Encrypting your cloud data is not only necessary to prevent attackers from gaining unauthorized access to the data, but depending on the classification of the data, it is also required to comply with data privacy laws such as HIPPA, PCI-DSS and soon GDPR.
One of the challenges of implementing data at rest encryption is the need for robust key management. Solutions dealing with sensitive or high-value data require the use of a Hardware Security Module (HSM). However, when evaluating HSM or Key Management solutions organizations often face trade-offs between security, simplicity, and scale.
Additionally, organizations should encrypt their data in such a way that they, not the cloud provider, maintain control over the encryption keys. These keys should be stored separately from the encrypted data to prevent a single security breach from granting access to both the keys and the encrypted data.
Fortanix DSM delivers unified HSM and Key Management capabilities. Fortanix DSM is built with no compromise security; only authorized users can access the keys. In this blog, we will explore how to create an encrypted block device on public cloud platforms using Fortanix DSM. The procedure is described for Amazon EC2 instance, Microsoft Azure Compute, and Google Compute Engine but it can also apply to other cloud platforms or on-premises data center.
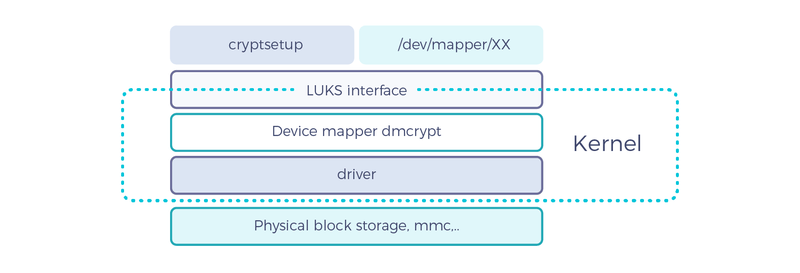
Primer on Linux block device encryption
The standard solution to create an encrypted block device on Linux is to use Linux Unified Key Setup (LUKS), Linux device mapper (dm-crypt) and cryptsetup utilities.
The Linux dm-crypt module provides cryptographic functionality, and LUKS provides secure management of password. cryptsetup is the user space utility to manage and configure them.
The administrator configures LUKS with a passphrase to begin with, and LUKS generates a random master key secured by the passphrase. The administrator secures the passphrase in a key vault, preferably backed by an HSM.
Fortanix solution overview
Fortanix DSM simplifies data-at-rest encryption in cloud computing platforms with a two-step process to deliver HSM grade security for your keys and secrets.
- Import a secret/key in to Fortanix DSM (either via APIs or web interface)
- Create encrypted device using secret export functionality of Fortanix DSM using our rest APIs
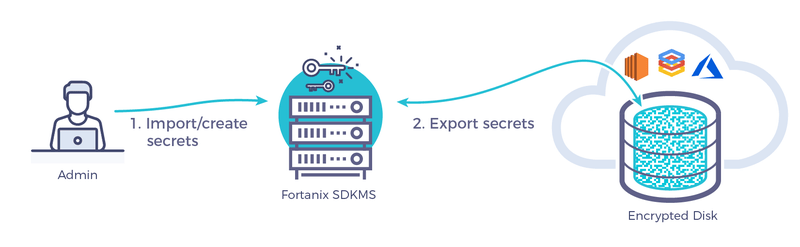
When you import a secret object (password or key) to Fortanix DSM, this secret is protected by Fortanix patented key derivation technology and Intel® SGX hardware security.
Using the Fortanix DSM Web UI, you can define groups to provide applications with granular access control to keys and secrets. All operations on secrets and keys are stored in a centralized tamper-proof audit log.
Our solution demonstrates an encrypted loopback device on a boot volume in the cloud including AWS EC2, Azure Compute and Google Compute Engine. The solution is also applicable to cloud block storage attachments including AWS EBS, Azure Block Storage and Google Persistent Disk. Furthermore the solution is also applicable to any Linux based server in your data center with the required cryptographic modules installed on it as described in the primer.
We provision LUKS with your secret using Fortanix APIs upon compute instance launch or on block storage attachment. You can verify the encryption the key using cryptsetup tool and mount the encrypted block device.
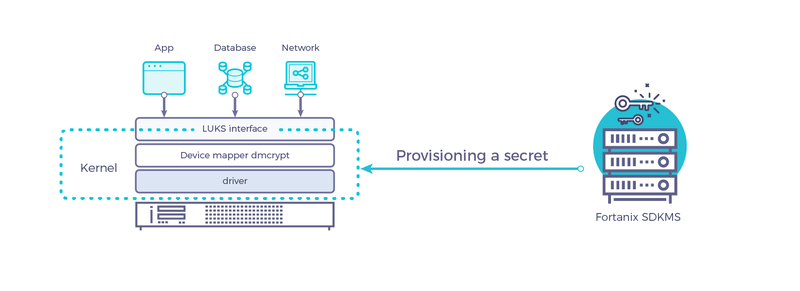
Implementation for block device encryption using Fortanix DSM
Our developer guide provides step-by-step instructions on how to encrypt block device on a Linux instance in your data center or your cloud platform of choice including Amazon AWS, Microsoft Azure and Google Cloud Platform. Review the knowledge base for implementation details.









