Fortanix Enclave Development Platform (EDP) is the most secure, battle-tested, and easy to use SDK available to developers for building Intel SGX enclaves. Fortanix EDP is completely open source, fully integrated with the Rust language compiler, and allows native Rust code to be compiled for enclaves without any modification.
Since its launch last year, Fortanix EDP has seen rapid adoption among researchers and ISVs in the Runtime Encryption community building new products and services to enable confidential computing.
When we launched Fortanix Confidential Computing Manager as a SaaS offering running on Azure Confidential Cloud last month, it offered users an easy way to bring their most sensitive applications and data to a confidential computing environment.
Fortanix Confidential Computing Manager transparently converts applications to run inside Intel SGX enclaves using Fortanix Enclave OS, and it offers several services for these applications, such as identity management, data access control, remote attestation, and integrity protection.
Fortanix Confidential Computing Manager provides developers with full lifecycle support for managing their Confidential Computing apps.
Today, we are excited to extend the benefits of Fortanix Confidential Computing Manager to developers who have been using Fortanix EDP to build secure enclaves.
Fortanix EDP is now natively integrated with Fortanix Confidential Computing Manager, and developers can simply add their EDP apps to be managed and orchestrated by Confidential Computing Manager along with other Fortanix EDP or Fortanix Enclave OS apps.
Developers can configure policies for certificate issuance, and whitelisting of enclave images, just like other enclave applications.
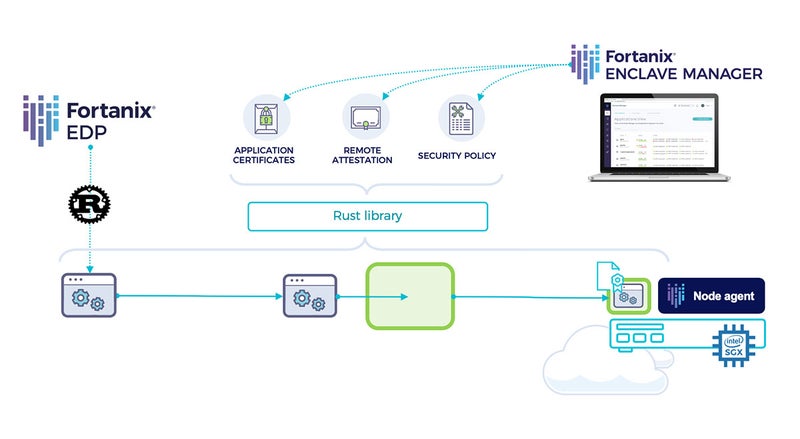
With this integration, when a user launches an EDP enclave application, Fortanix Confidential Computing Manager verifies the remote attestation of the enclave and issues an X.509 certificate to the enclave application based on the policy configuration.
The enclave application can use this certificate to prove its identity to other applications and to create a secure TLS channel between two enclave applications.
A Confidential Computing Manager issued certificate confirms the following for an application enclave:
- The application enclave is a valid Intel SGX enclave and has been verified using Intel SGX remote attestation service.
- The Confidential Computing Manager administrator has approved the enclave image to be used within the Confidential Computing Manager account.
- The Application is running on compute nodes enrolled in the Confidential Computing Manager account.
How it works:
With Fortanix EDP, developers get a secure enclave development platform which is easy to use and compatible with existing application code. We have released an open-source library to simplify Confidential Computing Manager integration with EDP applications.
Using this library, developers can seamlessly integrate their Fortanix EDP application with Fortanix Confidential Computing Manager in their dev and test environment.
- The Fortanix Confidential Computing Manager library allows EDP applications to obtain signed X.509 certificates from Confidential Computing Manager.
- Confidential Computing Manager verifies the attestation of the EDP application and issues a X.509 certificate for an approved domain for the application.
- EDP applications can now use the certificate as server certificates (e.g., web servers, databases, etc.), client certificates or both.
Additionally, we have also made an open source CLI tool along with CURL examples and Confidential Computing Manager UI interface to configure EDP application with Confidential Computing Manager. It is possible to completely automate EDP and EM integration as part your current development pipeline.
How to get started:
- Sign-up on Confidential Computing Manager platform
- To develop confidential Rust Applications
- Refer to the Developer’s Guide for bringing EDP Rust applications to Confidential Computing Manager