Software is Eating the World
You’ve probably heard the phrases “The world runs on software” and “Software is eating the world”, which date back to 2010 and 2011 respectively. If it was true back then, it is even more true today.
We cannot imagine a world without computers, mobile phones or the Internet. Software is also increasingly prevalent in industrial robots, cars, airplanes, televisions and a plethora of IoT devices around the home.
As we move towards a cashless society, our financial transactions increasingly depend on software. More and more of our personal information is stored in countless databases.
Our on-line browsing and shopping are tracked and analyzed. Everything from intellectual property to state secrets are communicated and stored under software control. Machine learning, AI, big data, analytics – it all relies on software.
Software's power — the ability to be adapted, tuned, and improved — is also it's downfall
The Need for Security
Crime has always been a part of human society, so we have developed physical security, such as locks, guards and CCTV, to deter and prevent theft.
But in today’s interconnected world, criminals can steal data and even money by exploiting software vulnerabilities, and they can do this at a great distance and with complete anonymity, completely bypassing any physical security measures.
Thus, we need to find new ways to protect the confidentiality of data (i.e., keep it secret), the integrity of data (i.e., prevent it being changed) and the availability of data (i.e., be able to use it when we need to).
The Problem with Software
However, software is, by its nature, vulnerable. Its power – the ability to continually adapt, tune and improve it – is also its downfall. It can be corrupted and changed. Malicious software can be inserted.
It is very difficult and expensive to write secure software, and with increasing size and complexity it becomes essentially impossible. Software developers are encouraged to develop code quickly due to financial and competitive pressures, with functionality and convenience prized over security.
As a result, we end up with vulnerabilities such as buffer overflows, SQL injection and XSS, leading to compromised systems, malware and data leakage. Major data breaches have become everyday events, despite regulations and heavy fines.
Software developers are in a never-ending arms race with hackers. Operating systems, applications, firewalls – everything is vulnerable and needs constant patching. We add anti-virus tools, intrusion detection systems and other security measures – more software!
Today, it is common to assume your systems will be breached and that organizations must be able to detect and respond rapidly to minimize the damage.
Can Cryptography Save Us?
Perhaps the most valuable tool we have to combat such threats is cryptography – strong algorithms that mathematicians assure us are secure against any known attacks.
But these are typically implemented in software, so errors can be (and frequently are) made, and if the integrity of the system is breached, then all bets are off. Moreover, cryptography depends on keys.
If a key is compromised, then so is the data it is protecting. All we have done is substitute the key for the data – we still have to protect something. The only advantage we have is that the key is smaller – can we find a way to keep keys safe?
Enter Hardware Based Security
This is where hardware comes in. Hardware security modules (HSMs) are application-specific devices that provide cryptographic services to applications.
They use physical entropy sources to generate strong cryptographic keys and provide strong logical and physical protection for them (e.g., tamper prevention and detection).
Also, a closed operating environment with secure boot code and hardened operating system; and certified implementations of cryptographic algorithms with tightly defined APIs and a small attack surface.
HSMs are most commonly used in banking applications to secure financial transactions, such as credit card payments; they are also used within enterprises to secure PKI systems and in other security-critical applications.
However, being dedicated hardware devices, they are generally too expensive, inflexible, non-scalable and difficult to use for widespread adoption.
Smartcard chips found on credit cards provide similar capabilities and have achieved widespread adoption, and Trusted Platform Module (TPM) chips found on many PC motherboards have had some success too.
But perhaps the biggest success story to-date for hardware based security is in mobile devices, which commonly have special hardware security systems (e.g., Apple Secure Enclave and ARM TrustZone) for the secure storage and use of cryptographic keys and biometric data.
Cloud – The Final Frontier
Enterprises are increasingly moving their software and data into the cloud because of the significant financial and operational benefits it can provide.
However, there are justified security concerns with cloud-based servers, which are owned and operated by third parties and often shared between multiple customers.
Servers connected to the Internet are particularly vulnerable to attack. Moreover, whilst cryptography (optionally using an HSM) can secure data-at-rest and data-in-motion, it cannot protect data-in-use.
While data is in use, it sits unencrypted in system memory, completely unprotected against hacking and malware or an attacker with physical access to the server. Even servers in private data centers are vulnerable, too.
Intel® SGX – a New Paradigm in Data Security
To address the problem of protecting data-in-use, Intel is introducing Software Guard Extensions (SGX) across its range of processors. SGX allows applications to execute within secure enclaves enforced at the hardware level by the CPU itself.
All data is encrypted in memory and only decrypted while being used inside the CPU. This means that, even if the operating system, hypervisor or root user are compromised, the data is still completely secure. For the first time, data can be fully protected across its full lifecycle – at rest, in motion and in use.
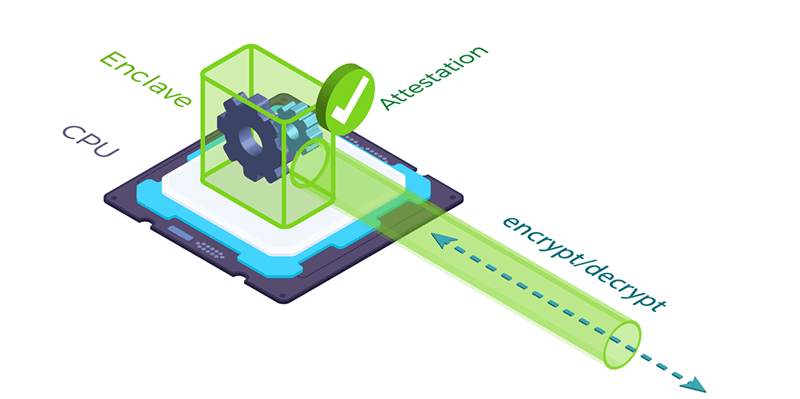
Intel® SGX Secure Enclave
SGX even takes security one step further using a process called “attestation” to verify that the CPU is genuine, and that the application is the correct one and hasn’t been tampered with.
Using Intel SGX, you can have complete confidence that your code is running as intended and that the data is completely protected, wherever it is.
This is a complete game-changer – it enables sensitive applications, including machine-learning and AI, to be run in the cloud and introduces the new concept of confidential computing.
Conclusions
Software is simply not up to the job of protecting highly sensitive or valuable data. Cryptography helps, but it needs high-quality keys that are well protected. Thus, hardware based security is commonly employed in banking and in particularly vulnerable applications such as credit cards and mobile devices.
But the biggest problem today is with cloud-based software applications processing vast amounts of sensitive data that is completely unprotected when in use.
Hardware-based security in the form of Intel® SGX technology can now provide a solution to that problem, promising to reduce data breaches dramatically and enabling the cloud to finally live up to its true potential.
Epilogue: Fortanix Runtime Encryption®
Fortanix® was the first company to offer commercial solutions based on Intel® SGX technology. Our open-source Enclave Development Platform (EDP) allows developers to write applications to run in SGX enclaves, whilst our Runtime Encryption Platform enables existing applications to be ported easily to SGX enclaves and deployed seamlessly.
Fortanix DSM is a complete key management system and HSM built on top of Intel® SGX technology, providing a modern, cloud-friendly, scalable and easy-to-use alternative to traditional HSMs.
These products work in concert to provide the world’s first holistic hardware based security solution for data at rest, in motion and in use.
Fortanix Confidential Computing Manager
Fortanix offers application teams the fastest, easiest, and most complete solution to run enclave applications today. The Fortanix Confidential Computing Manager enables applications to run in confidential computing environments, verifies the integrity of those environments, and manages the enclave application lifecycle.









