A Unified Platform for Protected Healthcare Information
Bring next-gen data security to Protected Healthcare Information (PHI) with Fortanix. Consolidate data security efforts, enable secure cloud adoption, and prevent exposure of PHI across your business systems, cloud analytics, and AI/ML pipelines. Drive better patient outcomes and find cures for diseases.
How Fortanix Helps
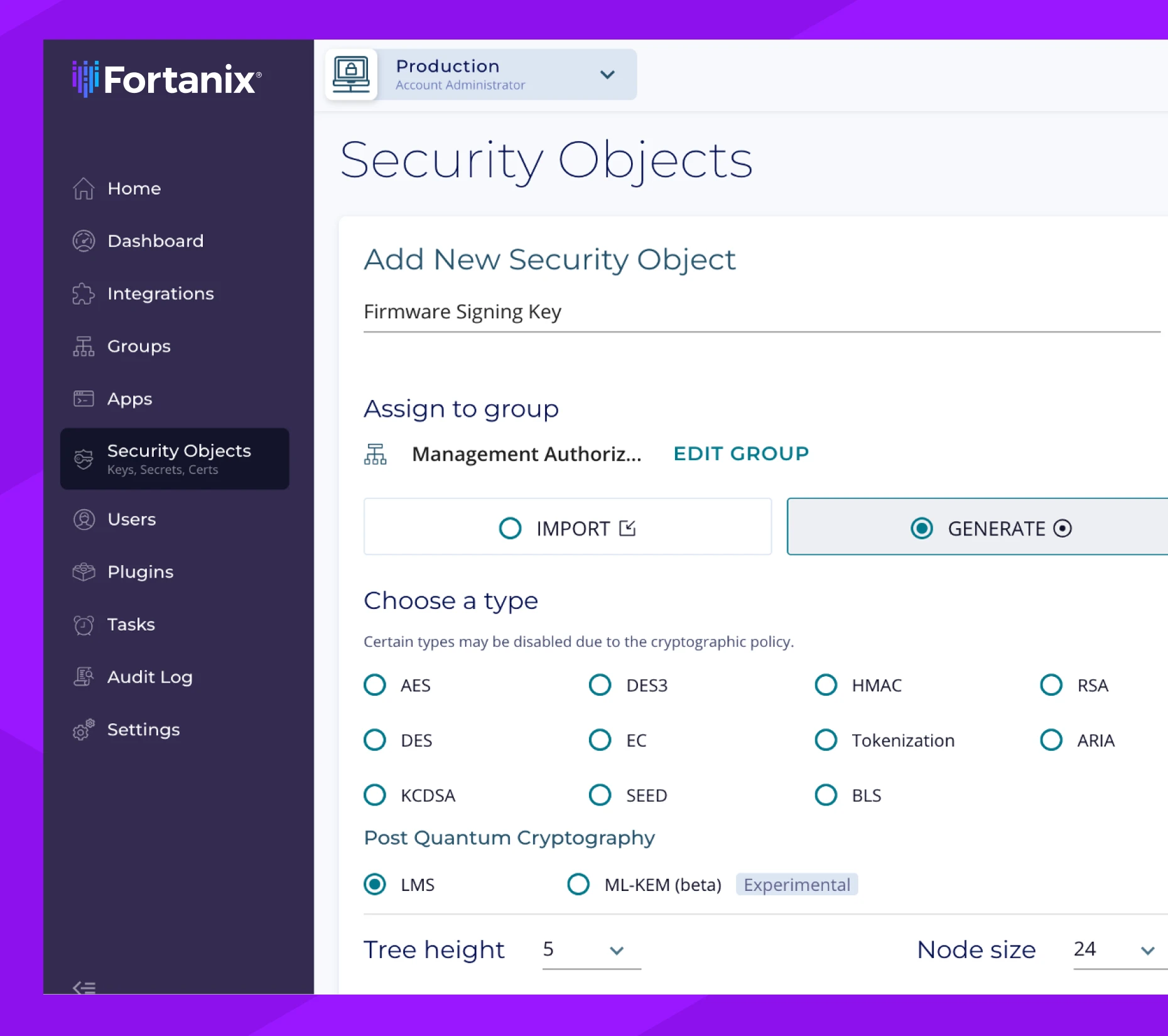
Enterprise Encryption and Key Management
Fortanix Data Security Manager (DSM) unifies disparate processes for data encryption and tokenization, key management, credential and certificate storage, for centralized operations, visibility, control.
- Encrypt data at-rest, in-transit, and in-use on a platform secured by confidential computing.
- Apply role-based access control (RBAC) for users, applications and groups with segregation of duties.
- Discover keys across the multicloud environments, classifying them by type and risk.
- Automate key distribution, rotation, and revocation across the organization.
- Protect PII and PHI with vaultless data tokenization.
Revitalize Your Data Security Practices
The data security landscape is changing fast. Stay ahead of threats and strengthen your agility by accelerating cloud adoption, apply hardened encryption protocols, and run your most sensitive processes in trusted execution environments.

Legacy to Cloud Infrastructure Migration
Migrate workloads to the cloud without losing the control you have in the data center. Fortanix enables the ultimate data and encryption key control and sovereignty, with all the agility the cloud has to offer.

Post-Quantum Readiness
Prevent quantum computers from exposing your sensitive data by fortifying or replacing existing encryption algorithms. Fortanix makes it easy to understand your cryptographic security posture across on-prem and multicloud environments.

Confidential Computing
Get the most value even from your most private and mission-critical datasets without risking exposure. Provide proof of operations in a trusted execution environment for compliance purposes.
Comply with Medical Data Regulations
With Fortanix, you get centralized visibility and control over the policies and procedures that keep you compliant with HIPAA and more. Keep comprehensive tamper-proof audit logs to track all activity, including administration, authentication, access, and key operations.

Access Controls
Leverage powerful identity and access management configurations with SSO and MFA for added security.

Global Key Policies
Enforce company-wide encryption key policies with alerts when protocols are outdated or insufficient.

Automatic Attestation
Fortanix handles attestation to continuously assess and validate your systems for security.
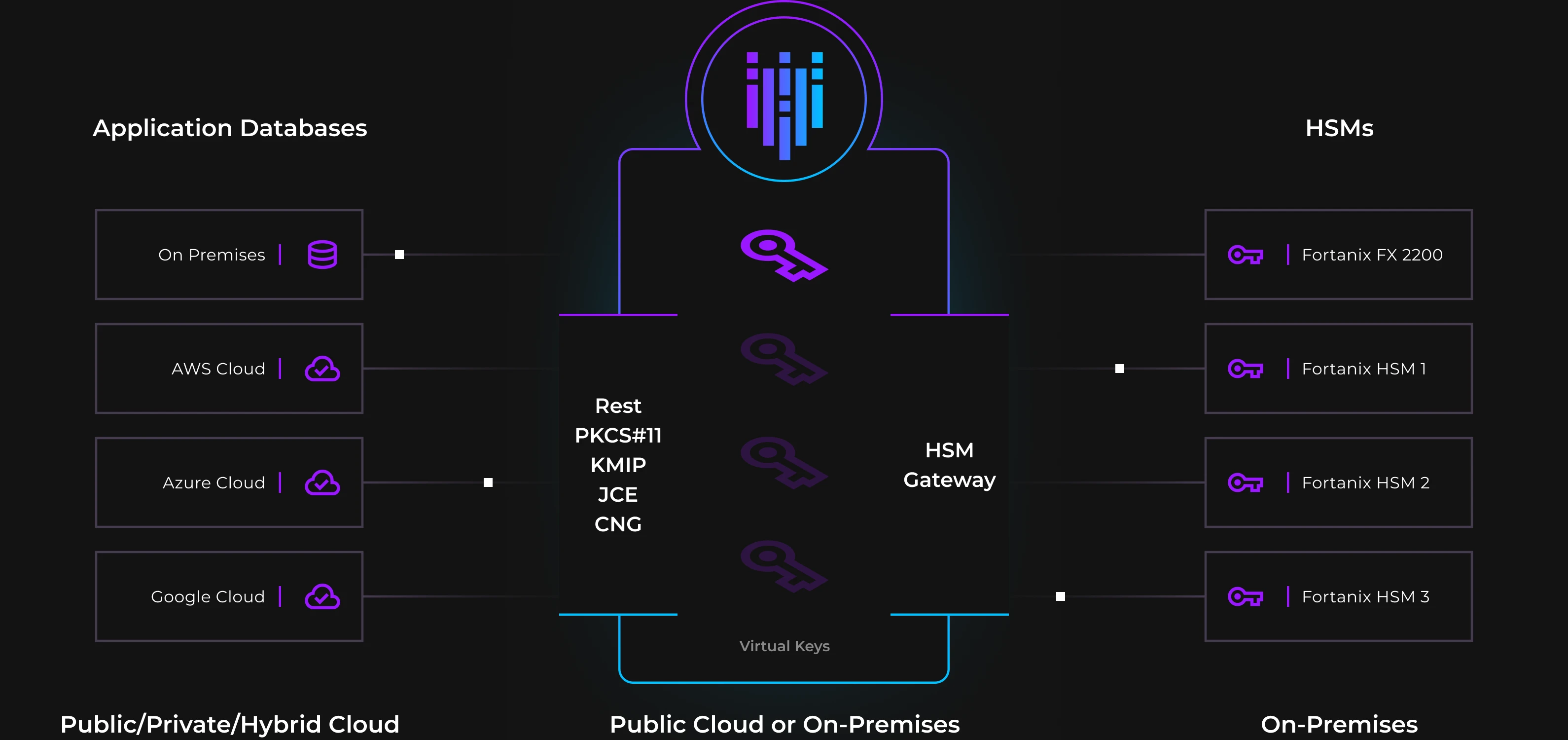
Deploy a Modern Solution You Can Trust
As you strengthen your encryption methods and close gaps in your security posture, store keys and secrets on Fortanix’s scalable, compliant solution. You can even consolidate your legacy HSMs using our secure HSM gateway. All of our appliance is FIPS 140-2 L3 validated and comes with on-prem and SaaS deployment options.
Featured Resource











