The U.S. government's Executive Order 14144 marks a major push to revamp national cybersecurity. It calls for sweeping upgrades to federal systems and sets the tone for wider industry standards, especially securing the software supply chain and using stronger cryptographic methods.
With the demands of this executive order, having advanced technology in place is a must. Fortanix data security platform offers a robust data security solution that can support federal agencies and their partners in aligning with the strict standards outlined in EO 14144.
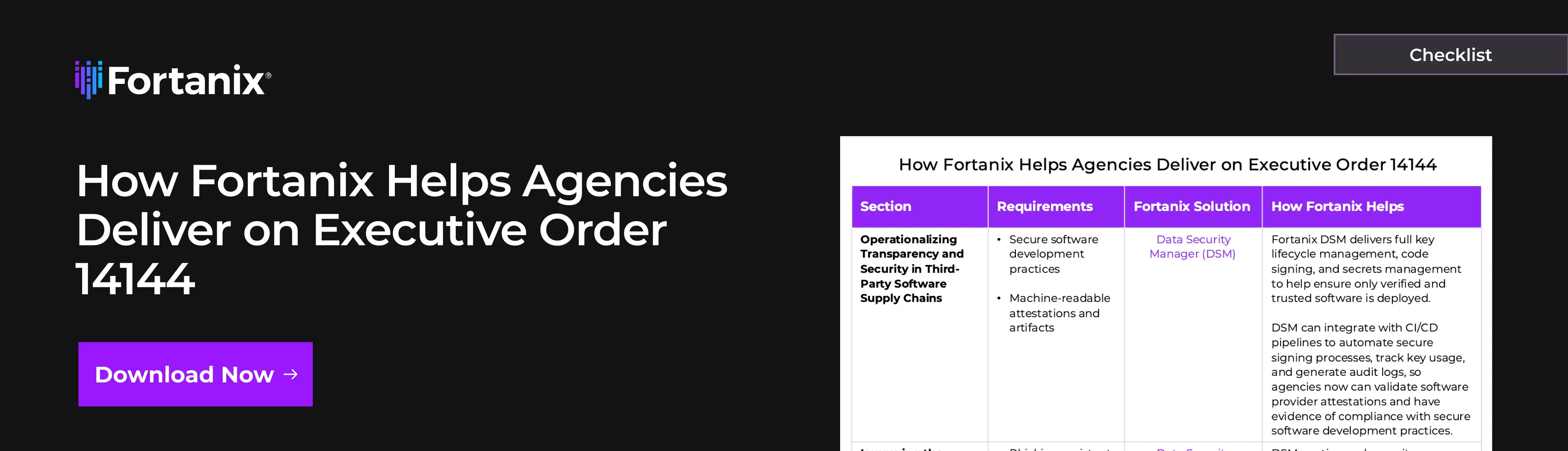
Below is a technical breakdown of how Fortanix addresses several core areas of the order.
Section 2: Securing the Software Supply Chain
EO 14144 strongly emphasizes securing software development lifecycles and demanding transparency from providers.
- How Fortanix Helps (DSM): Fortanix Data Security Manager (DSM) securely manages the cryptographic keys and certificates required for code signing. This ensures software integrity and helps providers meet attestation requirements. Fortanix DSM can integrate directly into CI/CD pipelines to automate secure signing, providing verifiable artifacts. Its audit logging capabilities help agencies track key usage and validate provider attestations, which increases trust and transparency in the software supply chain.
Section 3 & 4: Bolstering Federal Systems and Communications Security
These sections mandate adopting proven security practices, enhancing threat detection, and implementing strong encryption for all federal communications, including preparing for the quantum threat.
- How Fortanix Helps (DSM, Key Insight, Confidential Computing Manager):
- Threat Detection (Sec 3.C): Fortanix DSM tracks cryptographic activity as it happens and can link with SIEM systems to flag any unusual or potentially suspicious activities.
- Encryption for Communications (Sec 4.c, d, e): DSM manages keys and certificates for TLS 1.3, which is crucial for securing web traffic. It supports cloud key management through Bring Your Own Key (BYOK) integrations with cloud providers like Microsoft and Google for email encryption. It also integrates with Google Client-Side Encryption to protect data in Google Workspace, including Drive, Chat, and Meet. Fortanix DSM can also integrate with firewall vendors to enable keyless SSL/TLS and secure DNS communications. (Internal note: DNS and Email/Video/IM encryption points require further review for precise mapping).
- Quantum-Resistant Cryptography (Sec 4.f): Fortanix is at the forefront of the transition to quantum-safe cryptography (PQC). Fortanix Key Insight discovers and assesses the entire cryptographic landscape, identifying assets vulnerable to quantum attacks. Fortanix DSM already supports NIST post-quantum cryptography algorithms (ML-KEM, ML-DSA) alongside CNSA 2.0 requirements (SHA, AES, XMSS, LMS), enabling organizations to begin their crypto-agility journey.
- Hardware Security Modules & TEEs (Sec 4.g): The EO calls for robust protection of keys and tokens, often using HSMs and isolation technologies. Fortanix provides FIPS 140-2 Level 3 HSMs (on-prem and SaaS) for secure key storage and management. Additionally, Fortanix Confidential Computing leverages Trusted Execution Environments (TEEs like Intel SGX) to encrypt data while in use, providing unparalleled protection for keys, tokens, and sensitive processes, even in untrusted environments like the cloud. This centralized management across hybrid and multi-cloud environments simplifies compliance.
Section 7: Aligning Policy to Practice – Zero Trust Architecture
EO 14144 promotes Zero Trust Architecture (ZTA) to modernize security.
- How Fortanix Helps (DSM): ZTA relies on strong identity verification and least-privilege access, especially for sensitive assets like encryption keys. Fortanix DSM enforces fine-grained, role-based access controls (RBAC) for keys and secrets. Organizations can monitor and enforce ZTA policies with the help of real-time audit logs that provide visibility into key usage.
Section 6: Promoting Security with and in Artificial Intelligence
The EO acknowledges the role of AI in cyber defense but also vouches for the security of AI systems.
- How Fortanix Helps (Armet AI, DSM): Armet AI is Fortanix's secure Gen AI platform using Confidential Computing enclaves to protect the entire AI pipeline. It enables enterprises to safely build custom AI applications using their sensitive data while maintaining security and compliance. For AI coding assistance, Fortanix DSM can secure the cryptographic keys used in AI-generated code, mitigating potential vulnerabilities introduced during development.
Section 5, 8 & 9: Combating Cybercrime, Securing National Security Systems & Critical Infrastructure
These sections mention reducing identity fraud, applying advanced security to critical systems, and protecting vital infrastructure.
- How Fortanix Helps (DSM):
- Digital Identity (Sec 5): Fortanix DSM securely manages the cryptographic keys, credentials, and certificates that support digital identity documents, preserving their trustworthiness and preventing manipulation or fraud.
- Hardware Roots of Trust (Sec 8.c): Fortanix DSM's support for HSMs and using TEEs via Confidential Computing provide the hardware-anchored root of trust required for securing NSS and other high-impact systems.
- Critical Infrastructure (Sec 9): Fortanix DSM secures the encryption keys and certificates vital to the operation and resilience of critical infrastructure (OT/ICS). With real-time audit logs, organizations achieve visibility to detect and respond rapidly to potential threats against these systems.
Conclusion
Executive Order 14144 raises the bar for how cybersecurity is approached throughout the United States. Fortanix provides a robust, unified data security platform that directly addresses many of the EO's most critical technical requirements – from securing the software supply chain, enabling Zero Trust architecture, supporting quantum-resistant cryptography to protecting data in transit and use with advanced encryption and Confidential Computing.
With Fortanix, organizations can significantly accelerate their compliance journey and build a more resilient security posture that fits the modern threat landscape.