The DSM platform helps security, data, risk management, and DevOps teams to work together and simplify cryptographic operations to secure sensitive data. Fortanix takes a data-centric approach to cybersecurity that minimizes expensive data breaches and accelerates regulatory compliance.
Solutions for Zero Trust, Powered by Confidential Computing
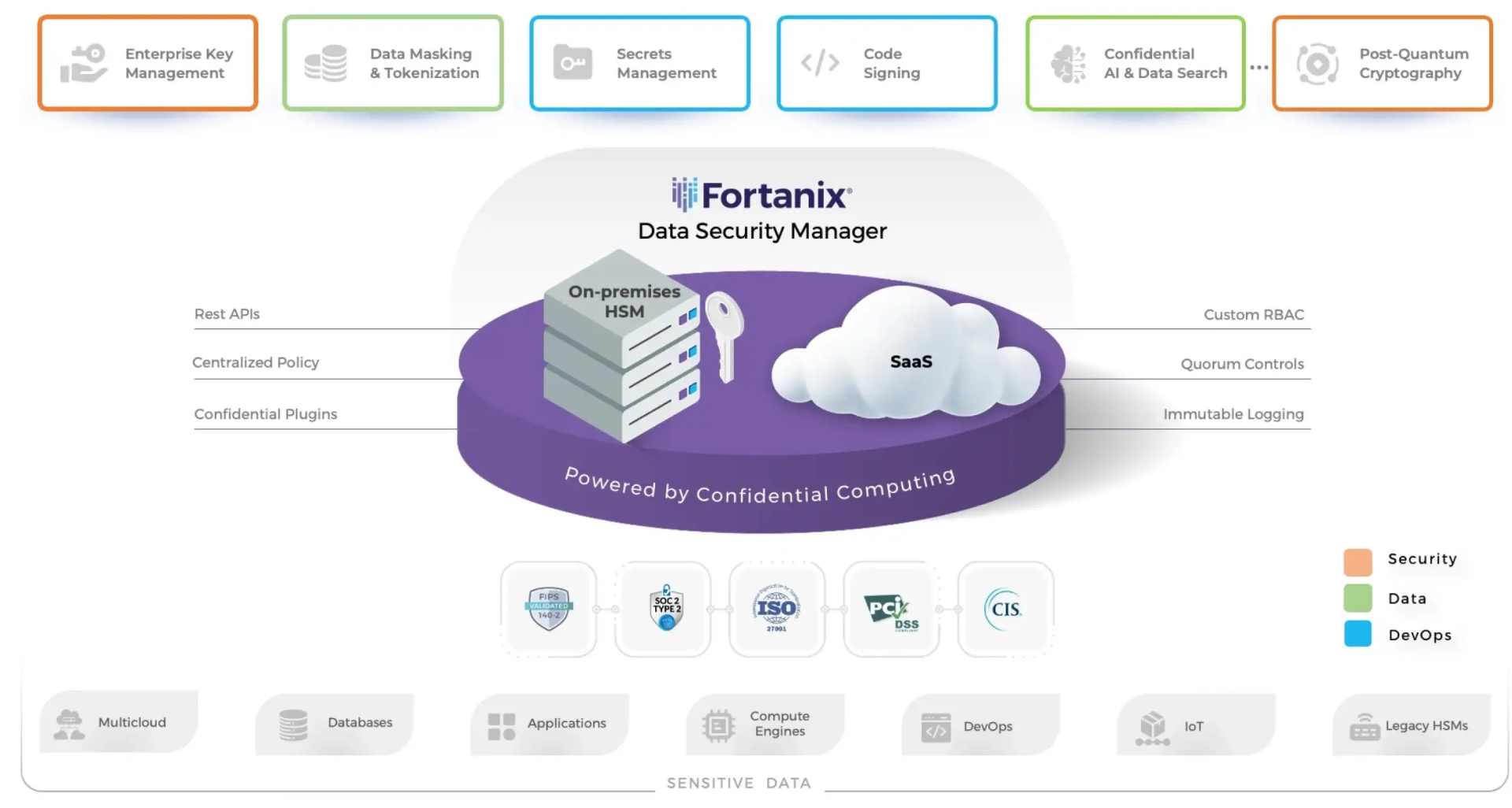
Advanced Solutions to Fortify Security and Accelerate Agility

File System Encryption
Go beyond full disk encryption and protect individual file systems, actively in-use on a designated host.

Transparent Database Encryption
Manage cryptographic keys for databases like Oracle, SQL Server, and MongoDB, securing them on FIPS-validated HSMs.

Data Tokenization
Anonymize data while preserving its integrity and structure by tokenizing sensitive data sets like PANs, PHI, and PII.

Key Management Service
Simplify key lifecycle administration across hybrid multicloud environments.

Hardware Security Module
Securely generate, store, and use cryptographic keys and other assets.
The Fortanix Differentiation

Unified Platform
Centralized key management, with natively integrated FIPS 140-2 Level 3 HSM, with visibility, command control, policy enforcement and reporting, empowers data, security and DevOps teams to increase productivity .

Global Multi-Tenant SaaS
Industry-leading SaaS, and innovative security controls combine to deliver performance at scale, and adherence to data sovereignty requirements, all while lowering total cost of ownership

Built on Confidential Computing
Trusted execution environments, powered by Confidential computing, encrypt and secure data whatever its state: at rest, in transit and in use

API-First Architecture
eases integration, and enables automation
Accelerate Business Outcomes

Reduce Risk from Data Breaches

Simplify Compliance with Global Regulations

Reduce Operational Complexity

Reduce Total Cost of Ownership











