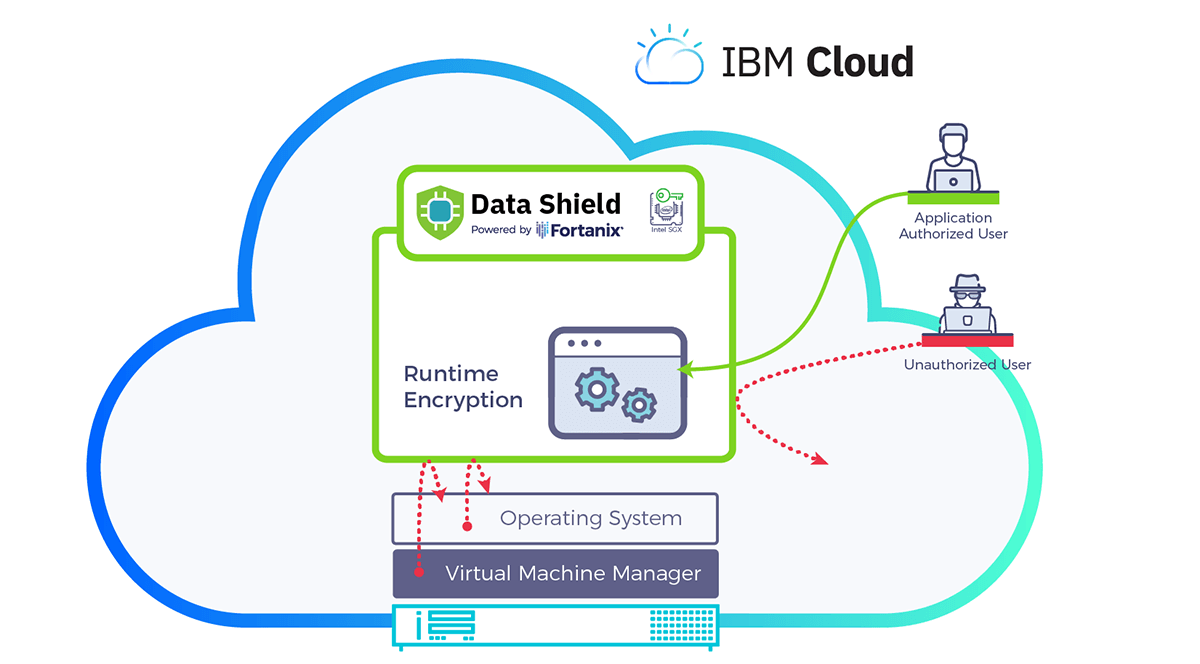
Today, we are taking the next step on our journey to bring Runtime Encryption® to the cloud. Earlier this year, we made early access to Runtime Encryption available in the IBM Cloud.
Since then, we have been working with early access customers to learn more about how Runtime Encryption® can help them tap into the powerful security protections of Intel® SGX.
After incorporating their feedback, we are excited to announce the experimental release of IBM Cloud Data Shield, powered by Runtime Encryption.
Key Takeaways from Initial Customer Engagements
As anticipated, the security and integrity properties of Intel® SGX have resonated well with our early access customers.
The consistent feedback has been that enclave computing is powerful but not always easy. We have also learned that Fortanix® Runtime Encryption® makes it easier.
During our early access phase with IBM Cloud, we engaged with users from organizations of all sizes - large enterprises, startups, and academia - and from across the globe.
The use cases that arose predominantly involve securing data-centric workloads such as Blockchain, AI/Machine Learning, Databases, and Analytics.
We heard from primary users ranging from security architects and application developers to DevOps engineers. Some languages of interest for use with Runtime Encryption® include Rust, Python, Go, and Java.
Early access customers noted that enclave computing has a steep learning curve. Customers confirmed that one of the challenges to operating within enclaves is the need to change, or sometimes rewrite, existing applications.
Because modern cloud applications are highly interconnected microservices, they require extensions to the enclave security primitives.
The Runtime Encryption® platform, which allows users to employ the security of enclave computing, without having to alter their applications, was clearly meeting a need.
The feedback we received from early access customers has helped us clarify the primary objectives of our Runtime Encryption® Platform.
The over-arching objective is to deliver maximum protection of secure enclaves with minimum friction. Specifically, we are focused on enhancing enclave-based computing with the following design goals:
- Zero trust (assume compromised infrastructure)
- Transparent protection (no application modification)
- Seamless DevOps automation
- Secure complete application lifecycle
- Secure complex distributed applications
Enhanced Offering and Partnership with IBM Cloud
We are strengthening our partnership with IBM today with the launch of IBM Cloud Data Shield experimental. IBM Cloud Data Shield, powered by Fortanix Runtime Encryption, offers applications the protection of data in use.
Runtime Encryption® enables a fundamentally new level of security and privacy, allowing organizations with highly sensitive workloads to operate in the cloud.
Organizations can securely run data-centric workloads such as Blockchain and Artificial Intelligence, benefiting from the economies of scale of cloud computing.
With this milestone, we are introducing new and enhanced capabilities to the Runtime Encryption® platform, along with making it more seamless for users of IBM Cloud.
The experimental milestone enables a more self-service consumption model in the IBM Cloud and represents a natural progression for the offering in the IBM Cloud.
The offering delivers SGX as a service end-to-end. It leverages IBM IaaS, which now has SGX-enabled servers in 3 regions and is growing.
It also integrates with IBM Cloud Kubernetes Service, delivering powerful PaaS services for application developers and DevOps.
The Data Shield offering can be easily deployed using Helm Charts in the IBM Cloud. The offering consists of new and enhanced Runtime Encryption® components:
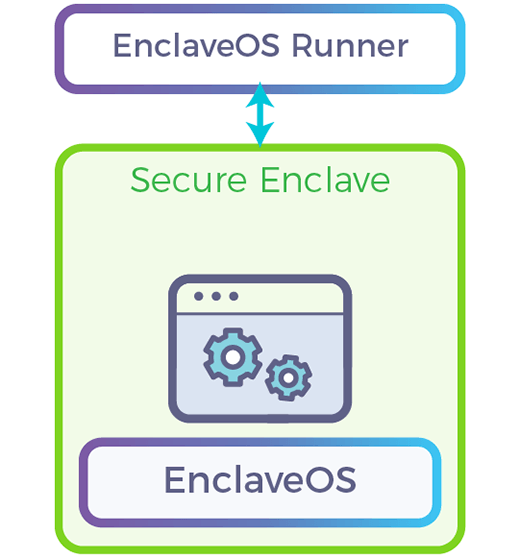
- EnclaveOS™: Hardware abstraction layer that enables unmodified applications to be run securely with Runtime Encryption.
- Confidential Computing Manager™: An orchestration service that allows applications running in enclaves to establish secure communication channels with each other.
- Toolkit/APIs: Enable 1-step protection of containers with CI/CD automation.
Once configured, you have flexible options to protect your applications in the cloud:
- Bring your own App: Bring your Linux Docker containers, and through a 1-step conversion process that does not require any code modification, our solution delivers a protected container. The entire process can be automated with CI/CD integration.
Once protected, you can deploy your applications using standard frameworks such as Kubernetes. - Use protected building blocks: Common services used to create scalable distributed applications are available protected with Runtime Encryption. These include MySQL Database (view demo), NGINX web server, keys and secrets management, and directory servers.
If you are interested in building a new application for SGX but prefer a different language option, then you will be happy to know that we are working on a Rust SDK, contact us for more information on this.
Application Design Patterns that benefit from Runtime Encryption
Over the past several months, we have analyzed multiple application patterns. Some of the common application patterns and use cases that can benefit from Runtime Encryption® in the cloud include:
- Running high value applications on untrusted infrastructure (e.g.: running sensitive workloads in Cloud IaaS, Edge clouds, Private Cloud)
- Secure processing of sensitive information (example use cases: AI, machine learning, secure data analysis apps, secure database processing)
- Balancing trust and transparency with the need for confidentiality and privacy (example use cases: securing Blockchain based apps)
Some of the common application design patterns that we are encountering are:
-
Three tier distributed applications. Each of the three tiers in the commonplace three tier architecture can benefit from the protection of Runtime Encryption.
The frontend tier is sensitive because it sees all the data transferred to or from a client. Runtime Encryption® protects this data as it moves through the frontend server.
Runtime Encryption® also protects the private keys associated with high-value client-facing TLS certificates, thus protecting a critical property of the application’s identity.
The application tier benefits from Runtime Encryption® because it provides protection for both application data in use and for proprietary algorithms operating on the data.
Finally, Runtime Encryption® provides the backend tier with protection for data at or near rest. Unlike some traditional encryption solutions for databases like Transparent Data Encryption (TDE), which only protects data that is fully at rest on persistent storage, Runtime Encryption® also protects data that is cached in memory by the database server.
Three tier applications also benefit from secure communication between enclaves, discussed next.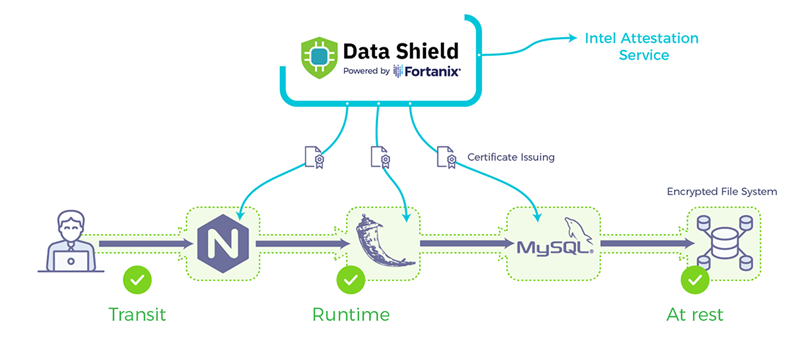
- Secure communication between enclaves. In a multi-tier or microservice architecture, protecting communication between services is critical.
When adopting Runtime Encryption, it is important not only to establish secure channels between services, but also to ensure that each end of a channel verifies that the remote side is running in an enclave.
Enclave Manager facilitates this by verifying enclave attestations as a condition for providing TLS certificates. Applications, in turn, may use various strategies to ensure they only trust enclave certificates. - Secure provisioning of secrets for enclave-based applications. Modern applications require a variety of secrets: TLS private keys, API keys, passwords, and more.
The Runtime Encryption® environment provides a means of managing these secrets so that only enclaves can access the plaintext of a secret. Secrets are provided to an application only after the application has presented a valid SGX attestation.
Getting Started
To protect your application’s data in use with the Fortanix Runtime Encryption® platform in the cloud, get started with IBM Cloud Data Shield. To discuss your requirements with our experts, contact us or join our Runtime Encryption® slack community.

 Cite this article
Cite this article