In this blog we will describe common application security threats and how Fortanix Runtime Encryption® protects application assets from these threats on untrusted platforms including public cloud.
We will use a 3-tiered application as an example with Nginx as the front-end load balancer tier, Python Flask as the application server tier and MariaDB as the data tier.
An application comes under attack from various threats that target different assets. Each threat actor can use any vulnerability in your application or the underlying platform to get to the target asset.
For example, a malicious insider can use operating system vulnerability to obtain access to your application’s cryptographic keys. In the table below, we describe different threat actors, assets and vulnerabilities that you should consider for your application deployments.
| Actors | Assets | Vulnerabilities |
|
|
|
Fortanix Runtime Encryption® provides unprecedented application security by keeping application memory encrypted throughout the application life cycle using Intel® SGX technology.
With Intel® SGX the operating system, virtual memory manager and other lower layer software and hardware components are outside the trust boundary. Application assets are protected even in the presence of platform vulnerabilities and administrator privilege compromises.
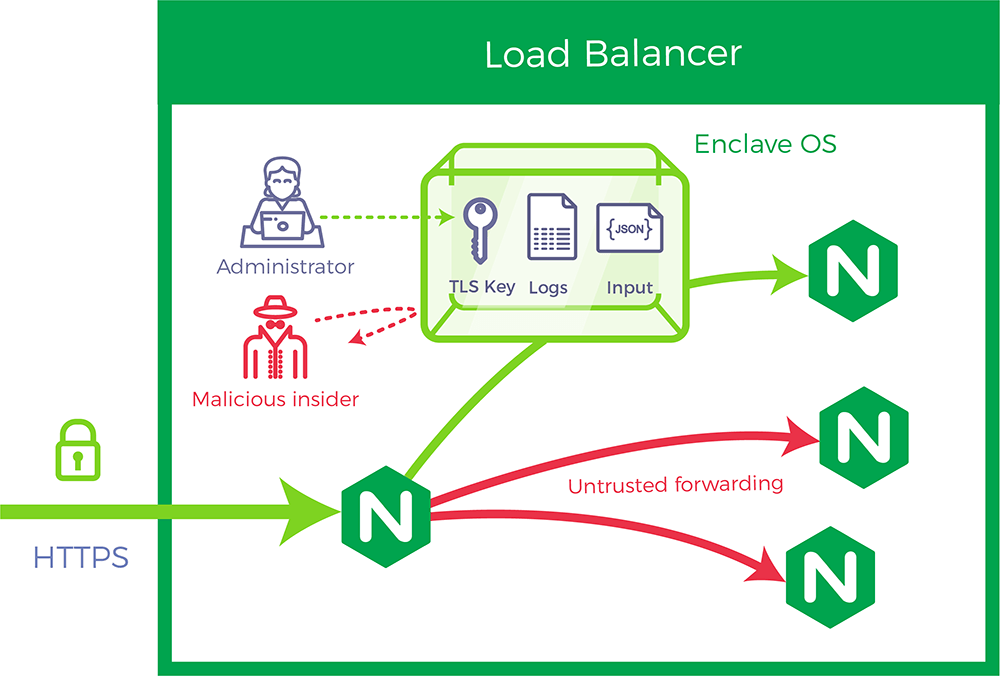
Front Tier: Protect the gate
For a tiered application, an application front-end tier like Nginx serves as a gate keeper and controls input traffic. Many application deployments use the front-end tier for transport layer security (TLS) termination. The TLS keys, user sessions parameters and access controls are some of the critical assets protected by Runtime Encryption®.

| Protected by Fortanix Runtime Encryption® |
|
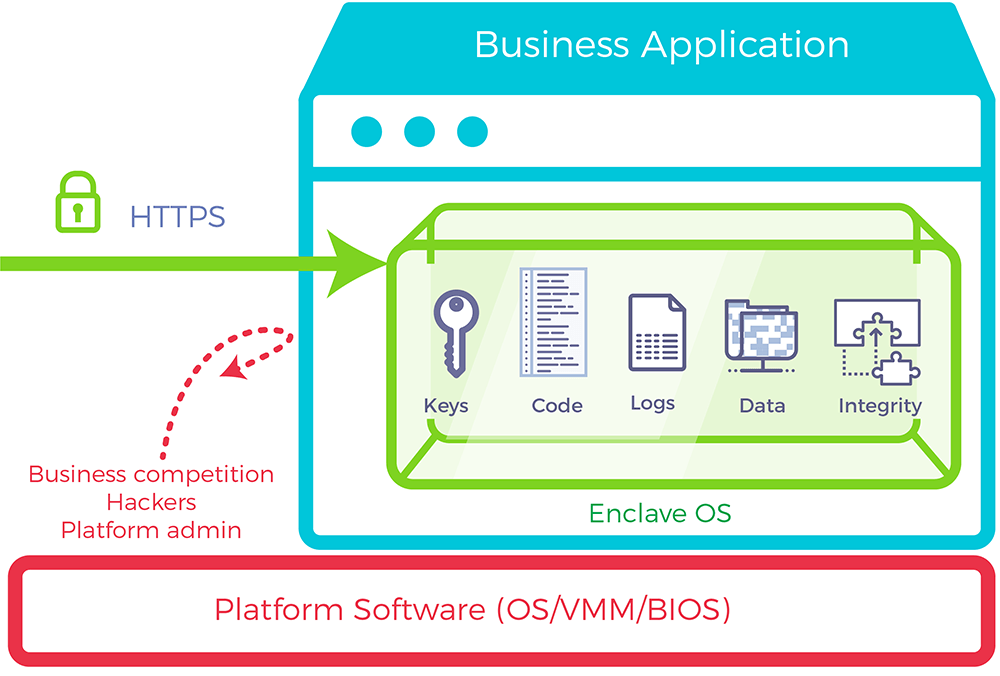
App Tier: Protect business secrets
Application servers like Python Flask in our example runs the business logic. Some of the critical assets managed by this tier are trade secrets, database access keys and application logs.
| Protected by Fortanix Runtime Encryption® |
|
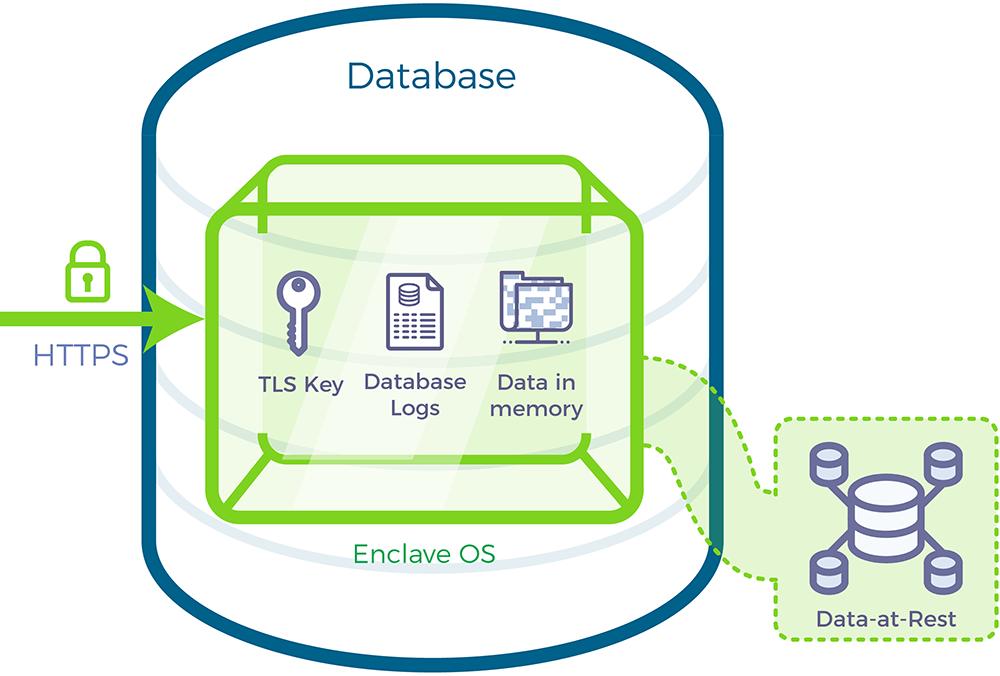
Data Tier: Protecting data-in-use and data-at-rest
Runtime Encryption® protects the data tier by keeping data encrypted in memory and on the disk. Fortanix can keep the database in encrypted storage that is tied to the application signature and application signer identity.
| Protected by Fortanix Runtime Encryption® |
|
Deployment flexibility
Using Runtime Encryption® does not require any application changes or recompilation. Fortanix can convert existing application containers into Intel® SGX capable secured containers to facilitate undisrupted continuous integration and deployment pipelines.
The secured containers are on integrity-protected and encrypted storage, thus removing the possibility of tempering with application binaries and configuration. Application security integrity and confidentiality are enforced by Intel® SGX remote attestation at the application launch.
Fortanix Runtime Encryption® is available on the IBM public cloud and can be deployed on-premises with existing container management platforms such as Kubernetes and OpenShift.