At Fortanix we are building a new class of data security solutions called Runtime Encryption®, leveraging Intel® SGX, to protect applications and data in use. We often receive inquiries about the impact of side channel attacks on Intel® SGX and Fortanix solutions.
Many of the queries are inspired by recently published literature identifying side channels that are applicable to Intel® SGX technology. The discovery of Meltdown and Spectre vulnerabilities has further raised the awareness of side channels, which are not always well understood even within the cybersecurity field.
In this blog, we will give an overview of side channel attacks, describe their relevance in the context of Intel® SGX, review key ingredients of an attack and mitigation strategies, as well as highlight defenses used by the Fortanix Runtime Encryption® data security solutions.
Modern era Safecracking
If you watch a lot of heist movies, chances are good that you have encountered a scene with a safe cracker determining the correct combination of a rotary lock using his fingers or using a sensitive listening device.
A side channel attack is like the digital equivalent of a safecracker using a sensitive listening device to determine the state of mechanical components in a lock. In the context of digital systems, side channel attacks extract sensitive information from the system by some means other than the intended input and output channels.
The sensitive information gleaned by a side channel attack is known as side channel leakage. There are many reasons that side channel leakage can exist, including variation in the time taken by the system to process different inputs, variation in the electrical activity of a circuit when processing different inputs, electromagnetic emissions from a circuit, and even sound emitted from a device.
Ubiquity of Side Channels
Side channels can exist in any digital system. The recent discovery of Meltdown and Spectre are a reminder of the ubiquity of side channels. Meltdown and Spectre are side channel vulnerabilities in CPU that can be exploited to allow unauthorized reads of data of running programs.
Side channel attacks are commonly described in the context of cryptographic systems, where the leaked information is a cryptographic key. However, it is important to note that side channel attacks can be associated with leakage of any kind of sensitive information.
Side channel attacks are a very real concern in any digital system that operates on sensitive data. The concern about side channels becomes even more prominent in the context of cloud computing, given the risk they pose for hardware infrastructure shared by co-resident virtual machines or processes.
Anatomy of an Attack and Mitigation Strategies
Several factors that are not always discussed in literature can make it infeasible or extremely difficult to mount a side channel attack in a practical setting. Successful side channel attacks require a perfect storm of key ingredients including access to a shared resource, an application that exhibits externalized behavior that is dependent on sensitive logic, and the ability to measure with precision.
In the presence of measurement noise, the attacker may need to make a larger number of measurements to mount a successful attack, which increases the chance of detection.
Mitigation strategies stem from disabling one or more of the ingredients of an attack. Secure development practices that remove or hide secret-dependent behavior can significantly limit the risk of side channel leakage. Other strategies make the victim sensitive to measurements of side channel leakage and take defensive action based on this detection.
Intel® SGX: With Great Power Comes Great Responsibility
By combining encryption of data in use with attestation, Intel® SGX offers secure computation in an untrusted environment, without exposing the data being operated upon. SGX enables applications to run in a protect execution environment, called an enclave.
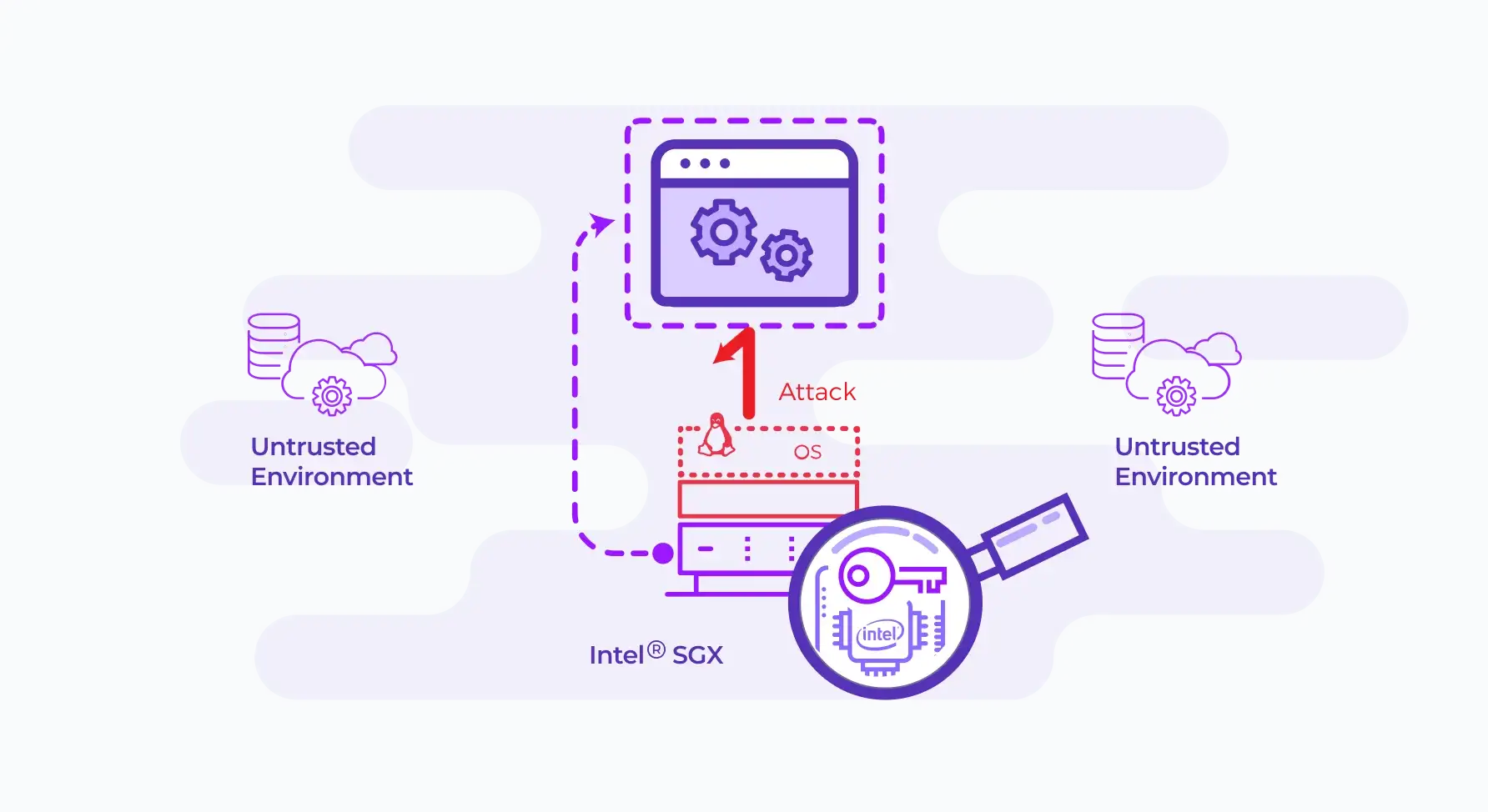
Interest inside channels attacks in the context of SGX arises because many kinds of attacks that are possible in conventional computing environments are no longer possible in SGX, leaving side channel attacks as one of few remaining attack vectors.
Recently published literature identified side channels that are present in the SGX technology, but whether there is information available from the side channel and whether the side channel is accessible to an attacker are properties of each application and deployment, and not of SGX itself.
Fortunately, applications can use countermeasures to control these parameters. To ensure that enclaves are secure in practice, great care is needed in design and implementation of the application, including the care to avoid leaking secrets through side channels.
Fortanix Runtime Encryption® protection
Fortanix leverages its considerable hardware-based security, side-channel, and cryptography expertise to deliver Runtime Encryption® data security solutions that ensure data remains protected even when in use.
Fortanix uses various defenses in its Fortanix DSM™ and Runtime Encryption solutions to protect against side channel attacks. For example, in Fortanix DSM, all cryptographic algorithms are hardened against side channel attacks. When appropriate, non-cryptographic algorithms are also protected. For example, the time to verify passwords is ensured to be independent of the secret.
For a more in-depth look at side channels, applicability to Intel® SGX and the protection offered by Fortanix data security solutions, download our white paper .











