Overview
In times of relentless cyberattacks and rampant online fraud, data tokenization is a secure and efficient way to protect sensitive data, allowing organizations to minimize impact of data breaches, comply with data laws and regulations, and safely work with data.
Data tokenization, also known as Format-Preserving Encryption (FPE), replaces sensitive data sets like PANs, PHI, and PII with surrogate values called tokens. These tokens retain the same format as the original dataset but have no intrinsic value. This approach preserves data integrity and structure while anonymizing and safeguarding it against unauthorized access.

Fortanix Solution
Fortanix Data Security Manager delivers data security and privacy by means of vaultless, Format Preserving Encryption (FPE) that allows teams to strike a balance between safeguarding sensitive data, complying with regulations, and unlocking data’s potential. With Fortanix, data is tokenized early in the data lifecycle to shift data security left, minimize sensitive data footprint across hybrid, multicloud environments, and ensure data anonymity right from the moment of creation or ingestion.
Fortanix provides Data Tokenization-as-a-Service, with a cloud-scale architecture for better and faster performance and simplifies implementation and management.
Benefits

Fortanix delivers a powerful combination of FPE and RBAC to bolster sensitive data protection. The platform integrates natively with FIPS 140-2 Level 3 compliant HSMs to secure encryption keys for tokenized data, eliminating the need for a centralized token database.

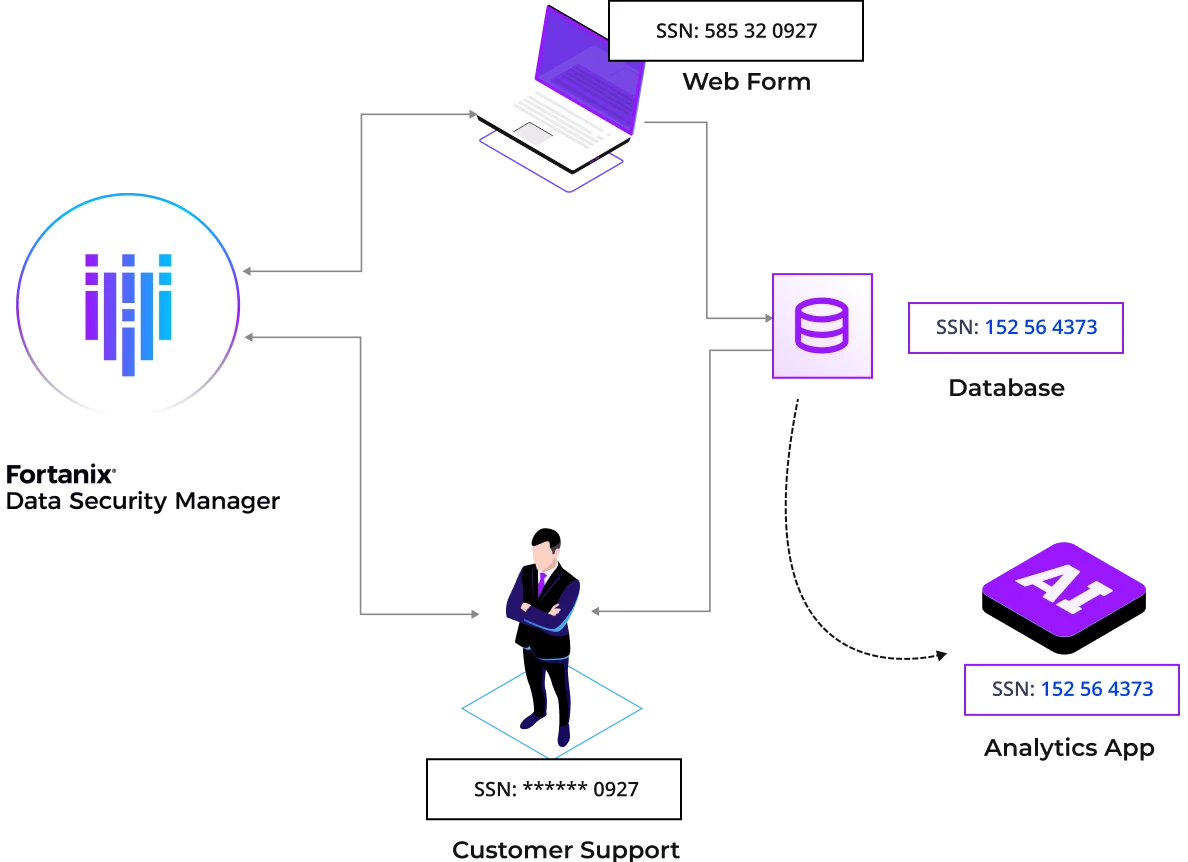
With Fortanix data tokenization, organizations can securely share specific data sets with third parties for analytics or internal customer support staff, all the while keeping sensitive data deidentified, secure, and compliant.

Teams can leverage the Fortanix data tokenization solution to dynamically obfuscate sensitive information, for examples credit card or social security numbers, thus ensuring compliance with PCI-DSS, or electronically protected health information (ePHI) and non-public personal information (NPPI) to adhere to HIPAA regulations.
Key Differentiators
Immediately identify the most important risks, and drill down into the details.

Vaultless Data Tokenization
Fortanix vault-less data tokenization relies on advanced NIST approved cryptographic techniques to generate and manage tokens, eliminating the risk associated with centrally stored sensitive data.

Advanced Data Masking
A user can choose to dynamically mask an entire field of tokenized data or part of the field based on permissions and needs.

Increased Security
Data Tokenization keys are securely stored within the Fortanix FIPS 140-2 Level 3 HSMs, available on premises or as SaaS, with granular RBAC and quorum approvals.
Resources
Here are some of latest news, blogs, resources, events, and more