The Federal government holds vast amounts of mission-critical and highly sensitive data, making departments and agencies prime targets for organized attackers, criminals, or foreign adversaries. With cyber threats looming large, the Federal Government needs to make bold changes and rethink the traditional security perimeters, which are fragmented and ineffective. Agencies need to take a data-first approach to defend the vital institutions essential to the American way of life and to uphold citizens’ trust in effective government.
Mitigate cyber security risk with Fortanix
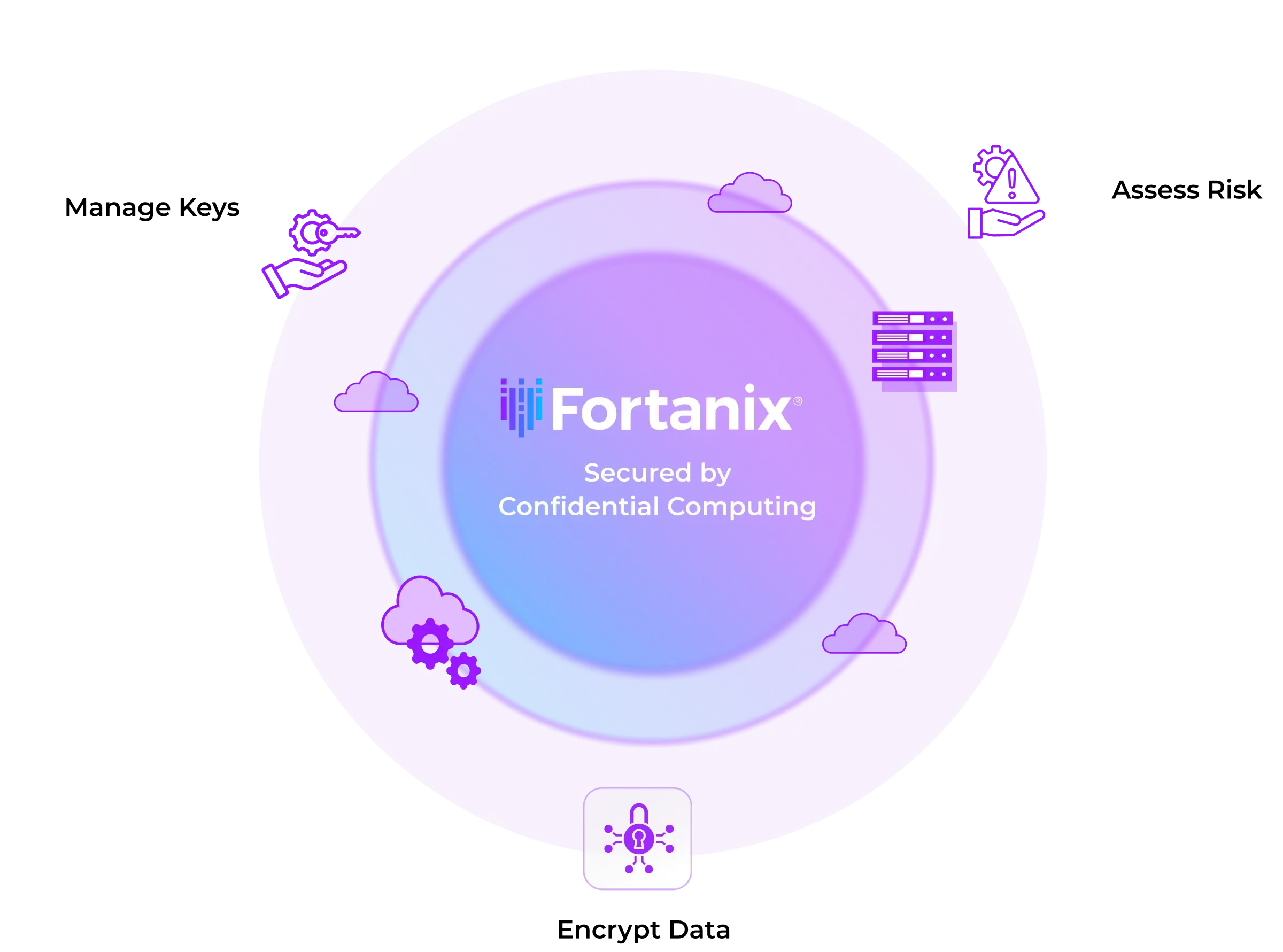
The Fortanix unified data security platform allows civilian, defense, and intelligence agencies to deliver cyber resilience against cyberattacks or malicious insiders. The Fortanix platform is built on confidential computing and brings essential capabilities such as Enterprise Key Management, Data Tokenization, Secrets Management, Post Quantum Cryptography, and others, to secure data in-use, in-transit and at-rest for on-prem, hybrid and cloud environments. With Fortanix, Government agencies now can implement solutions that simplify the data security landscape and reduce complexity across legacy environments and modern, cloud-based technologies to properly and consistently secure data for ultimate, last line of defense.
Drive outcomes with Fortanix

Deliver on Executive Cybersecurity Orders
Secure data across hybrid multicloud with end-to-end encryption and Zero Trust principles.

Prepare for Post-Quantum Cryptography
Take proactive approach to identify vulnerable encryption methods and switch to NIST-approved algorithms.

Eliminate Disparate Key Stores
Centralize key management and leverage policy-driven administration for consistent data security with unified and hardened platform
Capabilities

Full key lifecycle management with natively integrated FIPS 140-2 Level-3 HSM (soon FIPS 140-3 Level-3)

BYOK or BYOKMS for key custody and data access control for SaaS, multi-cloud and data center infrastructure

Policy-driven enforcement across all environments for consistent security and compliance

Quorum Approvals provide added security measures to prevent accidental key deletion or unauthorized filesystem mounts.

Zero Trust controls -Granular Role Based Access Controls, MFA, OTP and Quorum Approvals

Centralized key management with native integrations for all leading DBMS
Rapid update to NIST PQC approved algorithms

Disk, File, and Database encryption for data at-rest, in-transit, and in use

Vaultless Tokenization keeps data portable, private, and compliant

Confidential Computing encrypts data and AI models while in-use











