Hyperledger Fabric is described as an open-source permissioned distributed ledger technology (DLT). Unlike permissionless networks like Bitcoin or Ethereum where virtually anyone can participate, Hyperledger operates amongst a set of participants that prove a certain level of trust in the network.
This helps the network to work towards minimizing malicious activities in the form of smart contracts or transactions.
The participants in the network each have a digital identity in the form of X.509 certificates, as we know it’s a permissioned network, the identities are important to determine the user’s permission and access to resources in the network.
The trust in identity must come from a trusted authority, in the case of Hyperledger Fabric, it comes from Membership Service Provider (MSP) which issues X.509 certificates which are based on Public Key Infrastructure (PKI) and is achieved by Certificate Authorities (CA) where every participant who wants to interact with the network first gets a verifiable identity from the Certificate Authority.
In the context of Hyperledger Fabric, they are called a “Fabric CA”. Certificate Authorities issue identities using a public-private key pair, and the private keys are used to generate signatures for transactions.
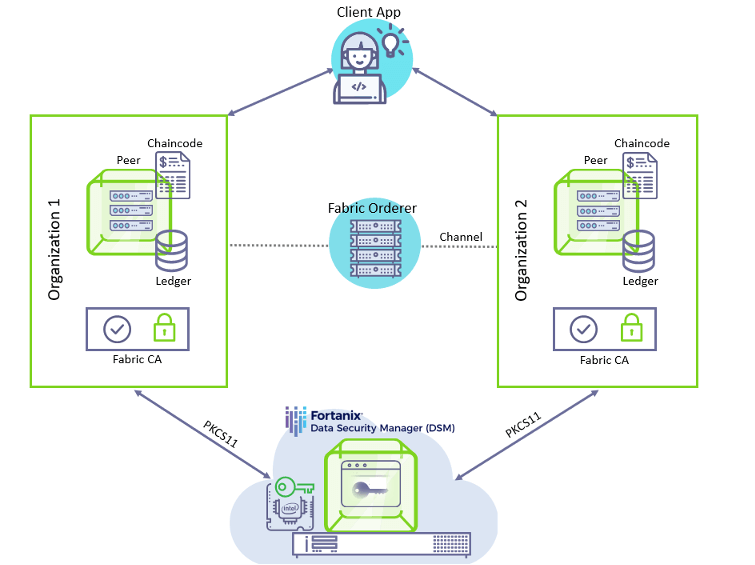
The crypto operations for the Hyperledger Fabric nodes can be offloaded to a Hardware Security Module (HSM) for secure storage and other crypto operations. This is enabled by the Fabric node’s BCCSP (Blockchain Cryptographic Service Provider) using the PKCS11 standard.
The Fabric CA can be set up by modifying the configuration represented by YAML files, in specific the BCCSP section. Once the server for Fabric CA is started, the private key is generated and stored in an HSM.
The Fabric CA clients can then register and enroll their identities to the CA server by modifying their BCCSP sections to use an HSM. The detailed steps for setting up the network and configuring the CA servers and clients can be found in the official documentation of Hyperledger Fabric.
As Hyperledger Fabric supports the PKCS11 standard to connect with HSMs, we can use Fortanix DSM for the crypto operations of the Fabric Node, as it provides a PKCS11 library client that enables users to use Fortanix DSM like an HSM.
Fortanix provided clients can interact with DSM for key management and crypto operations. HSM and PKCS11 specifications have terminologies of slots and tokens which correspond to physical hardware.
The Fortanix PKCS11 library works by providing many numbered slots that can be used like a traditional HSM but managed inside a secure Fortanix DSM environment which makes use of confidential computing to safeguard keys for storage and use in crypto operations.
This way, Fabric users can move from non-HSM setups or even HSM setups to Fortanix DSM for their crypto operations, thereby leveraging the many advantages Fortanix DSM brings over traditional HSMs.
Users can find detailed aspects of PKCS11 configuration at https://support.fortanix.com/hc/en-us/articles/360016160451-Clients-PKCS-11-Library.
A detailed integration guide is available at https://support.fortanix.com/hc/en-us/articles/8723554765332-Using-Fortanix-Data-Security-Manager-with-Hyperledger-Fabric that explains how you can setup Fortanix DSM for use in the Hyperledger Fabric network.
To understand how Fortanix DSM is better than traditional HSMs refer to https://www.fortanix.com/blog/2021/09/the-hsm-is-dead-long-live-the-hsm.










