Encrypt Data Everywhere
Encryption is your last line of defense. From file system to database encryption to data masking and tokenization, Fortanix enables you to secure data at every layer across all your environments and avoid paying millions in data loss or regulatory fines.

File System Encryption
Go beyond full disk encryption and protect individual file systems, actively in-use on a designated host.

Transparent Database Encryption
Manage cryptographic keys for databases like Oracle, SQL Server, and MongoDB, securing them on FIPS-validated HSMs.

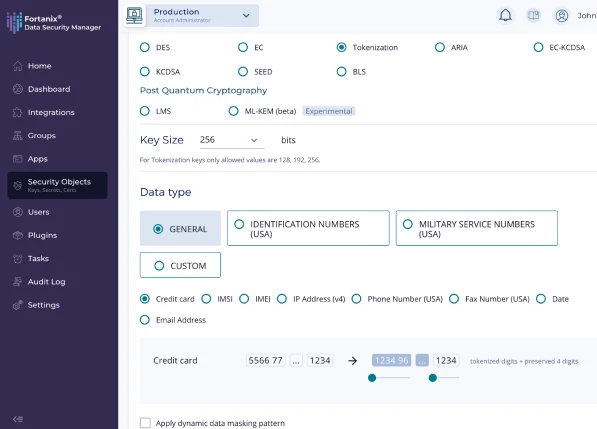
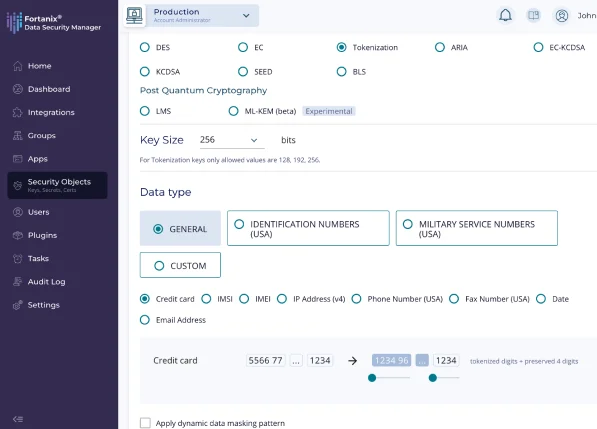
Data Tokenization
Anonymize data while preserving its integrity and structure by tokenizing sensitive data sets like PANs, PHI, and PII.
Enterprise Key Management
Store, search, rotate, and retire cryptographic keys on a single platform that gives you full control. Apply encryption policy with few clicks and drive consistent security. Fortanix makes compliance and data sovereignty easy, securing all of your keys and secrets on high-performance HSMs offered as a service.

Key Management Service (KMS)
Simplify key lifecycle administration across hybrid multicloud environments.

Hardware Security Module (HSM)
Securely generate, store, and use cryptographic keys and other assets.
Data Security Manager Helps You With
Multicloud Key Management
Post Quantum Cryptography
HSM Modernization
Regulatory Compliance
Secrets Management
Code Signing

Multicloud Key Management
Fortanix seamlessly integrates with cloud-based and legacy key management services with multicloud key management.

PQC
Stay ahead of quantum computers. Discover and assess your cryptographic security posture across your environments to prioritize and remediate quantum risks.

HSM Modernization
Start fresh on Fortanix's scalable, compliant infrastructure or consolidate your legacy HSMs using our secure HSM gateway. All of our hardware is FIPS 140-2 L3 validated and comes with on-prem and Saas deployment options.


Regulatory Compliance
Enterprise-grade security controls, data encryption across all layers, and enterprise key management, built on confidential computing, helps you drive regulatory compliance.


Secrets Management
Manage credentials, API keys, and other secrets on the same unified platform.


Code Signing
Let developers cryptographically sign code to verify the authenticity and integrity of applications.

Supercharge Performance and Flexibility
Add even more scale and support for high transaction volumes on the Fortanix platform.

DSM Accelerator
Encrypt your data at a very high throughput, cache keys locally on the application host, and activate in-memory encryption and decryption.

Secure Business Logic
Securely run sensitive business logic inside Fortanix HSMs, integrate business workflows, and impose custom access control policies on your keys.
Resources
Here are some of latest news, blogs, resources, events, and more