As a small business owner, what's the first thought that occurs to you when you hear about data breaches?
"Well, that wouldn’t happen to my small-scale operation!" I mean, come on, who'd bother with us when there's a whole platter of customer data, proprietary information, and secret sauces to pilfer from the corporate buffet?"
Is that right?
Not necessarily.
Small companies routinely process vital data such as customer specifics, financial accounts, and personnel records. Many SMBs rely on Google Cloud Platform to store and run their operations. While that provides convenience, it doesn’t guarantee security. That’s where using a cloud key manager like Google Cloud Key Manager, or better yet, a Google External Key Manager, can make a real difference
How Big Attacks Start Small
Given the interconnected nature of today's business ecosystem, data breaches in small businesses can have far-reaching consequences for larger enterprises, too.
Probably that explains why almost 40% of the ongoing cyberattacks [source] are targeted at smaller companies, and how some of the biggest and most talked about breaches of the 21st century traced back their roots to small businesses.
Remember the Target hack from 2013? [source] One which spilt info on as many as 70 million customers of the retail chain giant? Sources close to the investigation disclosed that the attack was carried out via the network of an HVAC contractor that worked with the chain.
Or take the more recent data breach at Wendy's [source], the fast-food chain, where the attackers targeted a small point-of-sale vendor used by Wendy's to deliver malware to Wendy's point-of-sale systems—impacting 18 million payment cards issued by roughly 7,500 credit unions and banks.
Wendy's was sued by both customers and financial institutions, eventually paying $50 million to settle the lawsuits.
Why Hackers Target Small Businesses
Despite not having pockets as deep as their enterprise big brothers, why do SMBs remain a good target for hackers? Here, let me list the top three reasons why.
Low-hanging fruits- Despite the smaller rewards, SMBs are seen as low-hanging fruit due to limited awareness and resources at their disposal – their IT investment is usually less, and security is minimal or average at best.
The data trail: As discussed earlier, small businesses hold a lot of crucial customer data—credit card information, medical records, SSN, bank account credentials, and proprietary business information. Amongst multiple potential misuses, hackers can use these credentials and make fraudulent purchases or sell them to other criminals.
Link to the big fish: Like the Target and Wendy’s attack I quoted earlier, SMBs make a lucrative entry point into bigger enterprises since larger companies presumably are tougher to penetrate.
Storing Data in Google Cloud Isn’t Enough
But I Keep My Data in Google Cloud Platform. That Must be Safe—Yes?
Most businesses mistakenly believe that storing their data with the likes of Google Cloud Platform guarantees security just because— “well…it’s Google”.
I’ll let you in on a little secret.
Google Cloud Platform has notably drawn a line in the sand over how far it will go to monitor and regulate security and compliance on behalf of its end-users. The shared responsibility model of Google Cloud Platform is crafted in a manner that holds the end user responsible for closing the data security loop in their own environments.
Essentially, GCP is responsible for making sure your infrastructure built within its platform is inherently secure and reliable. The customer, meanwhile, controls the data and configurations within that cloud environment.
Hence, customizable cloud capabilities like application management, network configuration, and encryption are the customer’s responsibility—including encrypting data in-transit and at-rest.
Your First Step Towards Enhanced Security: Google External Key Manager
Like most cloud service providers, Google provides options for customers to encrypt data in the Google Cloud Platform (GCP), and most businesses think that is all it takes—but this is where bigger companies take the lead.
You see, core to any encryption strategy is how the encryption keys are managed.
Most businesses make the rookie mistake of keeping their encrypted data and encryption key in the same cloud instance. And God forbid if Murphy’s law strikes and the cloud instance gets compromises—there are high chances of their data being at risk, despite being encrypted.
It’s very similar to locking your door and keeping the keys under the doormat.
Introducing Google External Key Manager
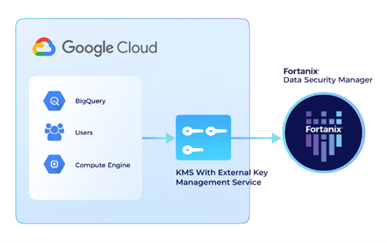
Keeping that in mind, Google has partnered with Fortanix to deliver External Key Management that helps you leverage the full power of trusted, cloud-native collaboration – by ensuring your encryption keys are fully protected and undecipherable even to Google.
Fortanix integrates with Google Cloud Platform (GCP) External Key Manager service to enable organizations to move the data to the cloud and get the same level of security for keys that they're used to in their own on-prem environments.
Encryption keys are always under customer control and stored inside a FIPS 140-2 level 3 certified HSM, away from the cloud. At a click of a button, in real time, enable and disable access to your data from specific instances and locations.
Fortanix integrates with Google external key manager.
Compliance Made Easier with an External Key Manager
Compliance regulations like Schrems II ruling and GDPR also require organizations to have the ability to revoke access to data at any time and store the encryption keys outside the cloud as additional data protection measures. To comply, an External Key Management system or Bring-Your-Own-Key-Management-System (BYOKMS) approach is critical.
Another opportunity where Google External Key Manager shines! You can protect the data at rest by using encryption keys stored and managed by a third-party key management system (KMS) outside the cloud, meet privacy requirements and ensure enhanced security for your cloud data.
Parting Thoughts
It’s evident that hackers don’t just go after a business based on its size, hence any organization entrusted with customer data must take security seriously.
Do you wish to understand what works best for your Data security? Looking to speak to an expert? Our specialists would love to hear you out and assist you.
External Key Control & Management for Google Cloud Platform
Hackers don’t care if you’re a big company or a small one. If you handle valuable data, you're a target. That’s why using tools like the Google External Key Manager makes sense even for small businesses.
With an external key manager, you keep your encryption keys separate from your cloud data. This lowers the chances of everything being exposed at once if something goes wrong. Pairing this with Google Cloud Key Manager or setting up a cloud key manager gives you more control over who can access your information and when.
If you're storing business data in the cloud, using a Google external key manager adds a strong layer of protection. It also helps you meet rules like GDPR, which require you to manage your keys outside the cloud.
Still unsure what setup is right for you? Talk to our team. We’ll walk you through it.











