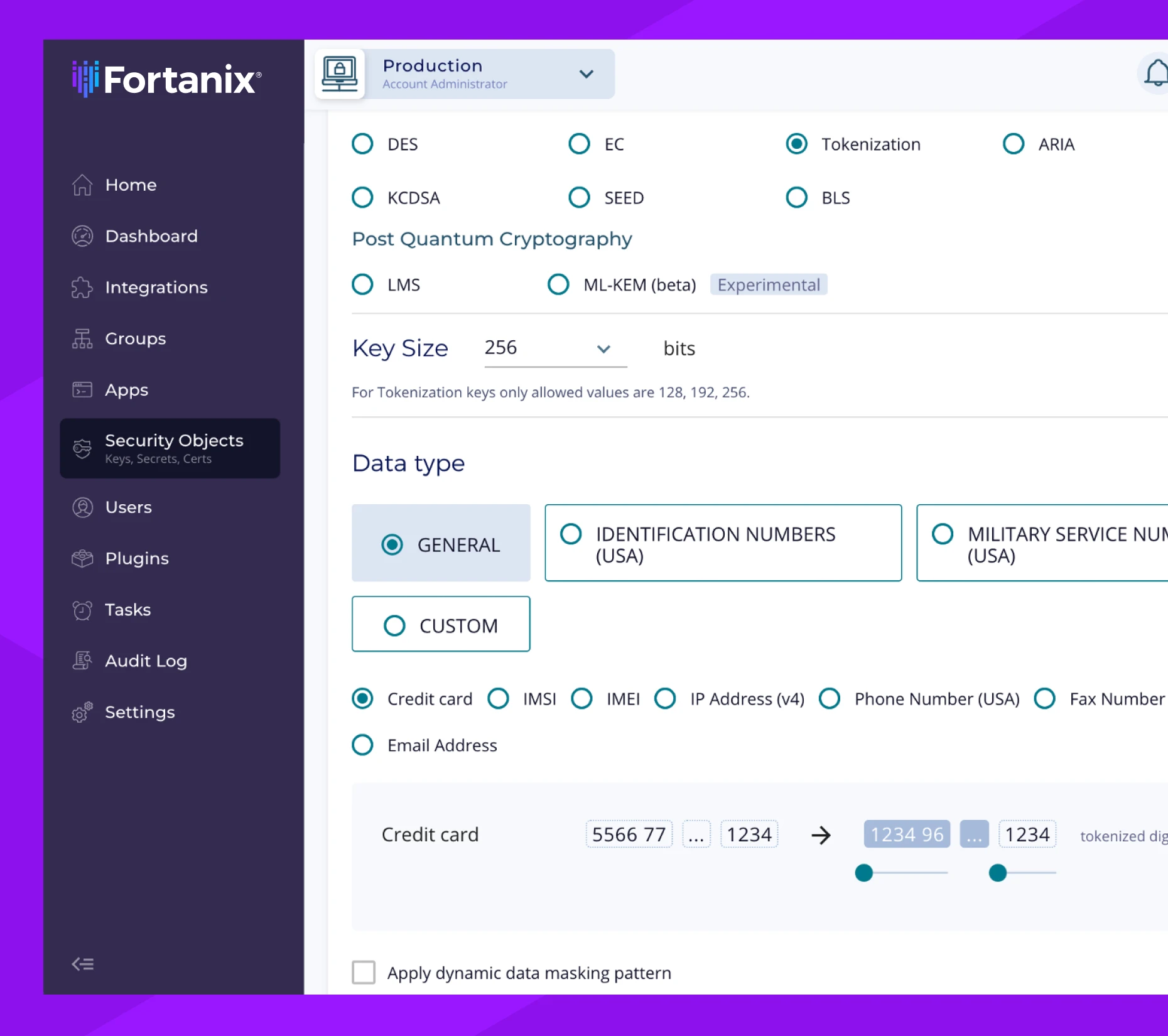
Streamline and gain control over disparate processes for data encryption, data tokenization, key management, credential and certificate storage, and more. Standardize on a single platform for cryptographic services and give your teams a single pane of glass for management and visibility into your distributed operations. Scale as needed to easily respond to a surge in demand.
Future-Proof Manufacturing Innovation with Fortanix
Transform your data security operations to transcend your business operations.

Legacy to Cloud
Migrate workloads to cloud infrastructure without losing the control you have in the data center.

Safe Data Usage
Tokenize sensitive or business-critical data to feed it into analytics and AI/ML to unlock its full potential.

Post-Quantum Readiness
Rapidly apply latest NIST-recommended algorithms and be ready for the quantum risk now.
Deploy a Modern Solution You Can Trust
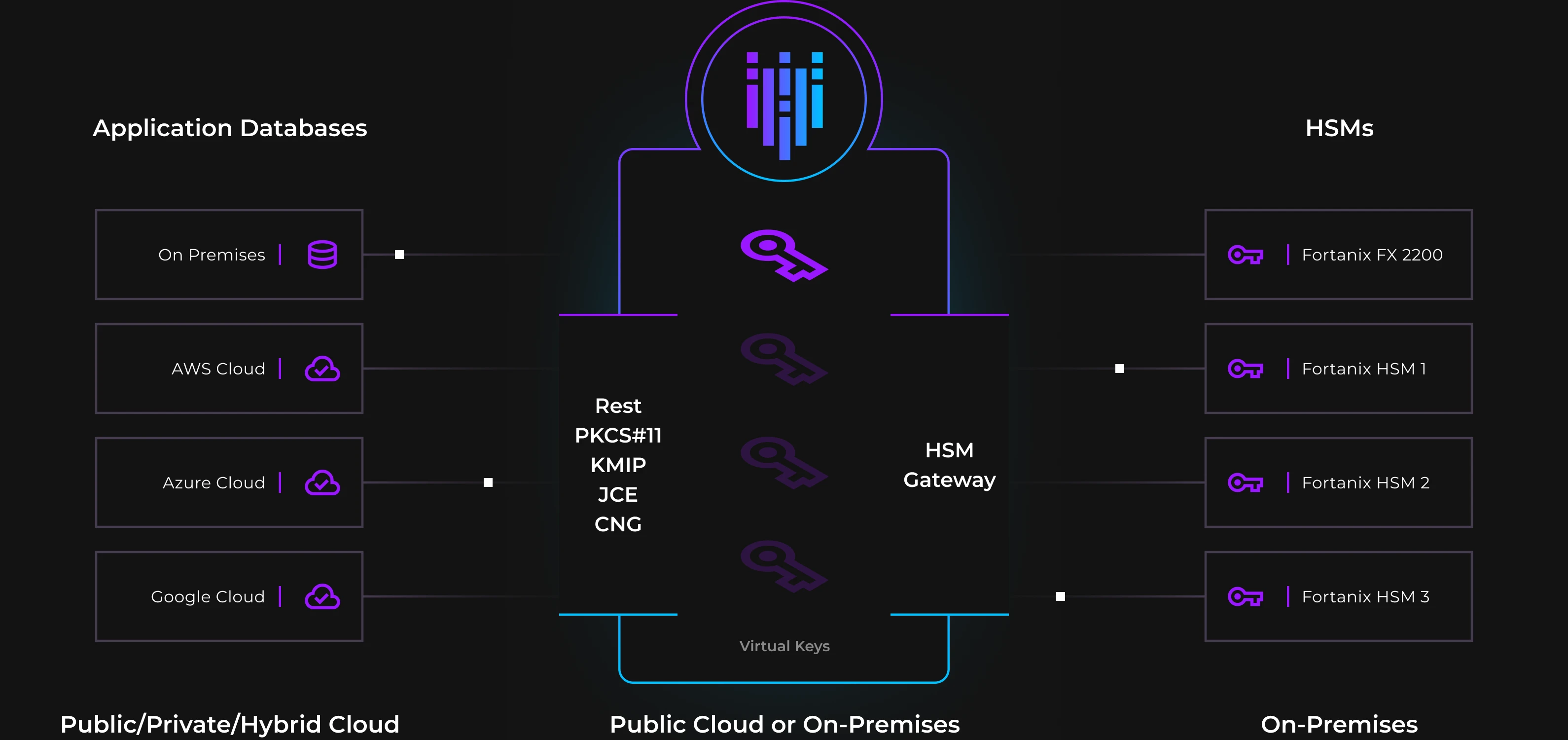
As you strengthen your encryption methods and close gaps in your security posture, store keys and secrets on Fortanix’s scalable compliant solution. Consolidate your legacy HSMs with Fortanix’s scalable, FIPS 140-2 L3 validated appliance. Simplify operations, reduce cost, and increase control.
Featured Resource