Overview
The Fortanix Confidential Computing Manager enables applications to run in confidential computing environments, verifies the integrity of those environments, and manages the enclave application lifecycle. The solution orchestrates critical security policies such as identity verification, data access control, and code attestation for enclaves that are required for confidential computing. Unlike other approaches, Fortanix provides the flexibility to run and manage the broadest set of applications, including existing applications, new enclave-native applications, and pre-packaged applications.
Benefits

Simplicity
Fortanix is the only turnkey solution that manages the entire confidential computing environment and enclave lifecycle.

Existing Applications Support
Unlike other approaches, Fortanix provides the flexibility to run and manage the broadest set of applications, including existing applications, new enclave-native applications, and pre-packaged applications.

Code Verification
Unlike other solutions, Fortanix verifies the identity of code and applications using digital certificates and PKI.
Key Features

Enclave Lifecycle Management
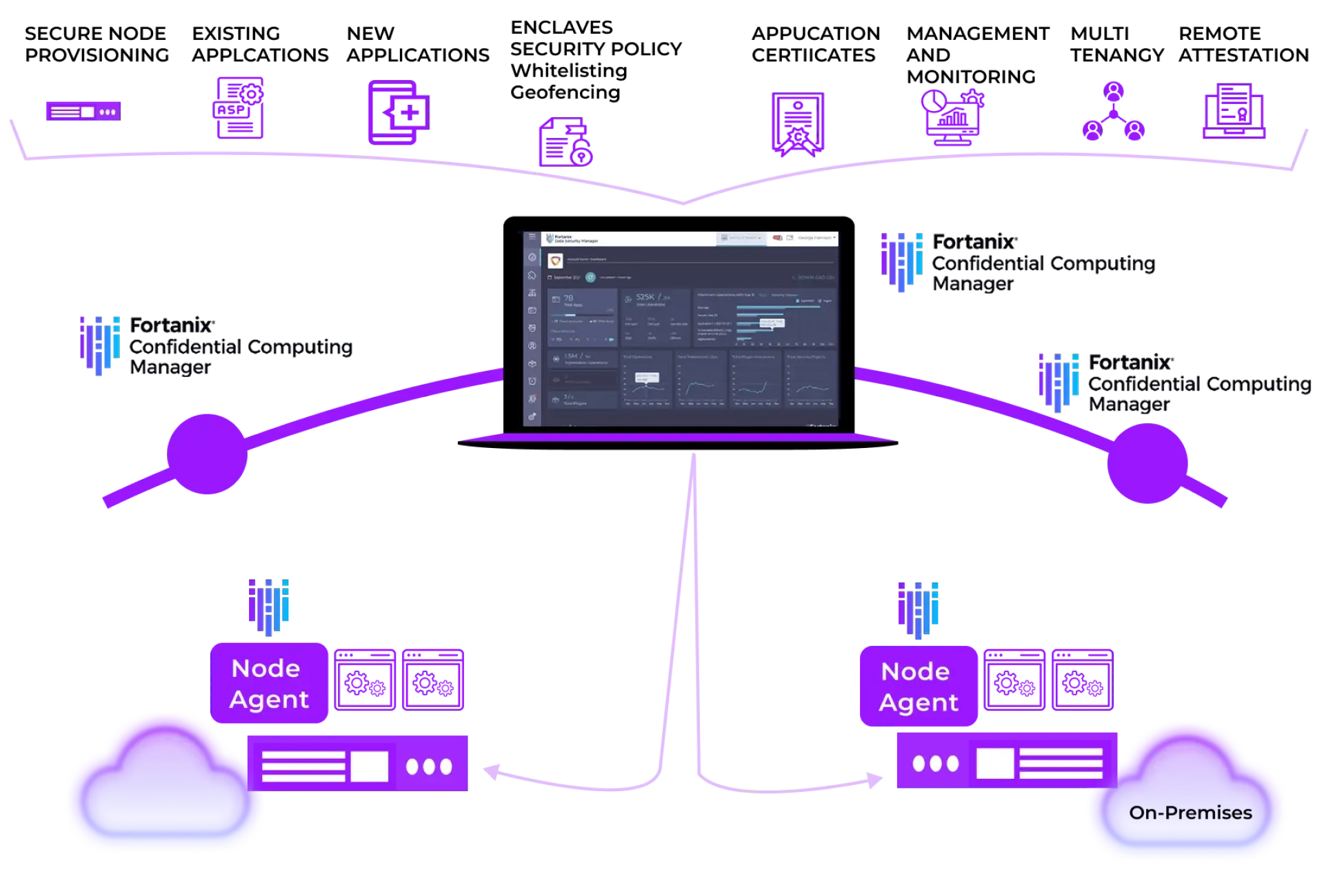
Fortanix provides a single solution to manage the entire enclave lifecycle including creation, deployment, monitoring, and auditing. The solution manages confidential computing infrastructure and applications across multiple public clouds and on-premises environments to provide complete visibility.

Broadset Set of Application Support
Fortanix makes it possible to enable existing applications, enclave-native applications, and pre-packaged application to run in a secure enclave in minutes. This capability is unique and enables widespread adoption of confidential computing with no development or integration costs.

Cryptographically Enforced Policy and Auditing
Fortanix manages and enforces security policies including identity verification, data access control, and attestation to ensure the integrity and confidentiality of data, code, and applications. Using these policies, businesses can implement geo-fencing, and compute affinity to support data regulation policies such as GDPR. Fortanix also provides audit logs to easily verify compliance requirements.
Deployment Architecture
Fortanix offers application teams the fastest, easiest, and most complete solution to run enclave applications today. The platform provides a single pane of glass management of secure enclaves. Additionally, it allows creation of enclaves from existing applications without any modifications, rewrite, or recompile.