Keep Individual Files and Folders Safe
Every day, the news is filled with reports about new data breaches that have led to loss of customer trust, legal consequences, and financial setbacks. Organizations are always looking to bolster the security of their business-critical data. Full disk encryption is no longer deemed as a sufficient practice, and both technology and business leaders want to ensure that individual files or folders, installed on various filesystems, can be accessed only by authorized and privileged users. Filesystem encryption is a proven approach that not only adds an additional level of data security, but also for separation of duties between data owners and system administrators.
The biggest challenge that organizations face when choosing to encrypt individual filesystems is management of the encryption keys. With each filesystem having its own encryption key, key sprawl becomes a reality and can easily get out of hand. How those keys are stored is of paramount importance as well-- encryption keys are attractive targets for hackers. Poorly managed and stored keys increase cyber vulnerabilities and exacerbates the data security challenges organizations face.
Solution
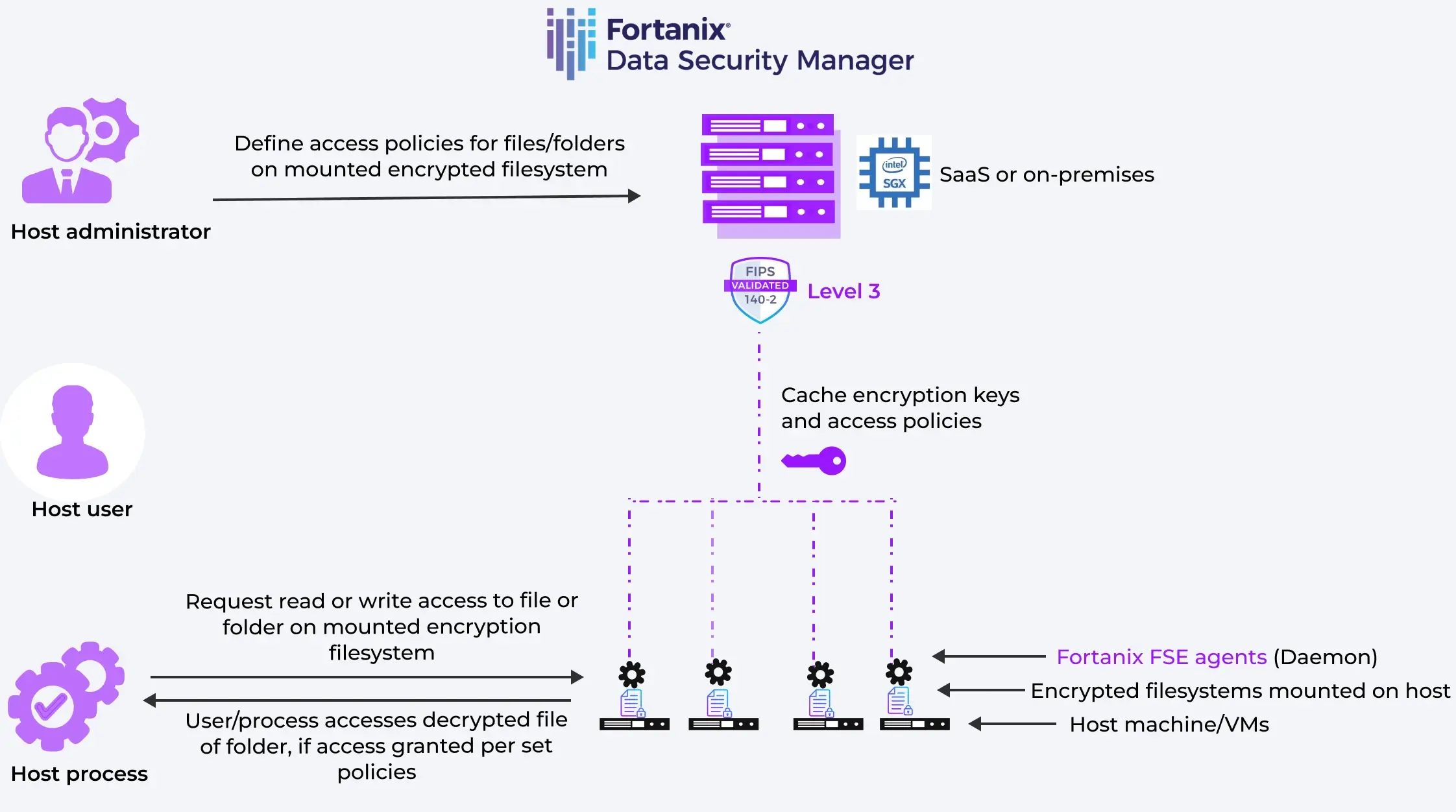
Fortanix Filesystem Encryption allows you to go beyond full disk encryption and protect individual filesystems mounted on a specified host. You now can apply fine-grained access controls and manage encryption keys efficiently at scale to better defend against malicious actors and maintain regulatory compliance.
Key Benefits

Easily Deploy at Scale
Seamlessly set up and manage agents, based on Open Policy Agent specification with no kernel dependencies, to encrypt individual filesystems mounted on host machines. Scale across physical or virtual servers, compatible with Windows, Linux, and Unix platforms, without disrupting workflow.

Prevent Malicious Threats
Enjoy peace of mind with file-level encryption that continuously protects against unauthorized access in physical, virtual, and cloud environments. Apply granular encryption policies to ensure only authorized users and processes can access sensitive data in plain text.

Manage Key Efficiently
Centralize lifecycle management of all encryption keys and apply policies from single pane of glass. Store keys in natively integrated FIPS-140-2 Level 3 HSM, available as SaaS or on-premises. Prevent involuntary or malicious key deletion with Quorum Approvals.
Key Features

Scalable agent deployments, based on Open Policy Agent specification, with no kernel dependencies.

Support for Linux, Microsoft Server, and Microsoft OS.

Central control of and visibility into key management operations with enterprise level access controls and single sign-on support.

Full key lifecycle management to generate, rotate, and delete encryption keys and adhere to security best practices.

Quorum Approvals provide added security measures to prevent accidental key deletion or unauthorized filesystem mounts.

Secure key store in FIPS 140-2 Level 3 HSM, available as SaaS or on-premises.

Fine-grain policy-driven access controls restrict access to plain text data solely to authorized users and processes.

Audit logs for both key management and policy enforcement.











