Closing the Runtime Trust Gap with Composite Attestation and Policy Driven Key Management
Introduction to Attestation Based Secure Key Release
As enterprises accelerate their adoption of cloud infrastructure, AI pipelines, and multi-tenant architectures, a critical security gap has emerged: the runtime trust gap. While data encryption at rest and in transit has become standard practice, the moment of computation when data must be decrypted for processing remains the weakest link in enterprise security architectures.
This vulnerability is compounded when workloads run on third party infrastructure, where enterprises must balance the benefits of cloud scalability against the need to maintain exclusive control over their most sensitive data and cryptographic keys.
This vulnerability is particularly acute in two contexts: traditional three tier enterprise applications processing sensitive business data, and modern AI pipelines where proprietary models and training data represent significant intellectual property. In both cases, decrypted information in memory can be exposed to memory scraping attacks, insider threats, compromised hypervisors, or privileged cloud administrators.
This raises a fundamental security question: How can enterprises ensure that sensitive cryptographic keys are released only to trusted and verified execution environments, and never to compromised or unauthorized workloads even when the underlying operating system, hypervisor, or infrastructure may be untrusted or compromised?
Attestation based Secure Key Release (SKR) answers this challenge by providing a hardware rooted trust mechanism that releases cryptographic keys only to verified, attested runtime environments. By combining CPU and GPU attestation through Composite Attestation, enterprises can establish a provable chain of trust spanning from silicon to application logic protecting data confidentiality, business logic integrity, and AI model secrecy across the entire compute continuum.
This blog explores how Secure Key Release, powered by Fortanix Confidential Computing Manager (CCM) and Data Security Manager (DSM), delivers enterprise grade protection for both traditional applications and confidential AI workloads.
The Runtime Trust Gap - A Universal Challenge
Modern enterprise applications whether built as traditional three tier systems or cloud native microservices share a common architectural pattern: data flows from storage through processing tiers where it must be decrypted for computation. This creates an exposure window that encryption alone cannot address.
The Processing Tier Vulnerability
In a typical enterprise architecture, the presentation layer handles user interaction, the business logic layer processes data, and the data layer manages persistence. While encryption protects data in storage and TLS secures data in transit, the business logic tier must decrypt data to perform operations creating an in-memory exposure window.
This challenge intensifies in cloud environments where enterprises rely on third party infrastructure. Recent concerns around jurisdictional data access laws have highlighted a critical requirement: enterprises need cryptographic assurance that cloud administrators or infrastructure operators cannot access their protected data, even with privileged access.
The AI Specific Risk
For organizations deploying AI and machine learning workloads, the stakes are even higher. Proprietary models, training datasets, embeddings, and vector databases represent crown jewel intellectual property. In retrieval augmented generation (RAG) pipelines, sensitive enterprise documents must be processed alongside model inference, multiplying the attack surface.
Without protection for data in use, enterprises face three pressing challenges:
- Data Leakage: Proprietary information, model weights, or personal data can be exposed through memory inspection or system logs.
- Compliance Risk: Regulatory frameworks such as GDPR, HIPAA, and emerging AI governance standards require demonstrable safeguards against unauthorized data access.
- Trust Erosion: Without verifiable assurance that data and models remain confidential, organizations hesitate to deploy AI on sensitive workloads or migrate critical applications to cloud infrastructure.
Secure Key Release - The Foundation of Runtime Trust
Secure Key Release (SKR) addresses the runtime trust gap by inverting the traditional trust model. Rather than assuming that infrastructure is trustworthy, SKR requires workloads to prove their integrity before receiving cryptographic keys.
How Secure Key Release Works
The SKR mechanism coordinates two Fortanix platforms to gate key access based on verified attestation:
Fortanix Confidential Computing Manager (CCM) provides hardware based attestation and runtime integrity assurance across all major Trusted Execution Environments (TEEs), including Intel SGX, Intel TDX, AMD SEV SNP, AWS Nitro Enclaves, and NVIDIA GPU TEEs.
Fortanix Data Security Manager (DSM) serves as the centralized, FIPS 140-2 Level 3 certified platform for key management, secrets, tokenization, and cryptographic services. DSM releases keys only after validating that the requesting workload has been attested by CCM.
Key Characteristics of Secure Key Release
- Non-intrusive: Integrates with existing three tier or microservice architectures without code rewrites.
- Policy driven: Keys and secrets are released only when predefined attestation and policy and quorum conditions are met.
- Hardware rooted: Relies on CPU and GPU level attestation rather than software assumptions.
- Attestation gated: Creates a measurable, verifiable chain of trust from hardware to application logic.
Composite Attestation - Verifying the Full Stack
For AI and accelerated computing workloads, CPU attestation alone is insufficient. Composite Attestation extends the trust boundary to include GPU environments, ensuring that both processor and accelerator are verified before any sensitive data or model is released.
The Composite Attestation Flow
When a VM boots or an AI workload starts, Fortanix CCM orchestrates attestation across all active components:
- CPU Attestation: The Confidential VM (running under AMD SEV SNP, Intel TDX) produces a signed attestation report describing its measured state, firmware, and launch policy. CCM verifies this report through manufacturer services such as AMD KDS, Intel PCS, or Azure MAA.
- GPU Attestation: For accelerated workloads, the NVIDIA Remote Attestation Service (NRAS) verifies that the GPU firmware, driver stack, and loaded container match trusted references, ensuring AI models execute inside a confidential GPU enclave.
- Composite Validation: CCM ingests both CPU and GPU reports, validates their signatures, and issues a unified Composite Attestation Certificate (CAC) that binds both TEEs into a single hardware rooted identity.
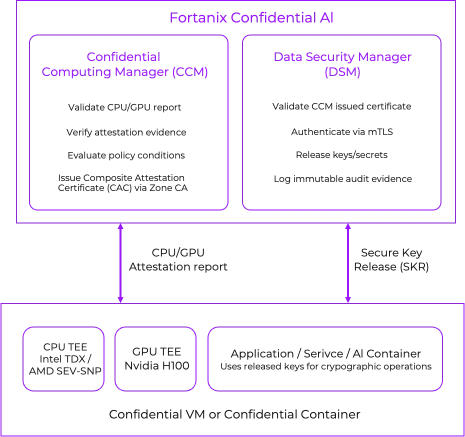
The Secure Key Release Flow
Once composite attestation is complete, the SKR mechanism coordinates with DSM to gate key access:
- Certificate Enrolment: The verified enclave generates an ephemeral key pair and a Certificate Signing Request (CSR) that embeds its composite attestation evidence. CCM validates the request, confirms that attestation metadata matches expected values, verifies that policy conditions (region, workload ID, tenant) are satisfied, and returns a short-lived X.509 certificate signed by a Zone CA.
- Key Request: DSM receives an mTLS request authenticated by the CCM issued certificate from the application or user. It validates that the certificate is issued by a trusted CCM Zone CA before proceeding with the key release.
- Key Release: Only after successful certificate verification does DSM release the required cryptographic material database keys, API tokens, model decryption keys, or signing credentials. Keys are released ephemerally into enclave memory and cannot be reused outside the attested context.
- Immutable Audit: Every attestation, certificate issuance, and key release event is logged with cryptographic timestamps, forming an immutable, regulator ready evidence trail.
Protecting AI and RAG Pipelines | Armet AI
Retrieval Augmented Generation (RAG) has emerged as the preferred architecture for enterprise AI, combining LLM capabilities with proprietary knowledge bases. However, RAG pipelines present unique security challenges: sensitive documents, vector embeddings, and model weights must all be protected throughout their lifecycle.
Confidential AI in Action
By deploying RAG components within attested environments, Composite Attestation with Secure Key Release protects every stage of the AI pipeline:
- Platform Verification: Before loading any dataset or model, CCM verifies both the CPU and GPU environments using AMD KDS, Intel PCS, and NVIDIA NRAS.
- Data Ingestion and Embedding: Keys for encrypted datasets or vector databases are released only to attested compute nodes. Documents and embeddings are encrypted in memory and isolated from the host.
- Secure Retrieval: During runtime, the RAG retriever enclave authenticates to DSM using an attested certificate to fetch decryption keys for documents, embeddings or metadata. Query parameters and results remain protected.
- Model Execution: Proprietary model weights remain encrypted until the GPU enclave is verified. The inference engine receives an ephemeral model key post verification, enabling in enclave decryption.
- End to End Auditability: Each attestation, key release, and GPU workload is logged cryptographically, creating a provable record of where and when models and data were accessed.
This architecture powers Fortanix Armet AI solution, where confidential AI workloads run securely across CPU and GPU enclaves, creating a closed trust loop around the entire AI pipeline. Data is decrypted, processed, and re-encrypted only within verified, policy approved enclaves ensuring model sovereignty, preventing data exfiltration, and meeting emerging AI governance standards.
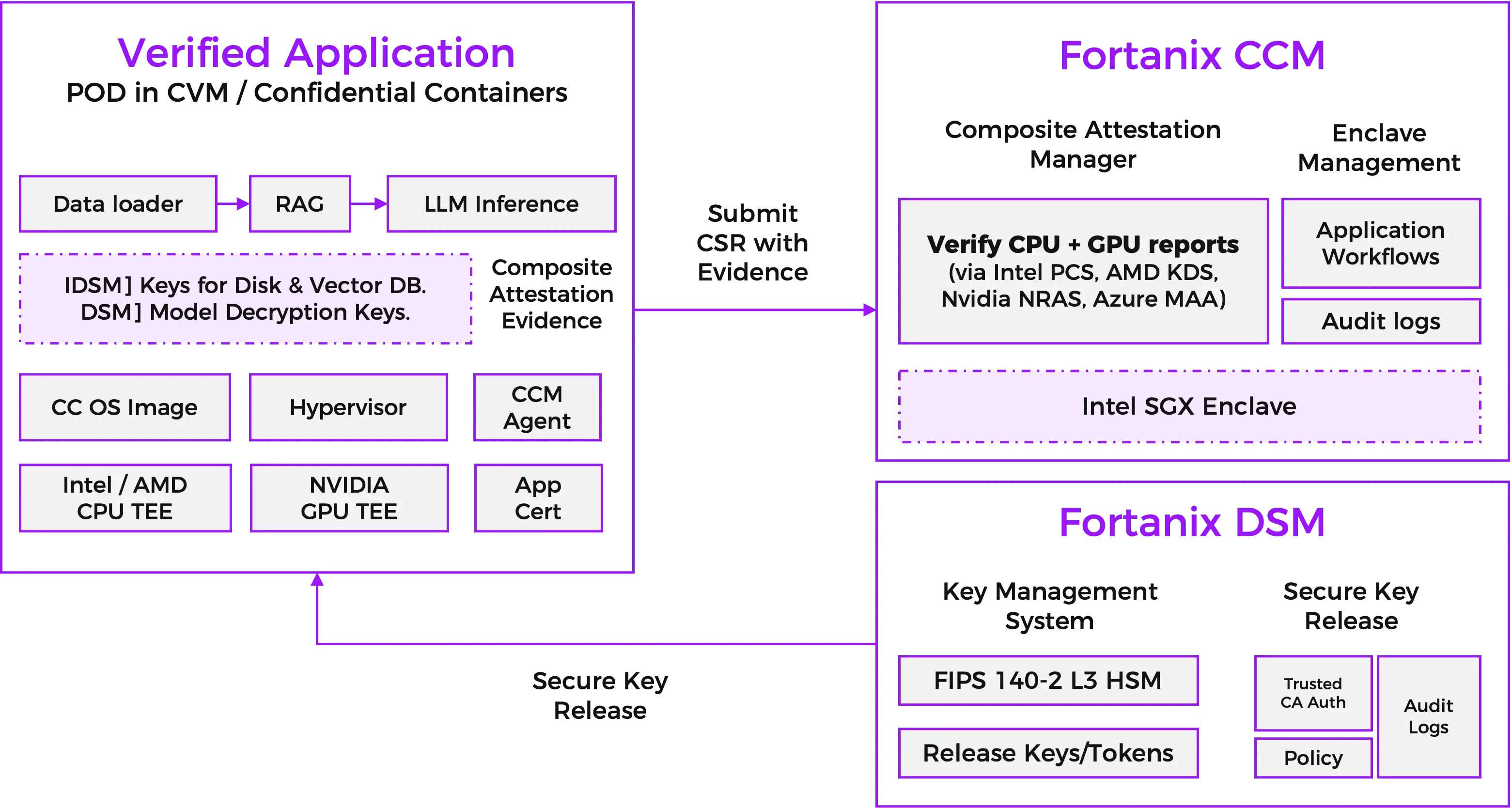
Verified Application Architecture
Diagram showing a verified application POD in CVM with Data loader, RAG, and LLM Inference components, connected to Fortanix CCM for composite attestation and Fortanix DSM for secure key release.
High Impact Use Cases
Secure Key Release integrates into existing enterprise architectures with minimal disruption, supporting multiple deployment models based on organizational requirements.
- Financial Services: Attested transaction processing, confidential tokenization engines, and secure code signing workflows with PCI DSS alignment.
- Government and Citizen Services: Sovereign control over encryption keys even when infrastructure is cloud hosted, with application tiers running inside attested confidential VMs.
- SaaS Multi-Tenant Platforms: Per tenant attested enclaves with zero knowledge platform posture operators and cloud providers cannot access customer plaintext.
- Confidential AI for Regulated Industries: GPU verified model decryption and comprehensive audit trails for healthcare, finance, and manufacturing AI workloads.
Operational Advantages
- Minimal Integration Effort: Deploy workloads as confidential VMs or containers with automatic attestation no application refactoring required.
- Database and Cloud Data Control: Integration with TDE, BYOK, and BYOKMS ensures cloud providers never hold master keys.
- Cloud Native Ready: DSM integrates with Kubernetes via CSI drivers and External Secrets Operator for dynamic secret injection.
- Continuous Compliance: Tamper evident audit logs provide automatic evidence packaging for SOC 2, ISO 27001, HIPAA, and GDPR.
Conclusion
Attestation based Secure Key Release with Composite Attestation closes the runtime trust gap that has long challenged enterprise security. By requiring workloads to cryptographically prove their integrity across both CPU and GPU environments before receiving keys, Fortanix CCM and DSM enable organizations to protect sensitive data in traditional applications, secure proprietary AI models throughout their lifecycle, and maintain sovereign control of cryptographic keys even in multi cloud environments.
With seamless integration, immutable audit trails, and no application refactoring required, Secure Key Release transforms confidential computing from a theoretical safeguard into an operational reality enabling innovation on a foundation of silicon rooted trust.