Hardware Security Modules (HSMs) solutions have stood the test of time. HSMs are highly efficient in protecting sensitive data and cryptographic keys and meeting security regulations by providing high levels of authentication and tamper-proof systems. As a result, companies mainly rely on HSMs to manage cryptographic needs.
Why Legacy HSMs Matter for Security and Compliance
Traditionally, companies have been using legacy HSM solutions for several reasons. Firstly, when companies want complete control over their keys without depending on the cloud service providers. For example, legacy HSM is a physical black box for managing keys for compliance reasons. Secondly, legacy HSMs are useful when applications have intensive cryptographic operations and are extremely sensitive to latency. In addition, legacy HSMs are also beneficial to companies meeting country-specific compliances. For example, the Root of Trust for PKI (Public Key Infrastructure), CA (Certificate Authority) signing, encrypt/decrypt operations such as AES/HMAS/3Des, etc.
The Scalability and Cost Hurdles of Legacy HSMs
Legacy HSM deployments are difficult to scale and manage because physical partitions limit their scope of operations. This type of architecture is expensive. Legacy HSMs have connection limitations and need large footprints to serve organizations' needs and scale.
Besides, legacy HSMs require a server and database layer that hosts the key management software (typically homegrown or added software costs associated) to interact with HSMs.
Related Read: How Fortanix Displaced Legacy HSMs
Additionally, legacy HSMs need substantial investment in hardware and skilled resources to keep up with this environment. As a result, organizations with legacy HSMs can manage operational volumes only within the given capacity of the deployed HSM.
Cloud-Vendor HSM Solutions Can Have Pitfalls

As organizations move to the cloud infrastructure for scalability, flexibility, and cost-effectiveness, Cloud-vendor HSMs such as AWS, Google, IBM, and Microsoft are gaining popularity. But let us understand why these Cloud-vendor HSM solutions have pitfalls.
1) No Control of Keys: Third-party cloud applications inside a multi-tenant environment access the Cloud-vendor HSMs. Attackers can easily hack applications with poor security and fraudulently access the HSM to get hold of the cryptographic secrets.
Organizations find it challenging to manage the remote access to the Cloud-vendor HSM, especially the remote loading of keys inside the HSMs and their remote administration.
2) No Redundancy: Redundancy means that if a system or component fails, there's a backup available to carry out the operations. Getting individual HSMs to work together in a synchronized, redundant, highly available cluster can be complex and double the expenditure.
As a result, Organizations fail to achieve redundancy for Disaster Recovery/High Availability outside of what the cloud service providers offer for their SLAs (service-level agreement).
3) Limited Micro-Segmentation: Micro-segmentation is based on user roles, regulations, applications, infrastructures, locations, etc, to authorize independent user access. Each segment has a separate security policy that ensures users who can access one of the zones cannot access another with the same authorization.
The cost of maintaining several such segments increases substantially, and between clouds is another challenge. Often, the micro-segmentation model fails when public and private clouds are integrated to work together to provide a shared service.
Fortanix Overcomes the Legacy and Cloud-vendor HSM Limitations
Organizations can deploy Fortanix Data Security Manager (DSM) to overcome all HSM solutions challenges. Fortanix (DSM) is an integrated HSM/KMS solution that provides the flexibility to support multiple deployment options to best meet organizations' needs for security, latency, and operational simplicity. The solution is deployed both On-Prem and SaaS, having the same functionality and integration capabilities.
Fortanix On-Prem HSM has a recommended deployment (over 3 Data Centers) to provide the utmost uptime and availability of an organization's HSM. Fortanix radically reduces legacy footprints for KMS and HSM. The solution is deployed in a clustered architecture to provide the Highest Availability/Disaster Recovery within a single cluster.
However, Fortanix DSM SaaS is the ultimate solution for all HSM security challenges. The SaaS solution provides an entirely secure environment with the ability to interact with the other clouds (AWS, Google Cloud, etc.) seamlessly. Organizations don't have to manage the networking, hardware, and software upgrades because of their on-prem architecture. They can avoid the time required to deploy and manage an On-Prem architecture.
Here's Why Fortanix DSM SaaS is so Effective for HSM Security
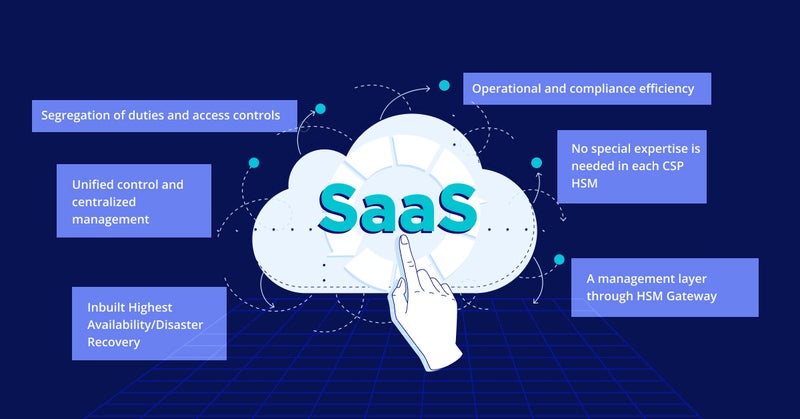
1) Ease of Operations and Administration - Fortanix SaaS requires no physical access because there is no hardware to deploy and software to manage. Instead, the service is 100% remotely controlled and can be accessed via the internet with a button click. SaaS is deployed in minutes and provides the same functionality as on-prem HSMs with 99.95% uptime SLAs.
Fortanix provides a "single pane of glass" modern, multi-tenant, and intuitive user interfaces for simplified administration and increased control, including extensive logging and auditing across your entire infrastructure.
2) Mobility and Flexibility - With the Fortanix SaaS gateway, you can seamlessly move sensitive data between on-premises and public cloud infrastructures with a consistent set of cryptographic services and keys.
Fortanix SaaS offers flexibility to integrate with your applications using industry-standard APIs, such as PKCS#11, Java Cryptography Extensions (JCE), and Microsoft CryptoNG (CNG) libraries. Fully API-driven architecture lets you easily connect to your cloud-native technologies and modern DevOps tools chain.
3) Security Compliant - Fortanix SaaS is FIPS 140-2 Level 3 certified and is supplemented by the power of Intel SGX to protect data in use. It also complies with the highest security standards with FIPS 140-2, PCI-DSS, and SOC 2 Type II certifications.
4) Full Key Control and Lifecycle Management - Fortanix SaaS is a multi-tenant solution that cryptographically separates accounts so that no one, not even Fortanix, has access to keys. Organizations can separately store and own the cloud encryption keys and get full control of their data security.
Fortanix SaaS can create, rotate, expire, and monitor/maintain its keys throughout the key management lifecycle without interruption or performance degradation. In addition, the solution manages HSM clusters, Networking, Load Balancing, and Non-disruptive upgrades.
5) Disaster Recovery/ Highest Availability - Fortanix SaaS lets you set a recovery point for your cluster and create a cluster from a backup to simplify the disaster recovery process. In addition, you can create a copy of the backup and move it to a different region. You can create a new cluster from this backup that is an exact clone of the original. Most importantly, the service is available and delivered across geographies via 15 data centers across the globe.











