The old idea of protecting only the perimeter doesn't hold anymore. Data doesn't stay in one place. It flows between clouds, SaaS apps, on-prem systems, and edge devices. Businesses depend on real-time access to that data across geographies, services, and platforms. And yet, traditional data protection methods were built for static environments and slow workflows. That's a problem.
The data protection model has to change as workloads shift to multi-cloud and edge architectures. Encryption alone is not enough.
Visibility and control must follow the data, wherever it moves, in real time. Organizations require a new mindset and a different set of tooling. Otherwise, teams are left reacting to incidents instead of preventing them.
Let us understand why.
The Real-Time, Multi-Cloud Problem
Most organizations use services from multiple cloud providers, such as AWS, Azure, GCP, etc. When you add SaaS platforms like Salesforce or Workday and data lakes scattered across locations, you've got a possibility of data sprawl that's difficult to govern.
Meanwhile, applications such as financial transactions, sensor logs, analytics pipelines, or AI model training consume and generate data in real time. Sensitive data might be processed on one cloud, stored in another, and visualized through a third-party dashboard.
With that much movement, the old way of setting static policies and doing periodic audits no longer fits.
The real risk is data loss, unauthorized access, improper usage, key misuse, and shadow data copies made on systems that don't meet security or compliance standards.
Where Traditional Cloud Data Protection Falls Short
Conventional data security tools protect storage, not data flows. They focus on encrypting data at rest or in transit, placing controls on buckets or drives.
However, those traditional controls break down when data flows between services and clouds.
Here's what gets missed:
- No central view of encryption keys: Inconsistent key management across clouds leads to blind spots.
- Limited policy enforcement: Most security teams can't apply real-time policies on who can access what data, where, and when.
- Lack of context: Conventional tools cannot detect the difference between a developer testing a pipeline and an attacker exfiltrating records.
- Slow response time: Incident response is reactive, after data exposure has occurred.
What a Modern Cloud Data Protection Approach Looks Like
Security must shift closer to the data to secure data in real-time across multiple clouds. It must operate continuously and not be limited to scheduled scans or policy checks.
Here’s what the new approach requires:
- Unified Key Management: If you do not control data visibility, you cannot protect it. Each cloud has its own native key management system, but separate KMSs create a fragmented view. Enterprises need centralized control over all encryption keys regardless of where the data resides. That means managing AWS KMS, Azure Key Vault, GCP Cloud KMS, and HSMs from one place. A unified KMS lets teams revoke or rotate keys across services, automate lifecycle management, and maintain compliance logs.
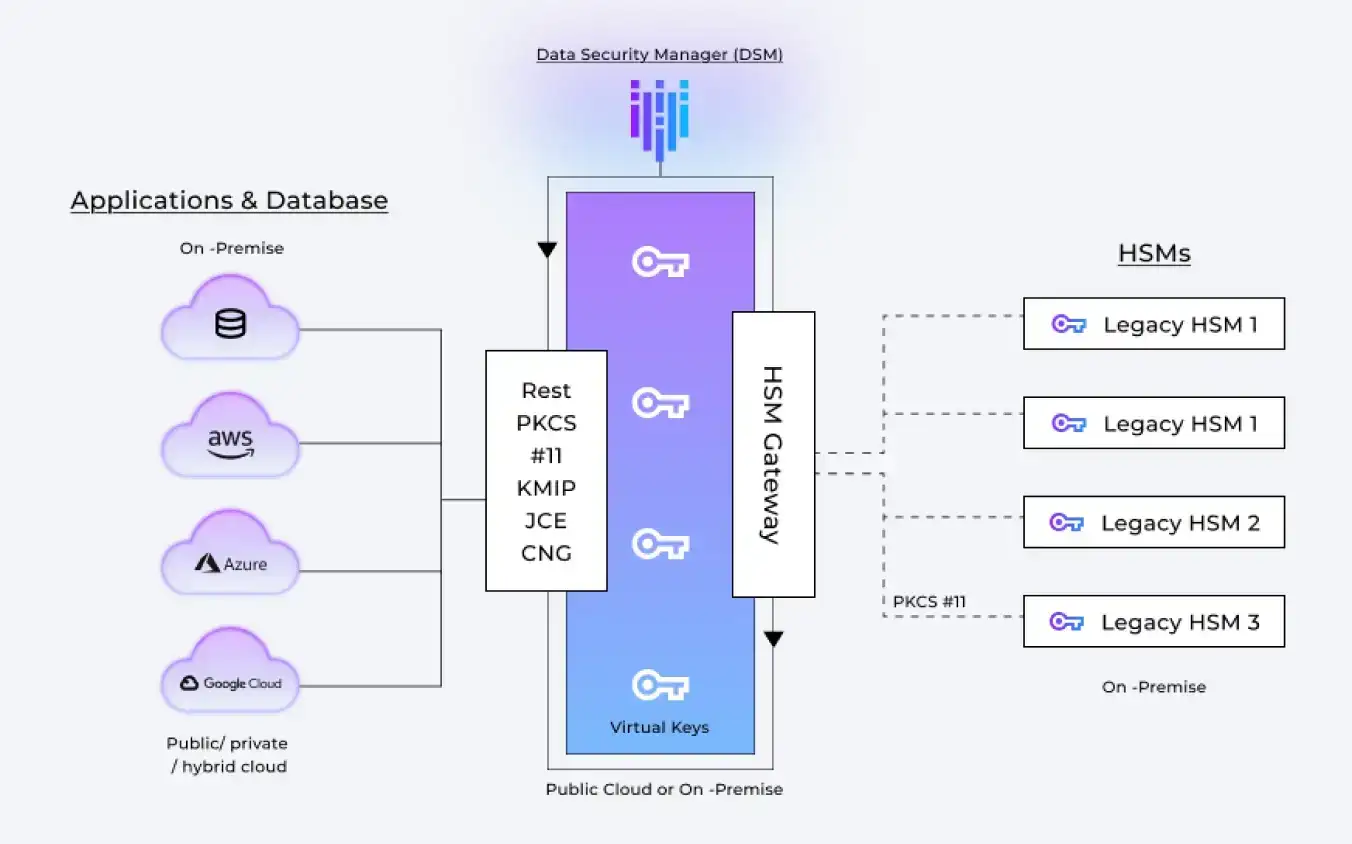
- Bring Your Own Key (BYOK): Many companies want to retain ownership of their keys when using cloud services for compliance and sovereignty. BYOK enables organizations to supply their own keys to cloud platforms. It will not allow the cloud provider to see or control the key. This level of control prevents unauthorized access, even from cloud admins or foreign jurisdictions.
- Real-Time Data Access Policies: Security teams need fine-grained access policies that apply in real time based on identity, location, time, and purpose. That includes conditional access to decrypt data only when specific criteria are met. For example, "Allow only finance team members to decrypt payroll files from corporate IPs between 9 AM and 6 PM." This level of dynamic control is much needed.
- Audit and Visibility for Data Flows: Audit logs are mandatory because you need visibility into when data is accessed, by whom, under what conditions, and where the keys were used. That data should be query-able for compliance and security investigations. Audit logs also enable anomaly detection, flagging when someone suddenly tries to decrypt large volumes of sensitive data at odd hours.
- AI and Analytics Workload Protection: Modern workflows feed sensitive data into AI models or analytics platforms. These processes happen across GPUs, ML pipelines, and data lakes. You need a way to protect the data used for training or inference without slowing down performance. Confidential computing, tokenization, and enclave-based encryption allow you to process encrypted data without exposing it to the underlying infrastructure.
Rethink the Cloud Data Security Strategy
Public cloud data protection adds a layer of complexity. While cloud-native services offer basic security, relying solely on them without centralized governance leaves gaps. Businesses need data protection for cloud environments that matches the speed and complexity of real-world operations.
If your security doesn’t match the movement of your data, it needs an update. Breaches occur in a misconfigured bucket, a leftover token, or a test environment with production data.
In multi-cloud setups, mistakes multiply. Data is copied, synced, backed up, or analyzed across regions, vendors, and tools. Every copy becomes a liability. Without consistent key control and visibility, it’s easy to lose track.
Protecting data in static environments is easy. The next challenge is to protect data that never stops moving between users, clouds, and services. What worked five years ago doesn’t work now.
We need systems built for movement, not just storage. Security must follow the data. Key management must be unified. Access must be conditional, time-bound, and context-aware.
Security can’t be bolted on. It must be built in. And that starts by regaining control of your environment’s most powerful resource: your data.











