VMware
Fortanix Data Security Manager for VMware Sovereign Cloud
Fortanix Data Security Manager delivers data protection and compliance to VMware Sovereign Cloud environments with industry-leading key management capabilities, FIPS 140-2 Level 3 HSM protection, data tokenization, and secrets management via a single unified platform.

Overview
VMWare Sovereign clouds are the unanimous choice amongst businesses looking to run their sensitive and regulated workloads on a secure, compliant national cloud that meets national data residency and data sovereignty requirements. While virtual environments running VMware can readily leverage vSphere VM Encryption or vSAN encryption to protect VMs and data-at-rest—enterprise key management that's both secure and adaptable to a dynamic software-defined infrastructure remains a challenge. Traditional hardware bound HSMs are not flexible enough for software-defined data centres, and software-only key managers fail to match the security level of HSMs.

Fortanix Solution
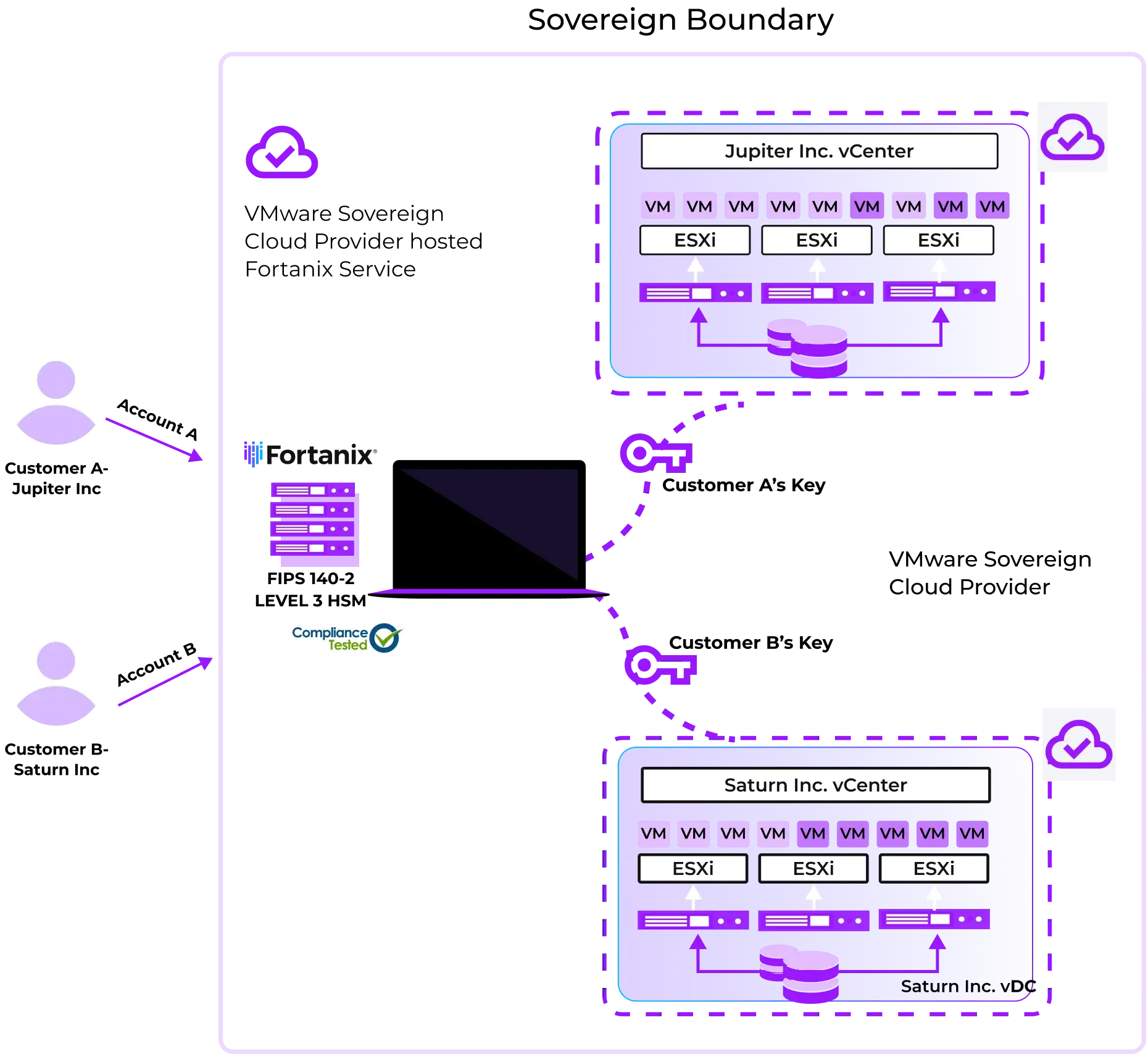
The joint Fortanix and VMware solution delivers scalable data protection and compliance for VMware Sovereign Cloud environments. Fortanix Data Security Manager (DSM) is a unified HSM and key management solution that integrates seamlessly with VMware vSAN and vSphere via KMIP, enabling customers to bring and manage their own encryption keys.
Built with Intel® SGX for hardware-grade security, Fortanix DSM supports multi-tenancy and allows service providers to offer BYOK for VM and vSAN encryption, FIPS 140-2 Level 3 HSM protection, tokenization, and secrets management—all within the VMware Sovereign Cloud boundary.
Benefits

Quick Time to Value
5 Minutes for implementation versus 2-3 weeks with other HSM services.

Greater Control Over the Keys
Control the keys externally, turn the keys off, turn them on when required and get control over data.

Own Your Data and Keys
Using Fortanix DSM, VM encryption keys for are managed and owned by the customers.

Strict Access Control and Quorum Approvals Safeguard Data
Segregation of the key management operations based on roles and permissions ensures control over data.
Meet GDPR and Schrems II Regulations
FIPS certified HSM and key management with regional level isolation helps meet specific data privacy regulations.
Featured Resource
VM and VSAN Encryption Demo
Resources



Press Release











