When organizations decide to use a key management tool, their main worry should be how much control they have over the keys. Since data is shared across multiple cloud services and with various users, it becomes challenging to have full control and visibility.
The key management tool must offer effective oversight and control over users accessing the keys. This is fundamental for storing sensitive information and ensuring data security, especially in complex and interconnected environments.
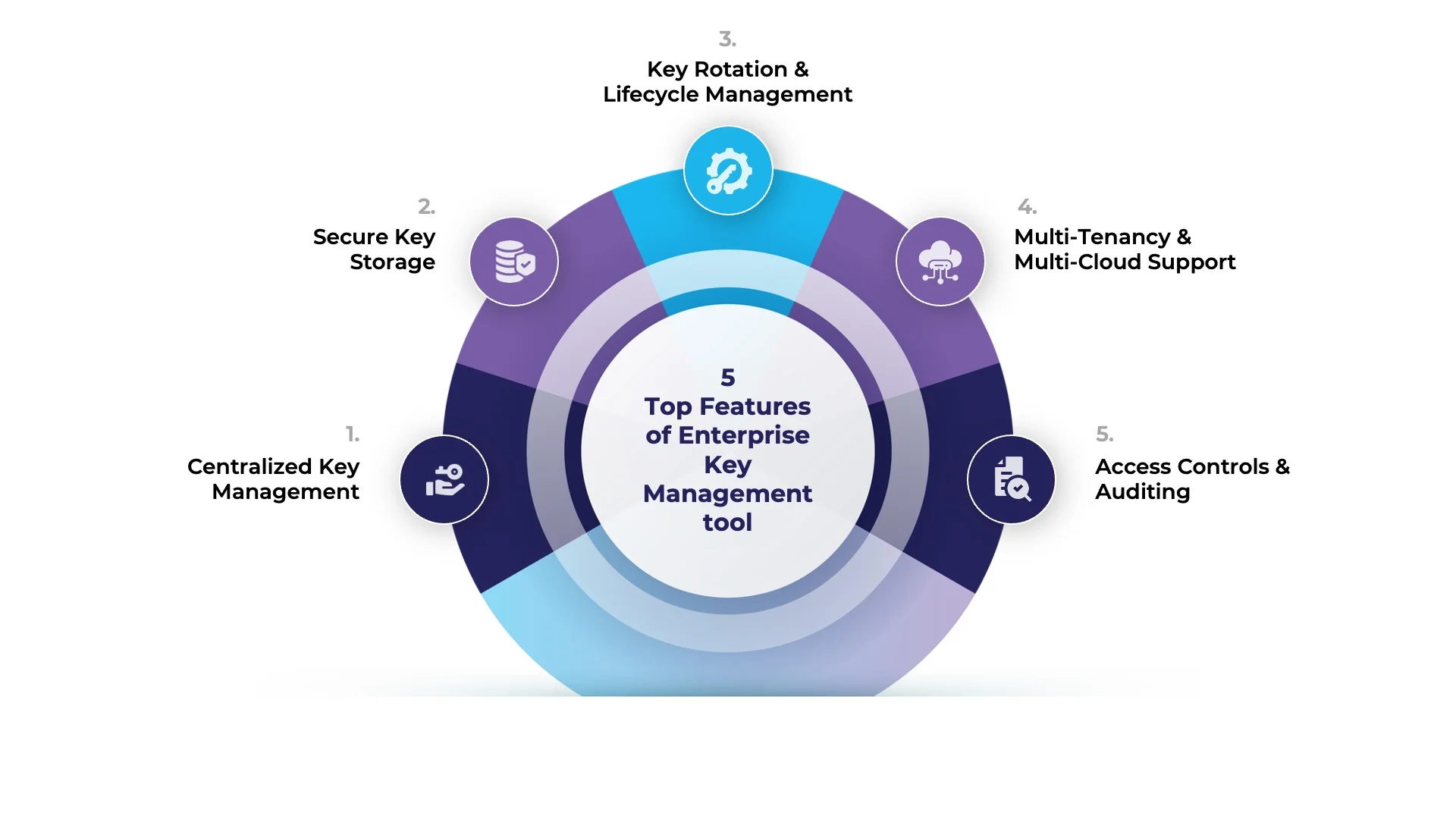
Here are five top features that organizations must consider validating the effectiveness of an enterprise key management tool:
1) Centralized Key Management
Many organizations currently rely on diverse tools and systems to manage keys within different data silos, making it challenging to maintain uniform policies and controls across the entire infrastructure. This fragmented approach exposes a risk of key compromise leading to penalties, recovery costs, and reputational damage and presents challenges for conducting compliance audits.
Transitioning to a unified, centralized Key Management System (KMS) is fundamental to addressing these challenges.
In a centralized system, single-pane control and visibility offer improved control, monitoring, and enforcement of security policies and minimize exposure points to attackers, unlike in a fragmented ecosystem with data silos across multiple cloud providers.
The Bring Your Own Key (BYOK) approach, integrated with KMS, brings the dual-layer protection mechanism into effect. Organizations must check that the chosen key management system is compatible with various cloud providers, including AWS, Google Cloud, and Microsoft Azure, as well as across private cloud, SaaS, and on-premises environments.
2) Secure Key Storage
Organizations are advised to prioritize the integration of FIPS 140-2 Level 3 HSMs into their security infrastructure, particularly in a cloud-first setting. These HSMs, whether delivered through on-premises hardware or as a SaaS service, offer a versatile solution that caters to diverse organizational needs. An additional plugin that links to existing legacy HSMs, enabling the management and accessibility of their keys through a unified interface. The capability to connect with legacy infrastructure and achieve single-pane management allows organizations to transition from legacy systems in a phased manner.
3) Key Rotation and Lifecycle Management
Suppose an organization employs a multi-cloud strategy, they have to utilize services from Cloud Service Providers (CSPs) such as AWS, Azure, and Google Cloud to host and process sensitive data, like customer records or financial information. Each CSP manages its own infrastructure and security protocols, and although they follow the rules, security incidents can still occur.
Consider a situation where one of the CSPs experiences a security breach because of misconfiguration or software vulnerability. In this case, if the organization is using static cryptographic keys without regular rotation, the compromised keys could potentially be exploited by malicious actors for an extended period, posing a significant risk to the confidentiality of data.
Regularly changing cryptographic keys means their usefulness is short-lived, even if a key is compromised. If keys are rotated daily, a compromised key from the breach would only be valid for the day, significantly limiting the potential damage and unauthorized access.
Key lifecycle management maintains consistent access controls and compliance standards across diverse cloud environments, ensuring regulatory alignment with GDPR, HIPAA, PCI DSS, CCPA, etc.
Quick Facts: A report on the impact of cyber threats leading to business data loss
4) Multi-Tenancy and Multi-Cloud Support
Multitenancy is a core requirement in fast-evolving cloud environments. Multitenancy allows data separation for compliance and security. It helps separate data by its sensitivity and spread it across different geos. This also makes securing data for each tenant possible based on its policies and configurations, faster application integration/deployment, and optimal performance.
In a multinational corporation with users dispersed globally, a KMS with multi-tenancy and multi-cloud support enables them to cater to diverse regulatory requirements and user needs. For example, financial institutions operating globally can use this KMS setup to manage encryption keys for sensitive data in AWS for North American operations and concurrently handle keys in Azure for European branches. This helps them ensure a unified and secure global approach to key management.
5) Access Controls and Auditing
When a user forgets their credentials or departs unexpectedly, it poses a problem. One way to address this issue is by providing access to multiple individuals. However, there is a major risk if several administrators have unrestricted access. Unethical users might exploit this situation to steal keys and compromise data. To minimize these risks, granting access to a small group of administrators is generally safer.
Here are a few things to consider. Organizations must segregate the key management operations based on roles and permissions (RBAC). An administrator can activate a quorum approval policy for a group. The ability to compose one or more quorum policy rules based on specific use cases can help secure sensitive crypto operations across an organization. Tamper-proof audit logs can further track the complete history of the key through the key management portal. Integration with SIEM tools is also an added advantage.
Conclusion
The above features collectively contribute to the effectiveness of an enterprise key management tool in securing sensitive data, maintaining compliance with regulations, and supporting the dynamic needs of modern business environments. When evaluating KMS solutions, organizations should prioritize these features to ensure a robust and comprehensive approach to key management.