Data is at the core of every business decision, from customer insights to AI-driven automation. It flows through analytics engines, machine learning models, operational systems, and external platforms.
But the more data is used and shared, the harder it becomes to protect. Exposure risks increase. Regulatory requirements tighten. And privacy expectations grow.
So how do you balance the need to extract value from data while keeping it secure, private, and compliant?
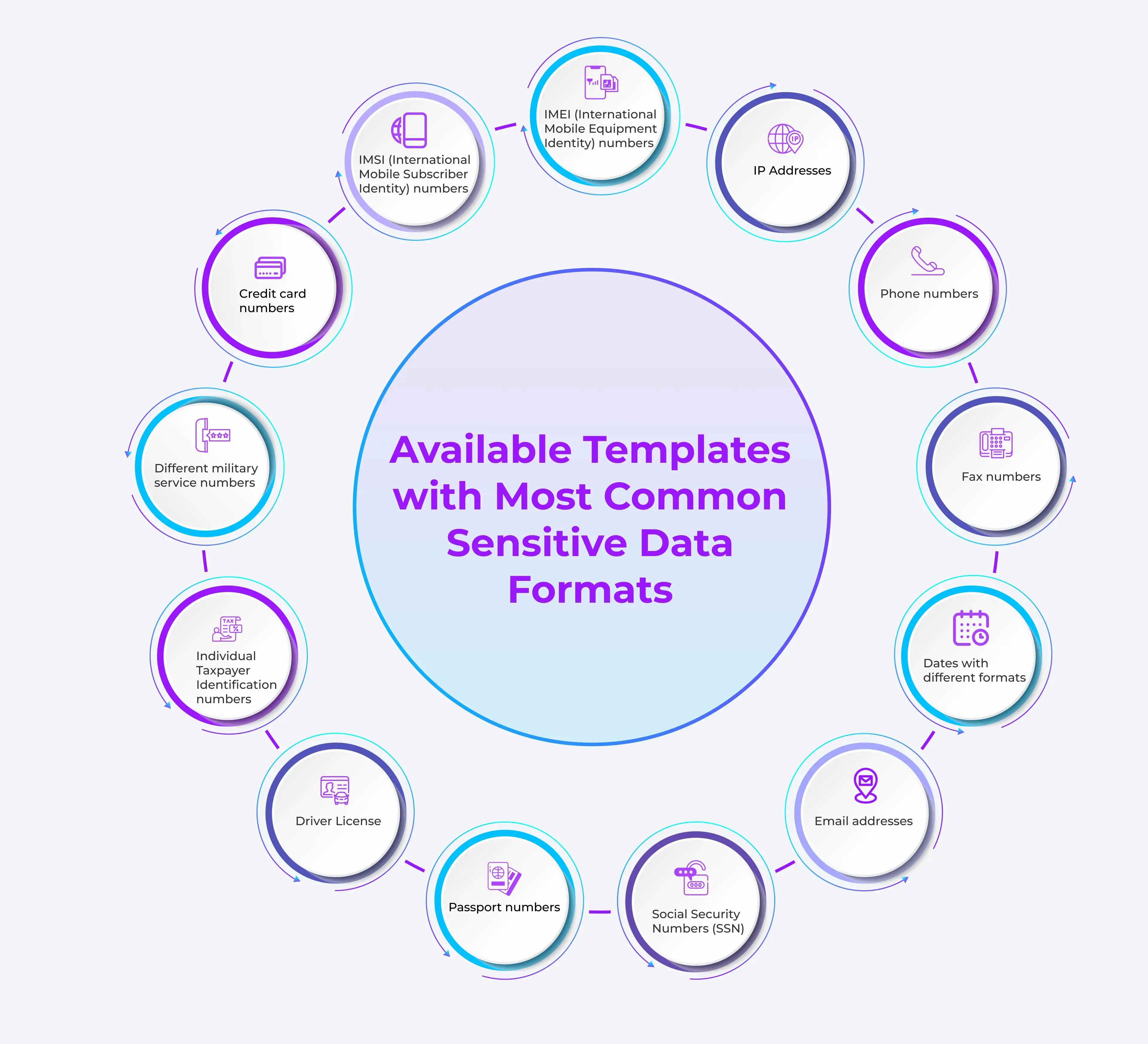
Data Tokenization is a proven way to make this possible. It can protect the sensitive elements such as names, account numbers, national IDs by replacing them with tokens that preserve format and usability. That means your AI models, analytics tools, and applications continue to function as designed, without putting the original data at risk.
What Is Data Tokenization?
Data tokenization replaces sensitive values, like credit card numbers or social security numbers, with non-sensitive but format-consistent tokens. The result looks real (same length, same pattern) but has no connection to the original value.
This mechanism quietly powers secure data sharing across industries. But how tokenization is implemented makes all the difference.
Vaulted tokenization is the older method. It relies on a centralized database or vault to store a mapping between each real value and its token. Every time an application needs to tokenize or detokenize, it has to query this vault. That creates performance bottlenecks, adds architectural complexity, and introduces a tempting target for attackers.
Fortanix uses a vaultless approach powered by Format-Preserving Encryption (FPE). There’s no lookup table, no extra round trips. Tokens are generated in real time using symmetric encryption algorithms that retain the original data format. This means applications don’t break, schemas don’t need rewiring, and the data flows smoothly through your existing pipelines.
Why Fortanix FPE Is the Smarter Choice
Other tokenization solutions often force trade-offs: security vs. usability, performance vs. control. Fortanix FPE removes those compromises.
With Fortanix Format-Preserving Encryption, the token looks just like the real thing. An email still looks like an email. A Social Security number keeps its dashes. A phone number keeps its area code.
This makes it perfect for use cases like database tokenization, where schema compatibility matters. Reports run as usual, dashboards stay intact, and your security team can rest a little easier.
Fortanix applies tokenization at the application layer, before data even hits storage. This "shift-left" approach builds trust into the data itself. Just as the saying goes, “nip it in the bud”, Fortanix helps secure data right at its source.
Data Tokenization Example: Credit Card Transactions at Scale
Consider a large e-commerce company handling millions of transactions every month. Credit card data needs to be processed, stored, and sometimes shared for fraud detection or analytics. Exposing raw card numbers is a legal and ethical minefield.
With Fortanix FPE, each card number is tokenized when it enters the system. The format is preserved, so the payment processor can still validate card types, track transaction patterns, or run statistics without ever touching the real data. This approach supports PCI-DSS compliance without slowing down business operations. That’s data tokenization done at speed and scale.
Benefits of Fortanix Data Tokenization
Keeping Data Functional
The real genius of Fortanix’s tokenization data lies in its balance between protection and performance. Traditional encryption can render data unreadable to every application unless decrypted completely. That’s risky and inefficient.
Fortanix Format-Preserving Encryption offers a better model. It protects data without breaking everything built around it. It doesn’t matter if you are managing tokenization of a database, analytics in the cloud, or mobile apps collecting customer information; FPE works in the background, keeping the operations wheels rolling.
Role-Based Access with Granular Control
Security is adequate when you know who has the key and what they can see. Fortanix integrates granular access controls and quorum approval so that no single admin can unlock sensitive data independently.
Let’s say a help desk agent needs to verify a customer using only the last four digits of their SSN. Fortanix enables partial decryption using configurable masking policies. That way, the agent sees only what they need—nothing more.
Tokenization and Data Residency: Keep It Local, Share It Global
With stricter privacy laws worldwide, tokenization and data residency help organizations meet compliance. According to laws, some data must stay within specific borders, but analytics teams or services using this data may live and operate elsewhere.
Fortanix solves this challenge with its tokenization solution. The sensitive original data stays within its required jurisdiction. The tokenized versions, safely stripped of meaning, can travel freely. This keeps your global operations agile while staying fully compliant.
Fortanix Data Tokenization for the Cloud
In the cloud, data can move between storage buckets, SaaS applications, analytics platforms like Snowflake, and dozens of other services.
Since Fortanix uses Format-Preserving Encryption (FPE), tokenized values keep the original format. That means your analytics tools, databases, and cloud workflows keep running without a hitch. Tokenization happens without breaking schemas or forcing rewrites.
This solution is ideal for modern, distributed cloud systems that rely on consistency and speed.
When scale becomes a concern, as it often does in cloud deployments, Fortanix DSM Accelerator helps. It handles cryptographic operations with low latency, whether you’re tokenizing millions of customer records from cloud apps or securing real-time data from IoT devices.
And if your environment has specific formatting needs, Fortanix supports custom token patterns so tokenized data blends into your system. That makes Fortanix data tokenization a natural fit for the cloud: secure where it counts, flexible where it matters.
Conclusion: When Security Is Built into the Data
Fortanix Format-Preserving Encryption makes data easier to share, analyze, and manage without fear. This is data protection tokenization, where performance and privacy need to work side-by-side.
You're rolling the dice if your data still sits in plaintext or relies on old encryption methods. Connect with our Fortanix team for a demo.
Make your data work harder—and stay safer—with Fortanix FPE. Explore how true format-preserving tokenization can secure your most valuable digital assets, wherever they live. Your data isn’t going to protect itself. Start today.