Overview
Benefits

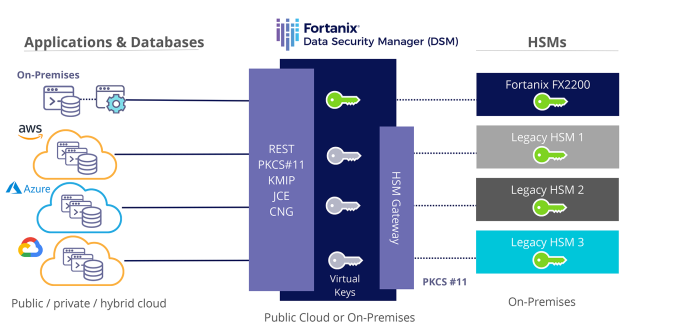
Consolidate HSM infrastructure
Fortanix HSM Gateway connects to the legacy on-prem and cloud HSM already available with organizations and make their keys manageable and accessible through Fortanix. This helps consolidate the HSM infrastructure, reduce cost, and complexity.

Migrate seamlessly to cloud
Fortanix HSM gateway enables businesses to seamlessly move between on-premises and public cloud infrastructures with a single consistent set of cryptographic services and keys.

Simplify cryptographic operations
Fortanix simplifies operations and provides increased control with a “single pane of glass” modern, multi-tenant, and intuitive user interface. All cryptographic operations are logged and audited.