When speaking with CISOs and cybersecurity professionals, the conversation often revolves around technologies such as firewalls, Extended Detection and Response (XDR), Security Information and Event Management (SIEM), antivirus solutions, and Data Loss Prevention (DLP) tools. These are all crucial components of a well-rounded security strategy.
However, there is a critical area that frequently goes overlooked: data encryption.
Despite the fact that encryption is mandated by numerous regulations - including but not limited to:
- General Data Protection Regulation (GDPR)
- Network and Information Security Directive 2 (NIS2)
- Digital Operational Resilience Act (DORA)
- Revised Payment Service Directive (PSD2)
- Payment Card Industry – Data Security Standard (PCI DSS)
- Cyber Resilience Act (CRA)
many organizations still fall short of effectively implementing strong encryption practices.
Data Is the Crown Jewel - Treat It That Way
In most environments, applications are the gateway to the organization’s most valuable asset: its data. While many organizations invest heavily in perimeter defenses, like a fortress guarding a treasure, they often fail to properly secure the treasure itself.
If an attacker manages to bypass these outer defenses, they could gain direct access to your sensitive data. Unfortunately, such breaches occur regularly - even in environments considered highly secure.
The only way to protect data effectively is through proper encryption.
Encryption Alone Is Not Enough
While it's encouraging that many organizations do encrypt their data, there’s a common mistake that undermines the effort: storing encryption keys alongside the application or data they protect.
Figure 1 shows this scenario: The application data is encrypted with a key residing on the same server. If an attacker has gained access to the application server, they can steal the encrypted data including the encryption key and therefore are able to decrypt the data.
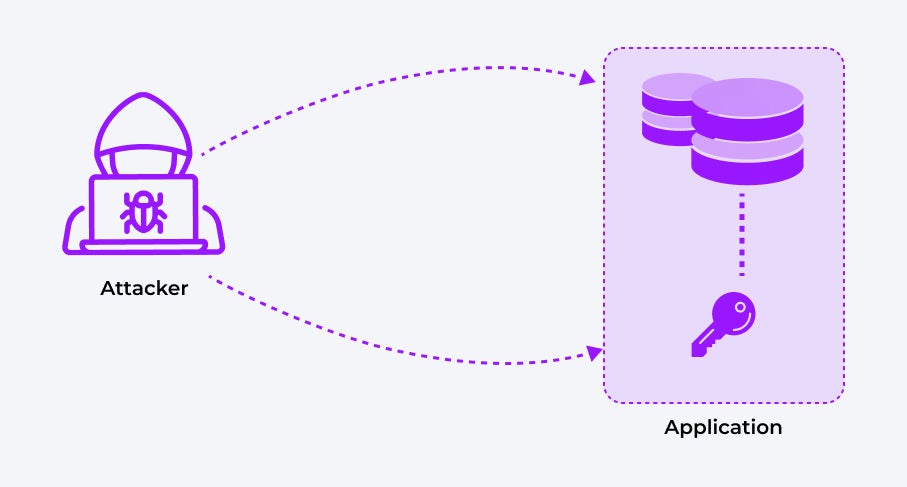
Figure 1: Encryption without HSM
This is analogous to locking your house but leaving the key taped to the front door. If an attacker compromises your server, they not only gain access to the encrypted data - but also to the keys required to decrypt it. In such a scenario, the encryption becomes useless.
This is a fundamental and dangerous security gap.
Introducing the Hardware Security Module (HSM)
To close this gap, organizations should leverage a Hardware Security Module (HSM) - a tamper-evident, hardened device specifically designed to manage and protect cryptographic keys.
As shown in Figure 2, the data is still encrypted but with a key protected by an HSM. While an attacker might gain access to the encrypted data, they cannot obtain the encryption key, which is securely stored inside a FIPS 140-2 Level 3 certified HSM, protected against extraction even in the event of a system compromise.
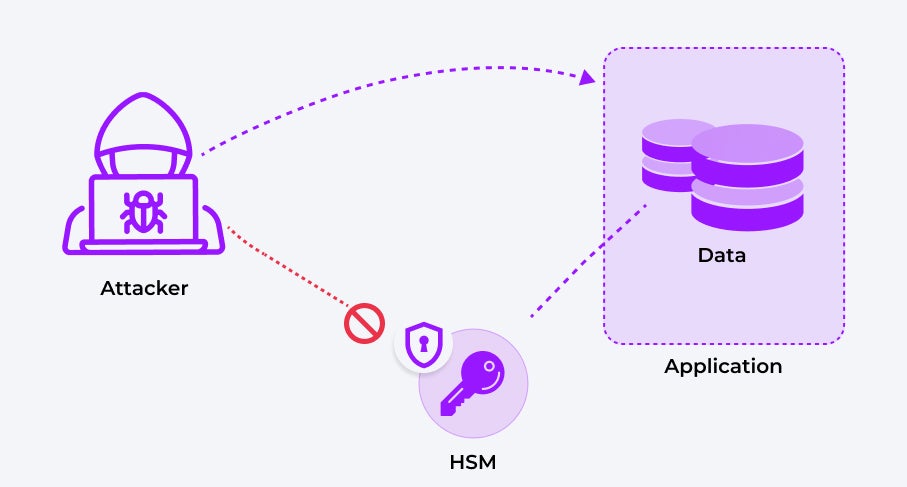
Figure 2: Encryption with HSM
With an HSM:
- Encryption keys never leave the secure hardware boundary.
- Applications can request the HSM to perform cryptographic operations (e.g., encryption or decryption), but they never gain access to the key itself.
- Even in the event of a breach at the application level, the attacker cannot obtain the key.
This separation between encrypted data and the encryption keys drastically improves your security posture.
Compliance and Best Practices
Separating encryption keys from the data they protect is not just a best practice - it's a requirement in several industry standards and guidelines, including:
Payment Card Industry – Data Security Standard (PCI DSS)
- Payment Card Industry – Data Security Standard (PCI DSS)
- NIST SP 800-57 (Recommendation for Key Management)
- NIST SP 800-111 (Guide to Storage Encryption)
- ISO/IEC 27002 (Information Security Controls)
By implementing an HSM, your organization moves toward compliance with these frameworks and significantly reduces its risk exposure.
How to Get Started
If your organization is ready to take encryption seriously, Fortanix offers a comprehensive solution: the Data Security Manager (DSM). DSM includes a built-in HSM along with a robust Key Management System (KMS), giving you everything needed to protect your cryptographic assets.
Fortanix modernizes the traditional HSMs by delivering a cloud-scale, software-defined solution that combines the highest levels of security with the agility of modern infrastructure.
Powered by Intel® SGX, Fortanix HSMs enable secure key management and encryption operations with strong isolation, even from attackers that gain privileged access. Unlike legacy HSMs, Fortanix’s solution is built for cloud-native environments, offering seamless API integration, elastic scalability, and centralized management across on-premises, cloud, and hybrid deployments.
This solution brings cryptographic services closer to applications, reducing latency while maintaining compliance with stringent security standards like FIPS 140-2 Level 3.
Fortanix also provides flexible deployment options to meet various IT strategies:
Prefer a cloud-first or cloud-only approach? Fortanix’s SaaS offering requires no on-premises hardware and is quick to set up.
Want to evaluate before committing? Simply visit the Fortanix website and sign up for a free trial - it takes less than two minutes.
Conclusion
Encrypting your data is essential. But doing it correctly - with proper key management and hardware-based protection - is what makes the difference between compliance theater and real security.
If you're serious about protecting your crown jewels, it's time to put an HSM at the heart of your encryption strategy.
For more information, please contact Fortanix.











