Internet of Things—an industry moving so fast that tomorrow’s predictions are often today’s realities.
Take, for instance, the smart hairbrush created by Kerastase and Withings. It uses a gyroscope, an accelerometer, and a microphone to analyze your brushing pattern and tell you if you’re doing it wrong.
Even better— the smart saltshaker. Hover the Smalt over your food, and with an Alexa command, it will dispense salt.
Because twisting a salt grinder is just so much hard work!
Jokes aside— this perpetually expanding flood of data and devices raises grave concern around establishing trust across connected devices on such a massive scale.
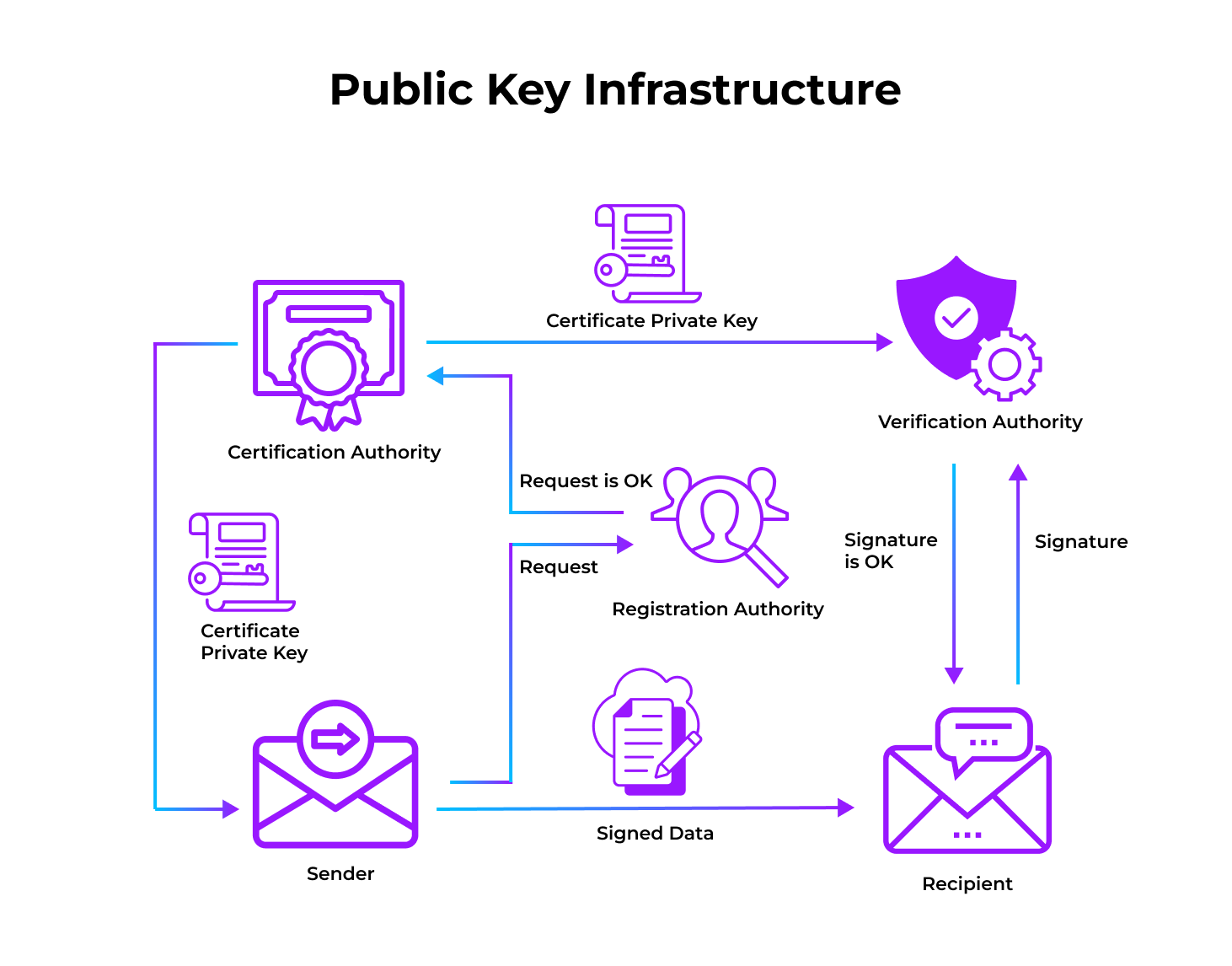
This is where Public Key Infrastructure (PKI) comes into the picture.

What Is PKI’s Role in Securing the IoT Ecosystem?
PKI is essential for establishing and maintaining trust across an IoT ecosystem. It affirms strong authentication during an exchange between—devices to devices, devices to cloud services, and users to devices.
Applying PKI affords some basic and essential mechanisms, ensuring the privacy of communications using encryption. But privacy often comes as an afterthought when implementing an IoT solution—as a bolt-on feature.
Related Read: What is IoT security in Cloud Data Security, and What are the Requirements?
Some of the transformative value we see when IoT bound futures are prophesized relies on devices being able to make decisions and act on their own without human intervention. In these scenarios, both the value and risk are directly tied to the integrity of the data.
Consider a healthcare use case with insulin pumps relying on spoof data sources, but what about energy regulating components that need to trust operational executions sent to them?
Such scenarios highlight the value that data integrity via PKI can deliver.
But IOT Demands More Than Just Regular PKI
Device diversity in an IoT ecosystem is undisputedly its most distinguishable feature, where each device is purpose-built for a distinct use case—with different specifications and capabilities.
This diversity creates a stark divergence between traditional PKI and IoT PKI.
Conventional PKI is built around and serves conventional purposes- say, issuing SSL certificates for internal or public-facing servers or digitally signing applications.
However, with IoT, every case could be unique and a new puzzle to solve. Devices here with configurational limitations such as RAM storage or computational capabilities could render the traditional PKI features unusable.
Secondly, establishing the trust model between different elements of an IoT ecosystem adds another layer of complexity to the PKI model.
Depending on weather it’s a closed ecosystem where you control all the entities, or if it’s an open ecosystem which new users and devices may join in outside your authority—your architects need to work out how and between which actors does trust needs to be established, leading to some unique or not-standard PKI deployment scenarios.
There’s More
Most conventional enterprise IT systems do not have to deal with the additional network architectural tier that gateways, and other intermediary computing devices create in an IoT ecosystem. Traditional PKI may not be designed to handle the security requirements of these important system elements.
Secondly, the sheer magnitude of devices also makes certificates and key lifecycle management a tough feat to achieve. IoT deployments create systems with tens or even hundreds of credentials.
While there is a lot more on that list, the overall challenges that the IoT ecosystem presents over regular PKI can broadly be classified into two major brackets—the Internet, and the Things.
Also read:
Closing Note
In addition to the unique cryptographic and certificate feature requirements, your need PKI services that can support both the volume and velocity of usage within an IOT ecosystem. As I mentioned before in the blog, PKI needs to scale and support millions of certificates rather than the thousands of existing deployments.
Fortanix partners with the likes of Venafi, Keyfactor, and AppViewX to deliver a combined solution that helps enterprises overcome the challenges brought by managing private keys in a complex infrastructure.
For enhanced security and compliance, private keys must be encrypted before they are stored in an enterprise’s infrastructure. Our combined solution gives the enterprise multiple options that cater to the specific needs of that infrastructure.
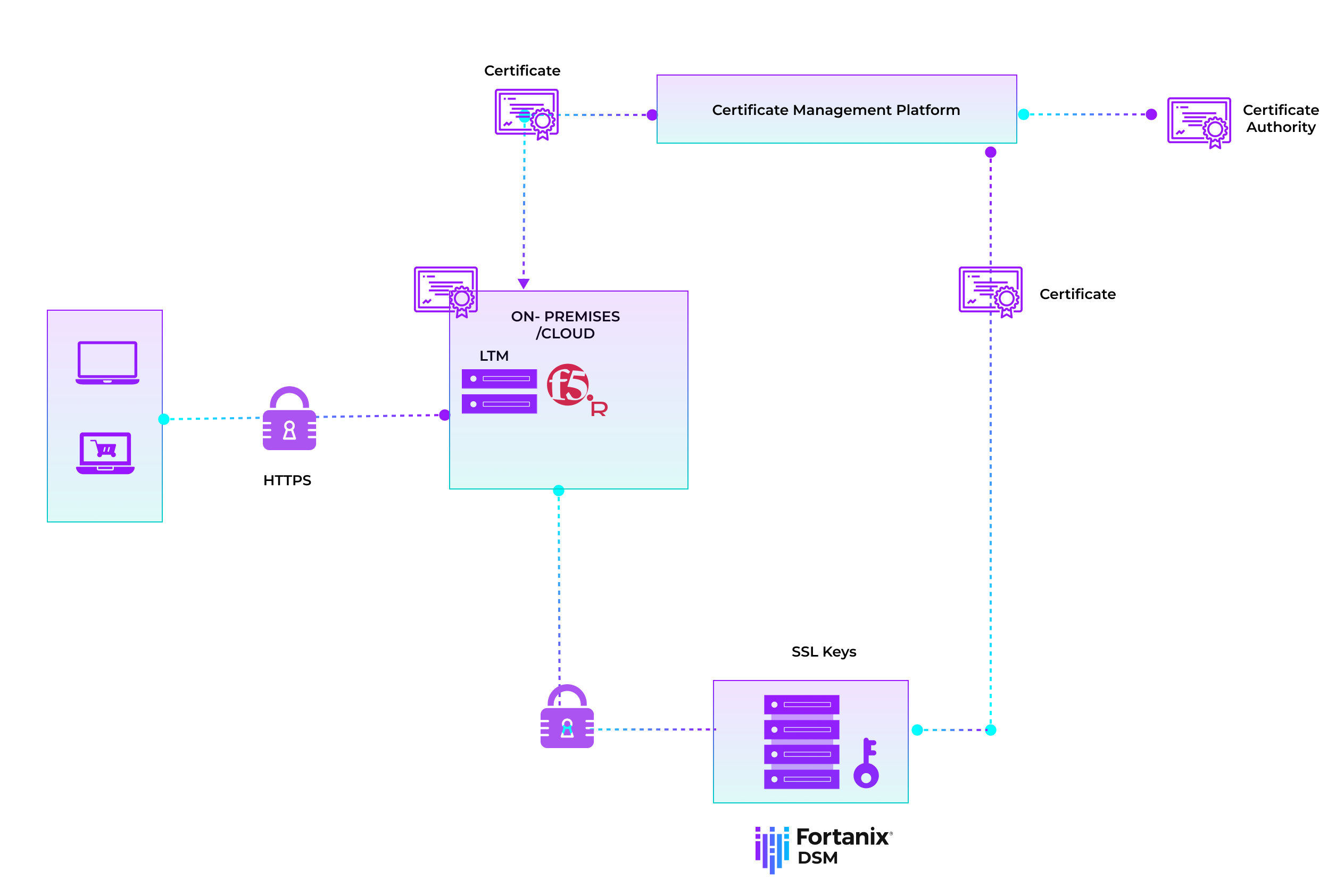
While our partners act as the automation and orchestration engine for the lifecycle management of X.509 certificates, and Fortanix Data Security Manager ensures the security of the private keys associated with those certificates in the cloud, on-premises or as a hybrid solution. What you get is:
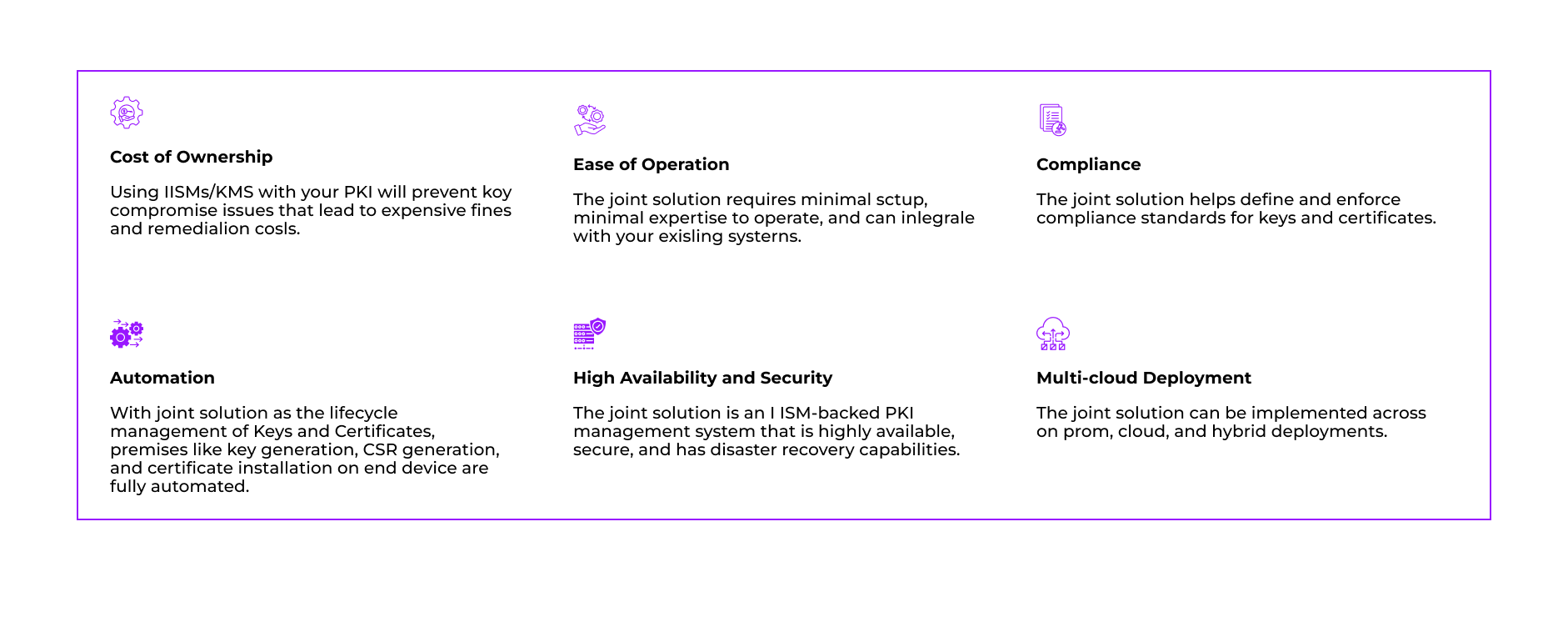
Encrypt and protect private keys using industry-standard, FIPS 140-2 Level 3 certified Fortanix HSM with the flexibility of either on-premises, cloud-based or hybrid services.
- Manage and automate multi-vendor X.509 certificates across multiple devices.
- Ability to generate, store and manage hundreds of millions of keys with automation across key lifecycle.
- Gain visibility and control across all certificates and its keys.
- Enforce policies and ensure compliance across the network.