Fortanix Confidential AI
Unlock the power of private data and AI models with Confidential Computing
Fortanix Confidential AI is a new platform for data teams to work with their sensitive data sets and run AI models in confidential compute. Fortanix Confidential AI includes infrastructure, software, and workflow orchestration to create a secure, on-demand work environment for data teams that maintains the privacy compliance required by their organization.
 Talk to our experts for a free assessment of your AI project infrastructure
Talk to our experts for a free assessment of your AI project infrastructureSign Up for Confidential-AI


Why Confidential AI

Furnish proof of execution to meet the most stringent privacy regulations

Get instant project sign-off from security and compliance teams

Trusted vendor with breakthrough security heritage

Put Your Private Data to Work

Protect AI Models Deployed in the Cloud

Easily deploy and provision with a managed service

Furnish proof of execution to meet the most stringent privacy regulations

Get instant project sign-off from security and compliance teams

Trusted vendor with breakthrough security heritage

Put Your Private Data to Work

Protect AI Models Deployed in the Cloud

Easily deploy and provision with a managed service

Furnish proof of execution to meet the most stringent privacy regulations

Get instant project sign-off from security and compliance teams

Trusted vendor with breakthrough security heritage

Talk to our experts for a free assessment of your AI project infrastructure
Sign Up for Confidential-AI
How Confidential AI Works?
01
Readily Available And Managed Confidential Infrastructure
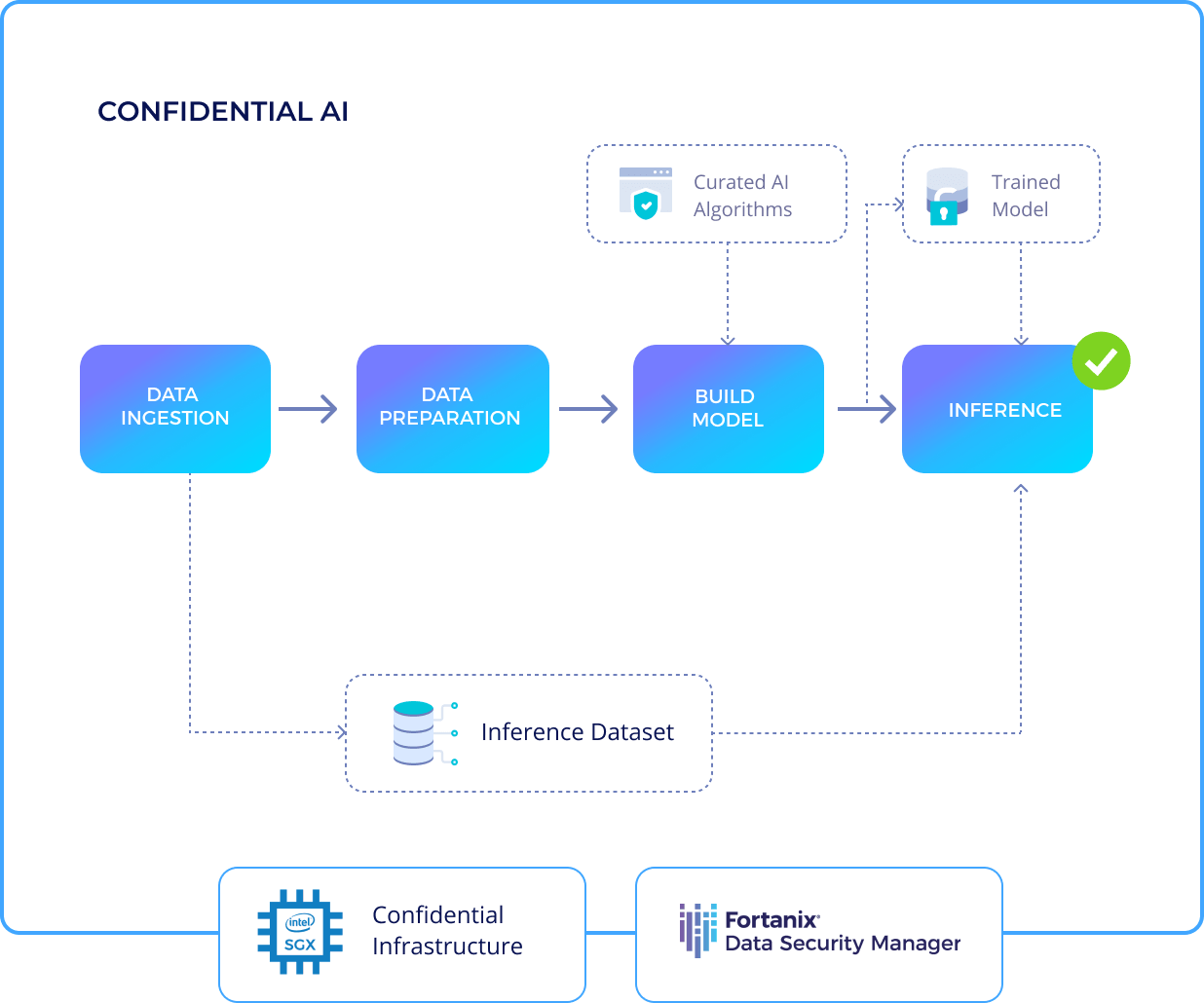
Fortanix C-AI provides a readily available managed Confidential Computing infrastructure that’s easy to deploy and provision. The solution is powered on Intel Ice Lake third-generation scalable Xeon processors.
02
Run AI Models Inside Intel SGX And Other Enclave Technologies

AI models and frameworks are enabled to run inside confidential compute with no visibility for external entities into the algorithms.
03
Hardware-Backed Proof Of Execution And Audit Logging

The solution offers organizations with hardware-backed proofs of execution of confidentiality and data provenance for audit and compliance. Fortanix also provides audit logs to easily verify compliance requirements to support data regulation policies such as GDPR.
04
Support For A Broad Set Of AI/ML Models
AI high performers have standard tool frameworks and development processes in place for developing AI models. Fortanix Confidential-AI supports a range of models such as Yolov 5, Decision Trees, SVM, Linear regression, KNN, etc.
05
Protect Data Across All Stages Of MLOps
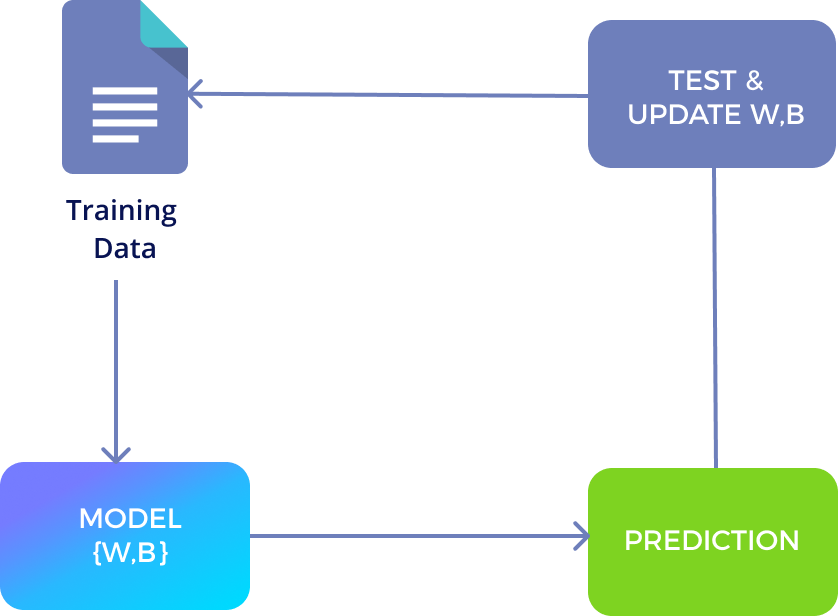
The service provides multiple stages of the data pipeline for an AI project and secures each stage using confidential computing including data ingestion, learning, inference, and fine-tuning.
06
Works On Azure
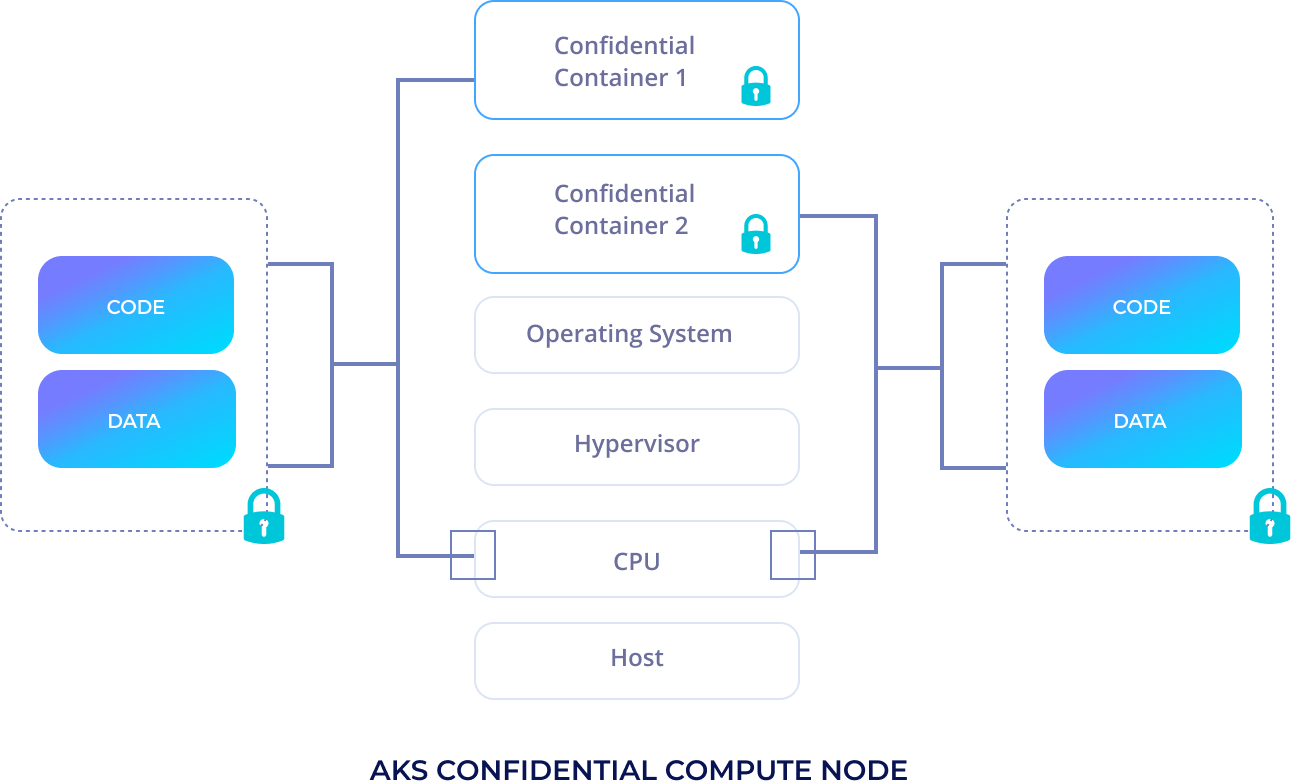
Fortanix managed and deployed infrastructure works on Azure AKS with SGX enabled nodes
07
Dataset Connectors Support Data Ingestion
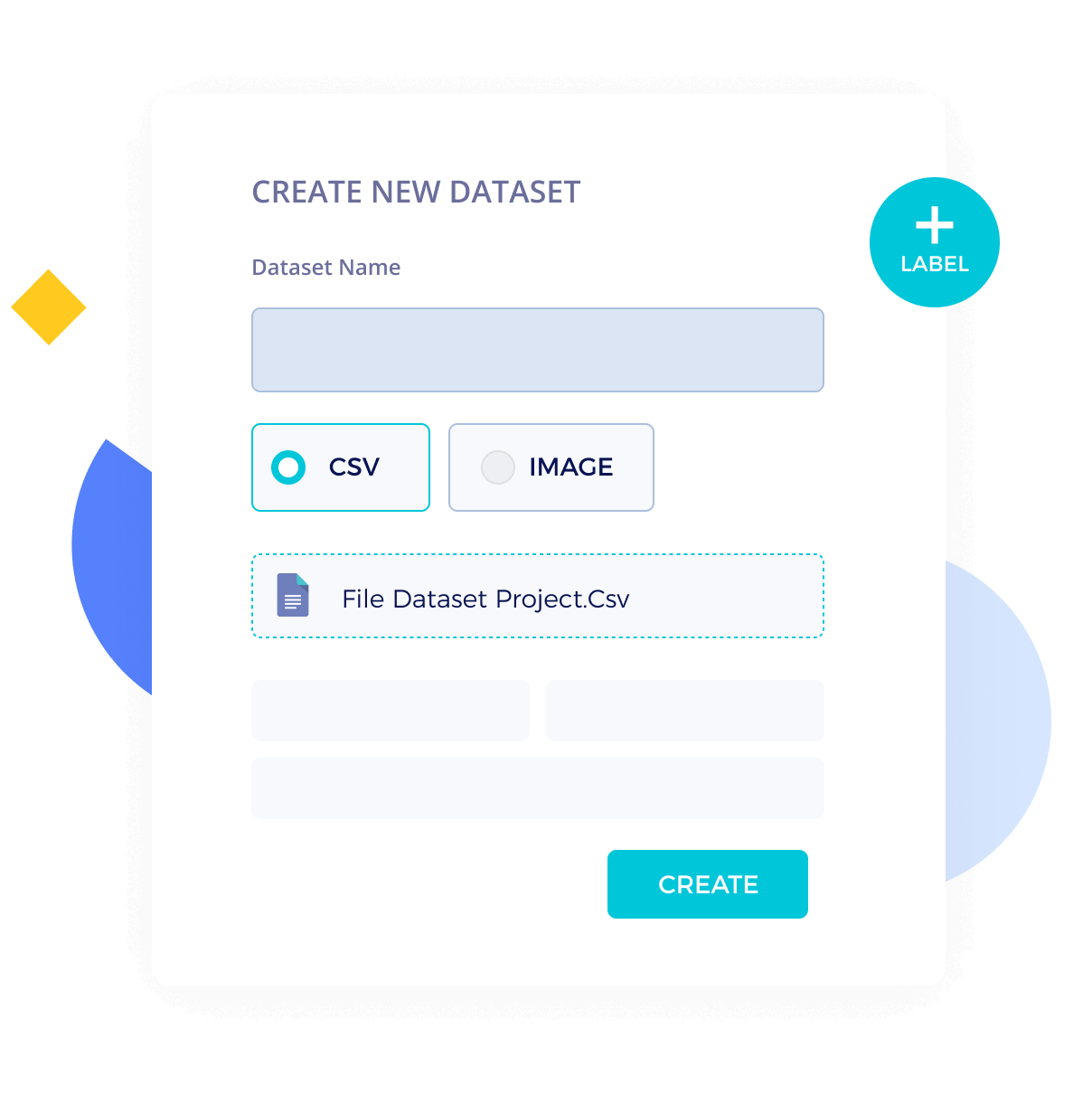
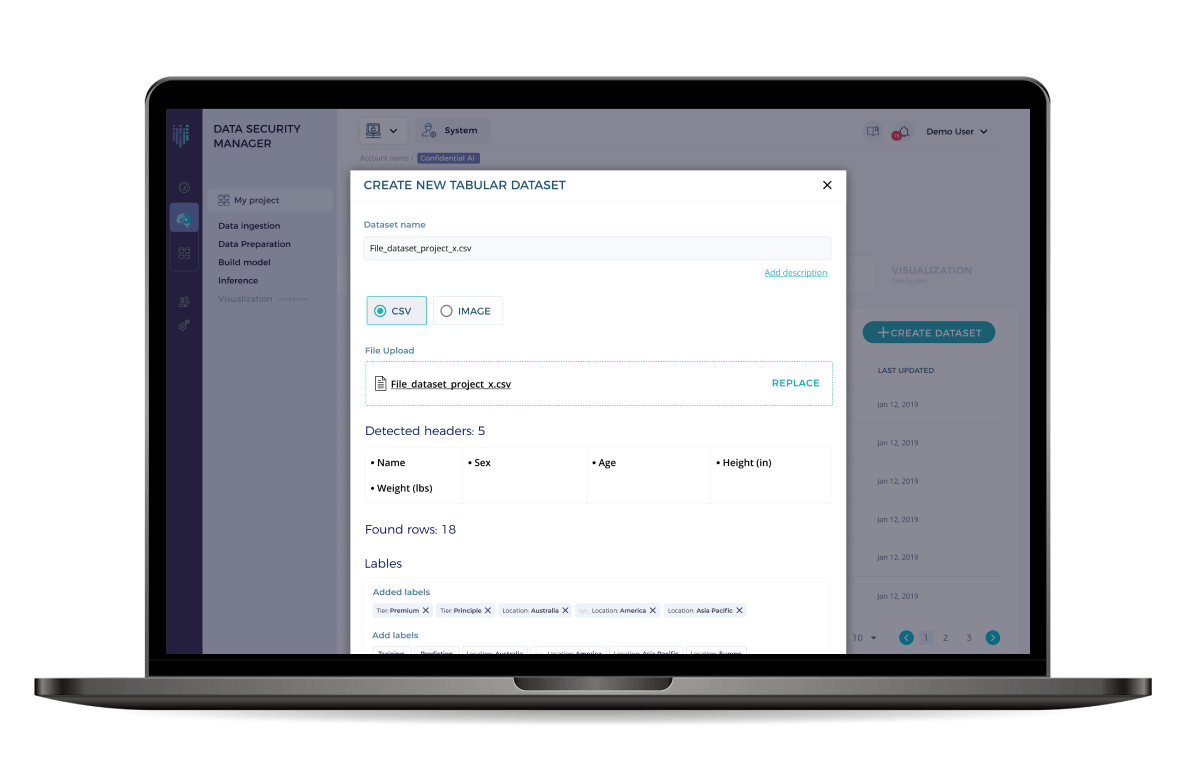
Dataset connectors help bring data from Amazon S3 accounts or allow upload of tabular data from local machine.
04
Support For A Broad Set Of AI/ML Models
AI high performers have standard tool frameworks and development processes in place for developing AI models. Fortanix Confidential-AI supports a range of models such as Yolov 5, Decision Trees, SVM, Linear regression, KNN, etc.
05
Protect Data Across All Stages Of MLOps
The service provides multiple stages of the data pipeline for an AI project and secures each stage using confidential computing including data ingestion, learning, inference, and fine-tuning.
06
Works On Azure
Fortanix managed and deployed infrastructure works on Azure AKS with SGX enabled nodes
07
Dataset Connectors Support Data Ingestion
Dataset connectors help bring data from Amazon S3 accounts or allow upload of tabular data from local machine.
01
Readily Available And Managed Confidential Infrastructure
Fortanix C-AI provides a readily available managed Confidential Computing infrastructure that’s easy to deploy and provision. The solution is powered on Intel Ice Lake third-generation scalable Xeon processors.
02
Run AI Models Inside Intel SGX And Other Enclave Technologies
AI models and frameworks are enabled to run inside confidential compute with no visibility for external entities into the algorithms.
03
Hardware-Backed Proof Of Execution And Audit Logging
The solution offers organizations with hardware-backed proofs of execution of confidentiality and data provenance for audit and compliance. Fortanix also provides audit logs to easily verify compliance requirements to support data regulation policies such as GDPR.
04
Support For A Broad Set Of AI/ML Models
AI high performers have standard tool frameworks and development processes in place for developing AI models. Fortanix Confidential-AI supports a range of models such as Yolov 5, Decision Trees, SVM, Linear regression, KNN, etc.
05
Protect Data Across All Stages Of MLOps
The service provides multiple stages of the data pipeline for an AI project and secures each stage using confidential computing including data ingestion, learning, inference, and fine-tuning.
06
Works On Azure
Fortanix managed and deployed infrastructure works on Azure AKS with SGX enabled nodes
07
Dataset Connectors Support Data Ingestion
Dataset connectors help bring data from Amazon S3 accounts or allow upload of tabular data from local machine.
01
Readily Available And Managed Confidential Infrastructure
Fortanix C-AI provides a readily available managed Confidential Computing infrastructure that’s easy to deploy and provision. The solution is powered on Intel Ice Lake third-generation scalable Xeon processors.
02
Run AI Models Inside Intel SGX And Other Enclave Technologies
AI models and frameworks are enabled to run inside confidential compute with no visibility for external entities into the algorithms.
03
Hardware-Backed Proof Of Execution And Audit Logging
The solution offers organizations with hardware-backed proofs of execution of confidentiality and data provenance for audit and compliance. Fortanix also provides audit logs to easily verify compliance requirements to support data regulation policies such as GDPR.
04
Support For A Broad Set Of AI/ML Models
AI high performers have standard tool frameworks and development processes in place for developing AI models. Fortanix Confidential-AI supports a range of models such as Yolov 5, Decision Trees, SVM, Linear regression, KNN, etc.
05
Protect Data Across All Stages Of MLOps
The service provides multiple stages of the data pipeline for an AI project and secures each stage using confidential computing including data ingestion, learning, inference, and fine-tuning.
06
Works On Azure
Fortanix managed and deployed infrastructure works on Azure AKS with SGX enabled nodes
07
Dataset Connectors Support Data Ingestion
Dataset connectors help bring data from Amazon S3 accounts or allow upload of tabular data from local machine.















We cover use cases across industries.
Here’s a snapshot.
 Healthcare
Healthcare
- Speech analytics and sentiment analysis to provide better tele-customer service in healthcare
- Fraud claim detection for health insurance
- Diagnosing medical conditions in radiology images
- Disease prediction using historical medical data
 Banking
Banking
- Abnormalities and trend analysis within financial planning
- Capital market trends and mood analysis
- Fraud detection with ML
 Insurance
Insurance
- Churn prediction for customers at risk
- Forecasting of claims and triage analytics
- Underwriting and other automatic workflows
 Retail
Retail
- Purchase pattern analysis and targeted marketing
- Predictive purchase analysis using customer profile data

Talk to our experts for a free assessment of your AI project infrastructure.
START YOUR FREE TRIAL