Rise of Machines: Protecting Your Machine Identities
As businesses transition online in a bid to streamline day-to-day management and operations, there has been an explosion of machines – from physical machines, such as servers and PCs, to mobile devices, applications, cloud instances, containers, microservices, clusters, APIs and smart algorithms.
And all these machines, like humans, have identities that need to be managed.
Research from the non-profit Identity Defined Security Alliance (IDSA) found that 83% of companies saw an increase in the number of identities accessing system resources in the past year.
As organizations continue to chalk out safe and efficient ways of running their services in the new global paradigm, machine identities are slated to grow significantly in the coming years. Getting machine identity management right is pivotal to safe communications—in-turn creating a greater dependency on Public Key Infrastructure (PKI) certificates and cryptographic key pairs.
But given the sheer volume of keys and certificates coupled with shorter lifecycles, managing machine identities manually can turn out to be a slow, error- prone, and highly inefficient process. On the contrary, having a proper strategy and technology solution can mitigate the operational overhead and the overall room for error. Given how these machine identities are often unique to each device—managing them manually is tough feat to achieve. Then there are secrets, tokens, cryptographic keys like SSH, and a slew of other IAM credentials to be managed and secured—often susceptible to expiration, revocation, or mismanagement when managed manually. Automating machine identity management is the only answer.
Fortanix Data Security Manager + Venafi
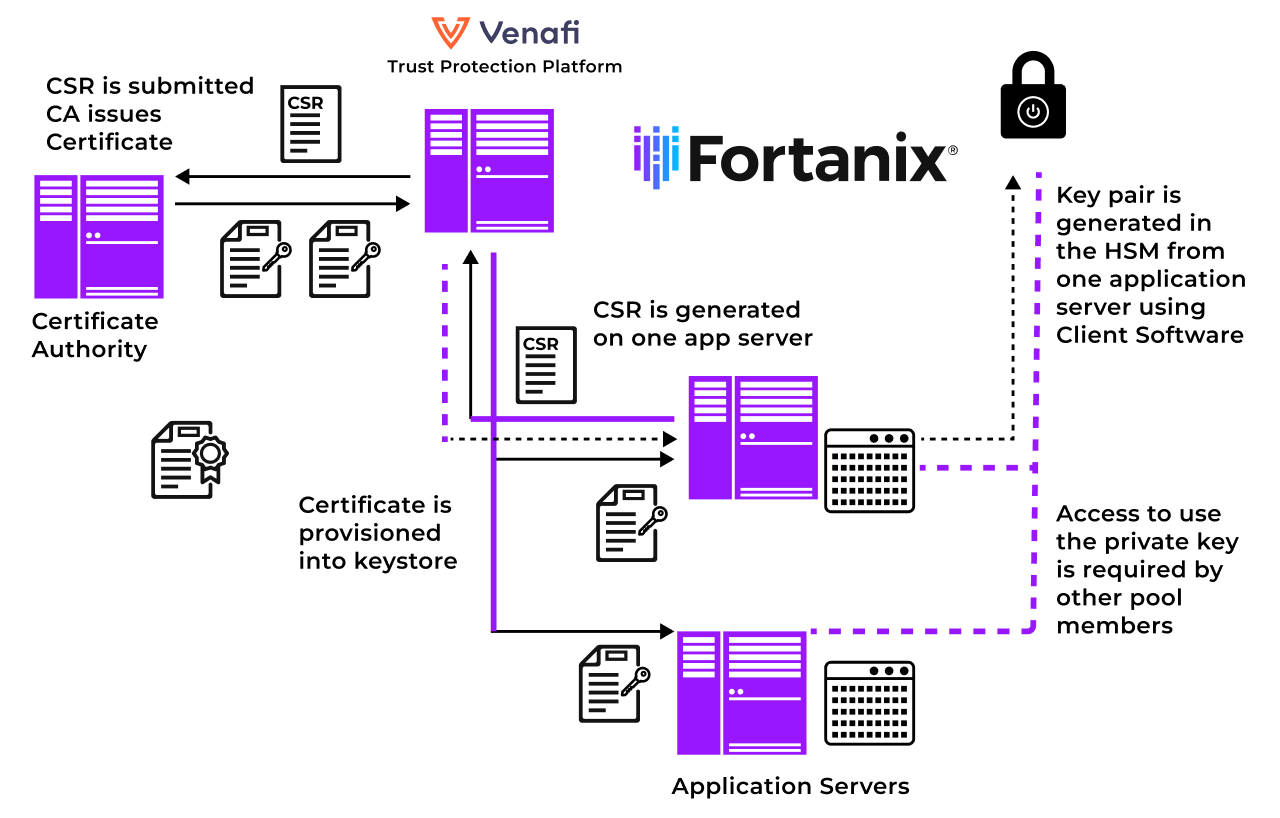
Together, Fortanix and Venafi enable enterprises to overcome the challenges in managing private keys in increasingly complex and hybrid infrastructures. The integrated solution bolsters your organization’s machine identity management programs by automating error-prone mundane tasks—that can potentially expose private keys and derail your overall security posture and application availability.
Users get a package deal that combines automated Public Key Infrastructure (PKI) certificate provisioning, firmware code signing, high-assurance key storage with management of certificate lifecycles —backed by strong data security and compliance assurance. While Venafi acts as the automation and orchestration engine for the lifecycle management of X.509 certificates, Fortanix Data Security Manager ensures the security of the private keys associated with those certificates.
Enterprises get to secure PKI in the cloud and hybrid environments with the Venafi platform, while securing the entire PKI hierarchy in Fortanix SaaS powered HSM—with an option to choose between an on-premises or a cloud-based HSM with Fortanix Data Security Manager SaaS.
Key Capabilities

Option to choose between on-prem or SaaS model of FIPS 140-2 Level 3 certified Fortanix HSM for encrypting and protecting private keys.

Define and enforce high level code signing policies.

Automated multi-vendor X.509 certificate management across multiple devices.

Ability to generate, store and manage hundreds of millions of keys with automation across key lifecycle.

Heterogeneous across development environments.

Complete audit visibility for proof of compliance.

User based access control.
Top Benefits

Multi-cloud Deployment
The Fortanix and Venafi combined solution can be implemented across on-prem, cloud, and hybrid deployments.

Simplified Operations
The joint solution requires minimal setup, minimal expertise to operate, and can integrate with your existing systems.

Lower TCO
Using HSMs/KMS with your PKI will prevent key compromise issues that lead to expensive fines and remediation costs.

High Availability and Security
The joint solution is an HSM-backed PKI management system that is highly available, secure, and has disaster recovery capabilities.

Advanced Automation
With joint solution as the lifecycle management of machine identities, processes like key generation, CSR generation, and certificate installation on end device are fully automated.
Summary
With some of the most business-critical transactions and communications taking place online, ensuring the privacy of these exchanges has become an absolute priority for every enterprise. The digital sprawl, however, is leading to an abundance of private keys to safeguard with little means to do it right.
By leveraging the Venafi platform and the key management capabilities of Fortanix DSM, enterprises can automate their machine identity management while staying on top of their data security game.











