Problem
Today, most devices are being manufactured in remote or offshore sites that do not have the same level of security standards as the corporate headquarters. Introduction of IoT into manufacturing has also created serious cybersecurity challenges. Cybercriminals now have an opportunity to hack into sensitive information that is stored on the devices manufactured within unsecured environments and introduce counterfeit units causing financial loss and irrevocable damage to the brand’s reputation. Manufacturing organizations are looking to implement advanced security systems that can ensure smarter, secure factory workflows, protect business critical information, and safeguard IP.
Solution Overview
Fortanix offers a unified data security platform that delivers a scalable cloud-native solution to securely generate, store, and use cryptographic keys and certificates, as well as secrets, such as passwords, API keys, tokens, or any blob of data. Secured with Intel® SGX, Fortanix runs the entire key management inside a FIPS 140-2 certified HSM. No one other than the authorized user has access to the keys. The scale-out distributed design ensures that it can scale to also meet the rising demand for PKI fueled by Internet of Things (IoT).
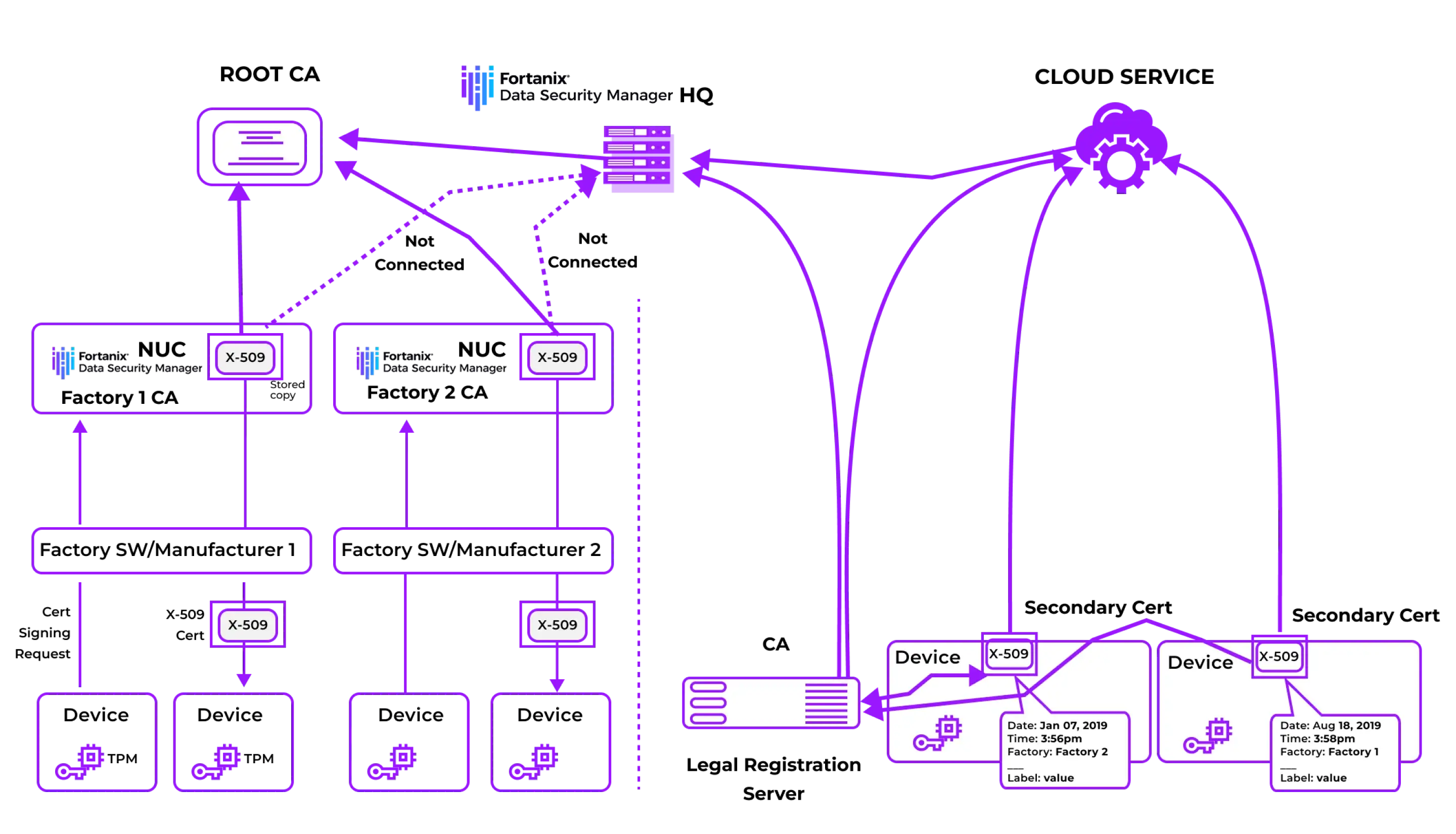
Chain of trust based on the root CA
Fortanix is helping a world leader that is producing and marketing smart home products to secure their IoT devices.
Challenge
The primary challenge was to secure home IoT devices by embedding a certificate at the point of manufacturing.
Solution offered
Fortanix offered a unified Hardware Security Module (HSM) and Key Management Service (KMS) to establish trust throughout the entire device life cycle with unmatched scalability. Fortanix custom integrated with manufacturing systems using plugins. The Runtime Encryption Plugin feature in Fortanix Key Management Service (KMS) allows custom code to run in a trusted execution environment. This allowed the device manufacturer to define policies for usage and access control of keys. These can be enforced by the manufacturer across multiple sites.
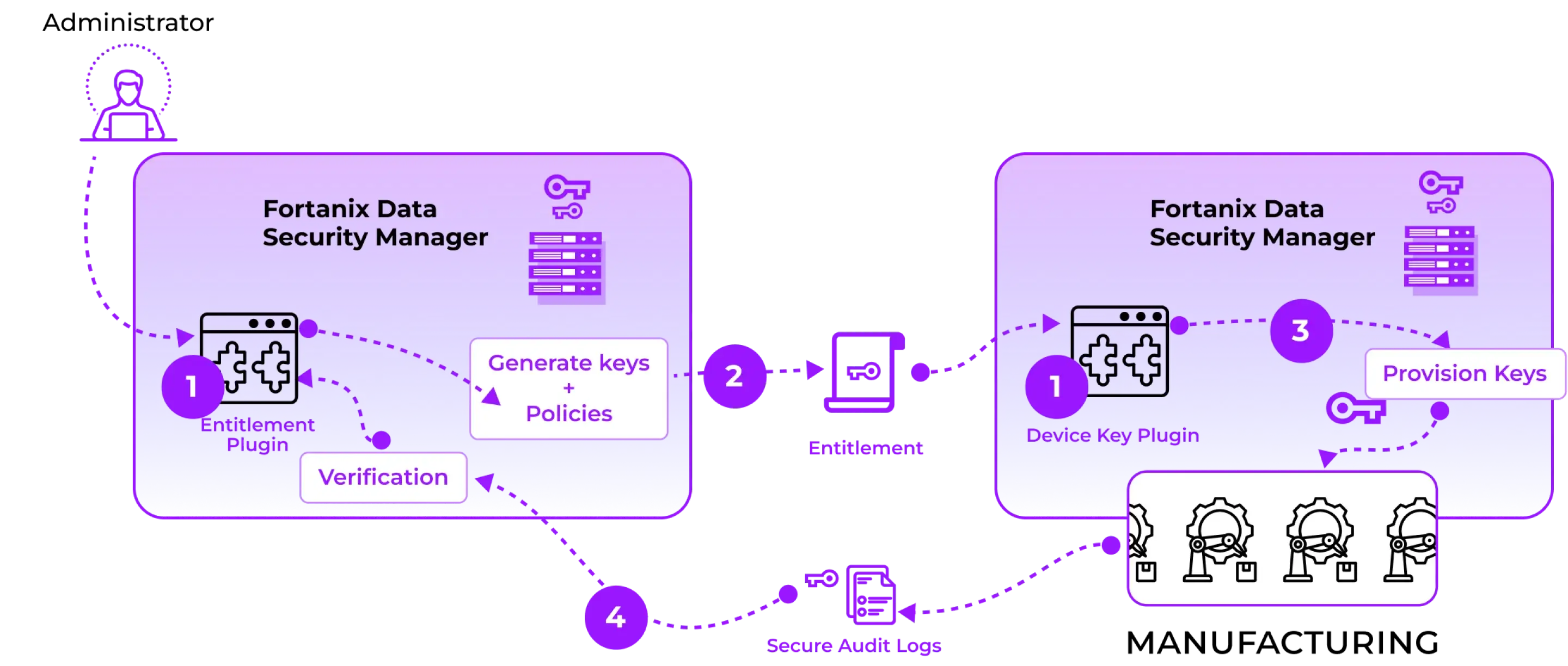
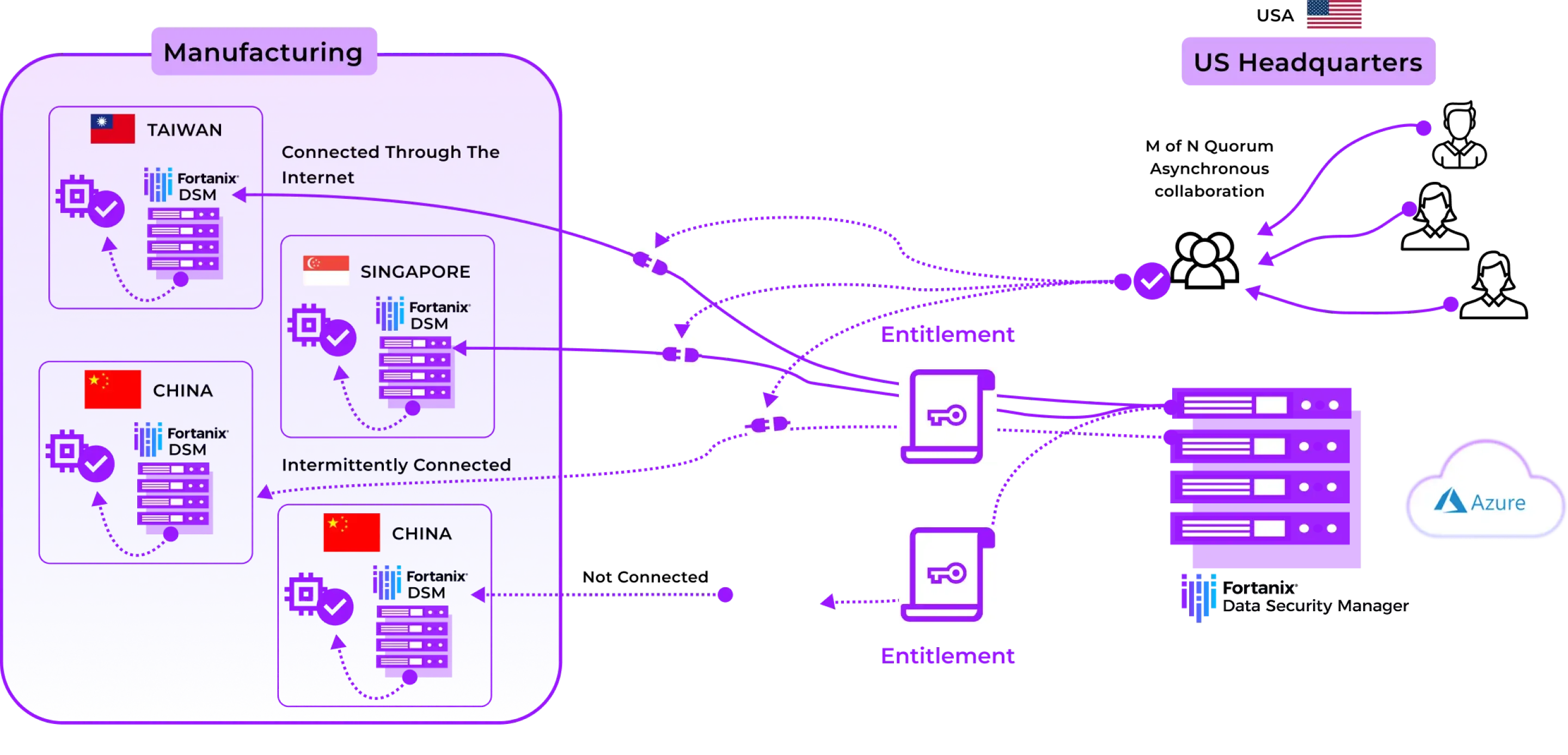
Case Study 2 : Manufacturing and secure deployment of Building systems
Fortanix is helping a market leading smart glass manufacturing company to secure its manufacturing process.
Challenge
The company needed a solution that could help secure its manufacturing process and ensure that the factory certified highquality devices were installed on the customer site (building). The challenge was two pronged: At the manufacturing site, the need was to generate key pairs, store private keys and certificates. And second, they needed to upload these certificates and transmit them to the customer site to verify and authenticate before deploying the factory certified devices.
Solution offered
There are two aspects of the complete solution:
Manufacturing Site
Fortanix Key Management Service (KMS) setup in the factory where devices are manufactured to issue certificates including building controller.
Customer Site
Fortanix KMS setup in customer deployment to verify and authenticate the factory certificate.