"I've warmed your milk and made your favorite snack, come on over and unload your sack
Tie those reindeer up, 'Cause you may be a while, And I know what will make you smile."
It's that time of the year. The packages from the Black Friday shopping start floating around, and Christmas presents are sent out to near and dear ones. It's also the time of the year when these packages get mixed up and delivered to the wrong addresses.
While we often worry about what's inside these misplaced packages, have we ever wondered how our personal information on these could be misused?
Now, picture this. You are a school transportation company in the US responsible for dropping students at their designated stops.
In emergencies, you may need to contact their parents or guardians, so you need the bus drivers to have the students' personal information, such as their name, emergency contact, and address. You provide each student with an identification card which the driver scans if he needs to.
While this works like a charm, you must ensure that no third party gets access to these cards. Because if that happens, you as an organization violate the Children's Online Privacy Protection Rule (COPPA).
COPPA allows parents to consent to the operator's collection and internal use of a child's information but prohibits the operator from disclosing that information to third parties.
A very efficient and obvious solution here would be to tokenize the sensitive data. The identification card for each student will now have tokenized data. This way, only an authorized driver with access to the tokenization key can scan this information.
Sounds like a plan.
Fortanix DSM REST API can perform cryptographic operations effectively and securely over the network. But here is the deal. The bus driver is not driving around the town with a laptop connected to a stable network.
They optimistically may have a smartphone and probably only a hand-held device. They also do not have the best connectivity or the luxury of not having access to a student's emergency info because the data won't detokenize when they aren't connected to the internet.
So here we are. In the midst of a shift away from traditional ways of managing keys and performing cryptographic operations.
We introduce you (drumrolls) to Fortanix Data Security Manager Accelerator (DSM-A) as an Android SDK library. The Fortanix Android DSM-A brings the goodness of the core Fortanix DSM-Accelerator to mobile/hand-held devices offering businesses the way to address their cryptography use cases with:
- Reduced network latency
- Maximized throughput
- Offline cryptographic operation for low/no network connectivity, and
- Ease of KMS/HSM integration with android applications
The DSM android archive (a library with a ".aar" extension) helps android application developers integrate easily with Fortanix DSM. It is one in its own class HSM/KMS integration in the android world.
The DSM-A library has a set of functions for authenticating to DSM, exporting and caching keys from DSM, local implementation of the cryptographic operations, etc. The library exposes these functions for android applications to use.
The android application developer needs to include the DSM-A .aar library in the code. This becomes an explicit dependency for their application. Once this dependency is included, the application logic can call the DSM-A functions directly and get the job done.
The following architectural overview depicts the functioning of the Android DSM-A.
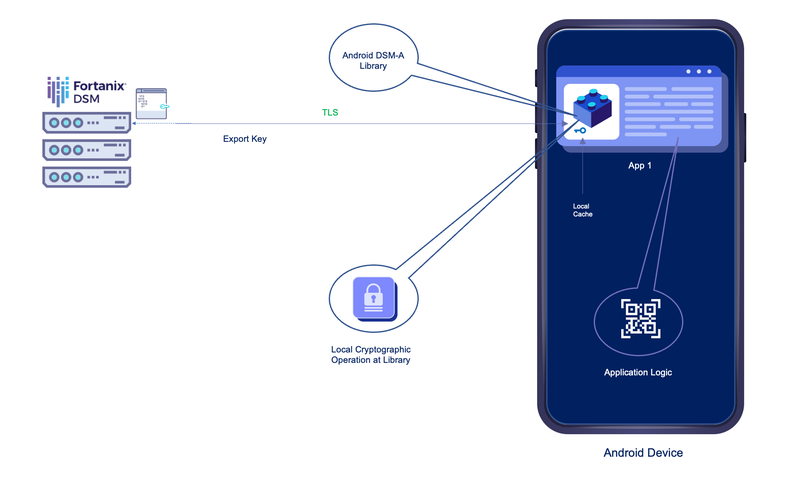
When an application is instantiated, it can check for its local cryptography cache. If it is empty, it fetches the needed subset of keys from DSM and caches them in memory. Once this is done, the application no longer needs connectivity to an external network or DSM.
Cryptographic operations can then be performed locally, catering to a mechanism to work effectively on cryptographic data. The library is a helpful way to create a reusable set of cryptographic operations that need to be integrated through different apps.
Let us look at the following sequence diagram that shows an example of DSM-A with an android application (Let's call it the Scanner App).
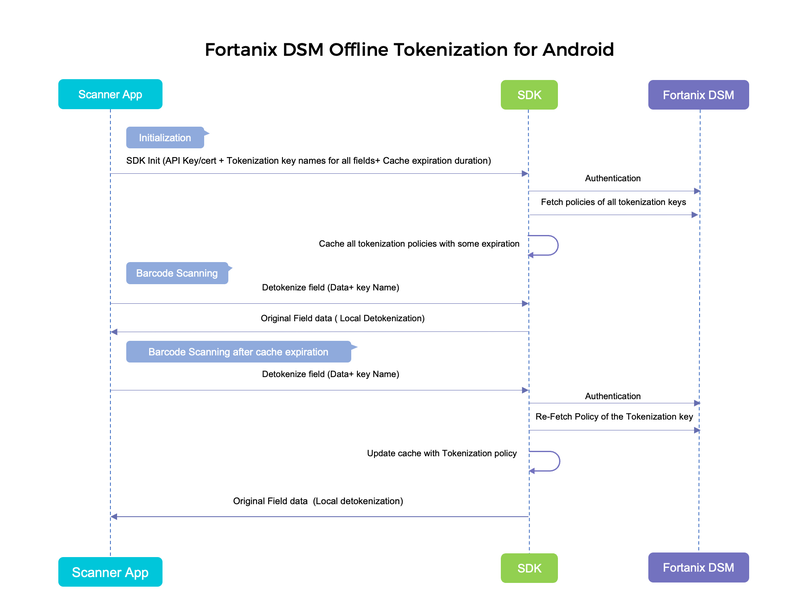
The Scanner App is implemented to scan tokenized data or QR codes and/or detokenize them using DSM security objects to display plaintext data. The Scanner App calls the DSM-A SDK functions to authenticate locally with DSM and cache security objects.
The name of the key and the cache expiration duration should be provided as inputs by the application. The key recaching can be implemented by a set of rules or policies, for example, when a device comes online.
An operator with a hand-held device only needs to synchronize with Fortanix DSM at the start of their shift or when they first have access to the network.
Once the scanner app caches a security object, the application subsequently uses local tokenization or detokenization. This increases efficiency and speed as cryptographic operations happen locally and offline.
If you are an organization that deals with personal information (who doesn't, anyways?), we know that it is a humungous task and a continued challenge for you to ensure compliance with several privacy regulations.
In the EU, the General Data Protection Regulation (GDPR) unifies the data privacy laws requiring all organizations storing or processing the personal data of EU citizens to honor privacy regulations. And while the US does not have a "melting pot" of privacy regulations such as the GDPR, we sure have a "bowl of salad" with different regulations and laws enforced by individual states and industry-based regulatory bodies.
We have the US Privacy Act, COPPA, Gramm-Leach-Bliley Act, and of course! HIPAA. It's a known fact that medical offices invest in HIPAA audits, staff training, and HIPAA-compliant technology. But what about HIPAA-compliant couriers? Medical couriers perform several types of delivery services.
And there are severe consequences if these go wrong. A missing specimen or a lost test result can harm not only patients' health but also the bottom line of the medical facility.
These privacy regulations expand the rights of individuals to control how their personal data is collected and processed and place a range of new obligations on organizations (controllers and processors) to be more accountable for data protection.
At Fortanix, we've pledged to simplify data security while keeping private data precisely what it is - private. With Android DSM-A, we now expand our portfolio to mobile and hand-held devices, going beyond just the customary storing, masking, and aliasing of high-value data.
Isn't this cool? Yes, we know. We are awesome like that. You can be too. By moving to the data security platform that your customers and security teams wish you to pick. If you are here, chances are you already know how to contact us. Come join the party.
And spread the Christmas cheer because, well, it's that time of the year.