Summary
In an ever-evolving digital landscape, data security is paramount. Fortanix has come up with a new solution of Securing Elasticsearch with Confidential Computing, fortified by Trusted Execution Environment (TEE) technology, stands as a formidable defense against the escalating tide of cyber threats and data breaches.
The power of TEE encrypts, protects, and processes sensitive data in the cloud, maintaining a strong security posture throughout. As organizations embrace the cloud for scalability and efficiency, our solution guarantees a secure transition, preserving the trust and peace of mind that modern enterprises demand.
Problem
Enabling Elasticsearch within a Trusted Execution Environment (TEE) is a cutting-edge solution set to revolutionize data security. Currently, conventional deployments of Elasticsearch lack the inherent protection and confidentiality offered by TEE technology. As a result, organizations face heightened risks related to data breaches, unauthorized access, and compromised privacy, particularly when dealing with sensitive data.
The absence of a TEE-based Elasticsearch solution hampers the ability to confidently manage and query data, impeding the advancement of secure cloud-based, multi-tenant environments. Bridging this gap is imperative to establish a robust data security infrastructure that adheres to compliance requirements and safeguards against evolving cyber threats, enabling seamless and secure Elasticsearch operations.
Solution
The Securing Elasticsearch with Fortanix Confidential Computing Technology provides the ability to host databases in a fortified environment that is impervious to external attacks, ensuring the confidentiality, integrity, and availability of data within it.
With the increasing prevalence of cyber threats and the growing need to protect sensitive information, Trusted Execution Environment (TEE) have become a cornerstone in the quest for heightened digital security, offering a robust shield against malicious actors and enhancing user confidence in the safety of their digital interactions.
Hence, Fortanix Confidential Computing Manager (CCM) comes to the rescue of its customers to protect their sensitive data. Using Fortanix Confidential Computing Manager, our security-conscious users can launch their Elasticsearch cluster with just a few clicks without any hassle in a secured enclave.
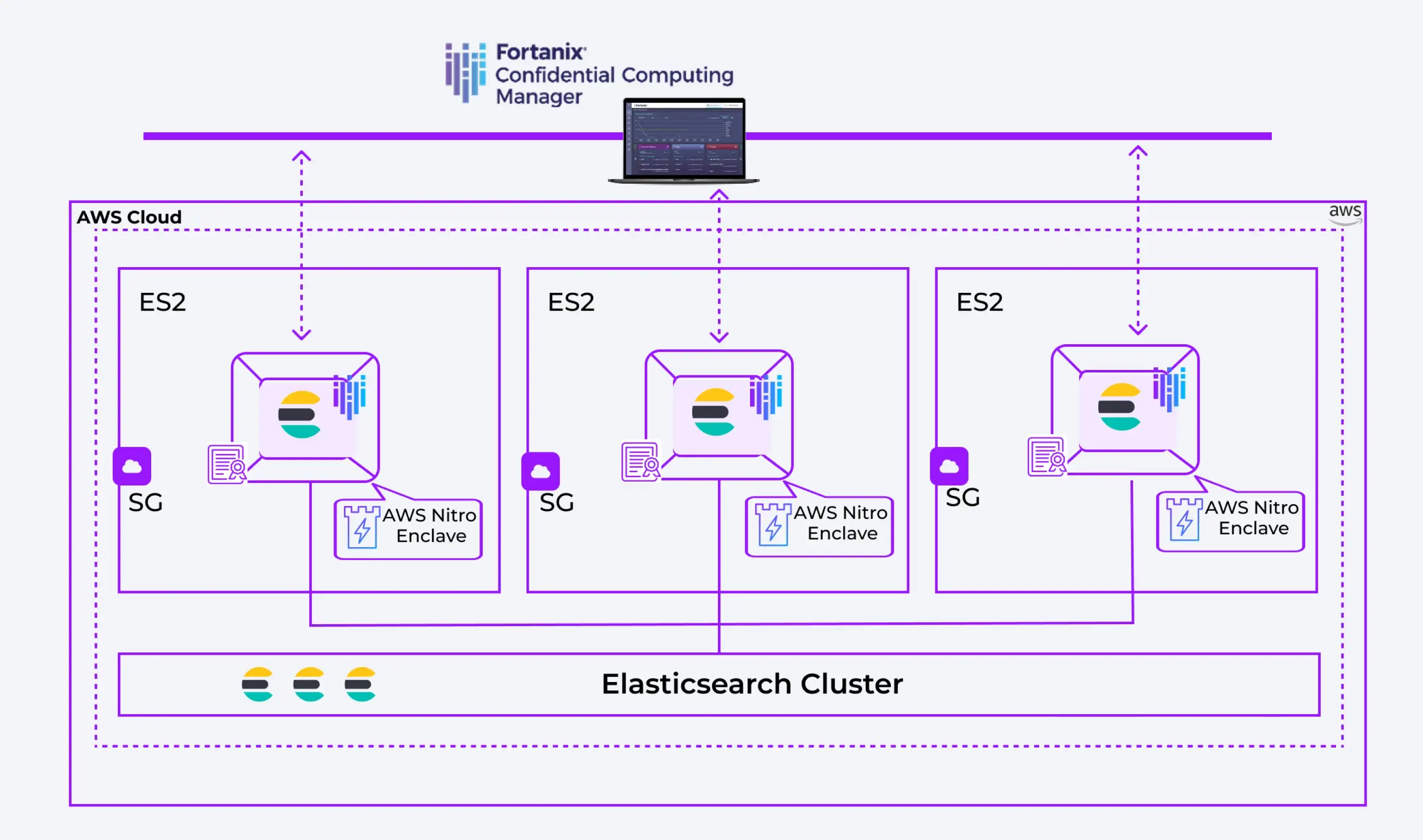
Key Features

Secured Enclaves
Hardware Attestation

Application Attestation
Clustering Support

Effortless Deployment

Secured Data Processing

Persistent Storage
Benefits

Enhanced Security
Ensure the confidentiality and integrity of your data with uncompromising precision, guarded within the fortified walls of a Trusted Execution Environment (TEE), guarding against unauthorized access and data leaks.

Compliance Adherence
Comply with stringent regulatory requirements such as GDPR, HIPAA, and PCI DSS through the sophistication of our security controls, audit trails, and TEE security.

Reduced Risk
Mitigate the risk of data breaches and cyberattacks with sophistication, safeguarding your reputation and business continuity, fortified by the security of a TEE.
Use Cases
Secure Data Warehouses :
Elevate the security of sensitive financial and customer data stored in data warehouses with finesse, fortified by TEE security
Healthcare Database Security :
Meticulously safeguard patient records and medical data from unauthorized access, with the added layer of protection from a TEE.
Financial Institutions :
Ensure the security of financial transactions and customer accounts with sophistication, backed by the security of a TEE.











