Demand for a Crypto Cadaster (Krypto-Kataster)
The German Federal Office for Information Security (BSI) has developed the IT-Grundschutz framework to guide organizations in protecting their IT infrastructure. In the 2023 edition, the framework was expanded with the element CON.1 Kryptokonzept. Two specific requirements, A15 and A19, demand that organizations create and maintain a crypto cadaster (Krypto-Kataster).
This requirement is mandatory for public authorities and operators of critical infrastructures (KRITIS). The reasoning is clear: cryptography underpins digital security, but it is also often scattered, inconsistently documented, and poorly governed. Without a structured inventory, organizations cannot prove compliance, detect weaknesses, or react quickly to emerging threats.

Figure 1: Crypto Cadaster
Beyond compliance, a crypto cadaster is also the foundation of crypto agility. Cryptographic algorithms that are considered secure today may be broken tomorrow, especially with the looming quantum threat. Quantum computers currently in development are expected to render widely used algorithms (such as RSA and ECC) insecure.
To prepare for this transition, organizations must adopt post-quantum cryptography (PQC).
But migration to PQC is impossible without first knowing:
- Which algorithms are currently in use
- Which services and applications depend on them
- Which keys and certificates must be replaced
A crypto cadaster provides clarity. It empowers organizations to plan migrations, react to newly discovered vulnerabilities, and implement new security measures in a targeted and efficient way. In short, the BSI’s requirement for a crypto cadaster is not only about today’s compliance; it paves the path for crypto agility and ensures organizations are PQC-ready.
What a Good Crypto Cadaster Solution Must Deliver
While the BSI does not prescribe a format - in theory, the cadaster could even be on paper - in practice this is unmanageable. Large organizations and KRITIS operators may have thousands of keys and certificates spread across diverse environments.
Manual approaches are not only error-prone but also unsustainable, since inventories need to be refreshed continuously.
An effective solution must therefore be automated, scalable, and policy-driven, with these key capabilities:
1. Automated Discovery Across All Environments
- Detect cryptographic usage in cloud services (e.g. AWS RDS, Azure Blob Storage, GCP BigQuery), on-premises tech stack such as databases, file systems, operating systems, hardware keystores, and code repositories.
- Identify encryption for both data at rest and in transit, including network traffic.
- Scale to thousands of resources without degrading performance of production systems.
2. Policy and Compliance Checking
- Highlight services that are not encrypted correctly.
- Flag keys and certificates that do not comply with corporate crypto policies or national/international requirements such as:
- Continuously monitor compliance so that changes in the crypto policy is automatically reflected in updated assessments.
3. Key & Certificate Lifecycle Management
- Track expiration dates of keys and certificates to ensure compliance with lifecycle policies with a Certificate Lifecycle Management (CLM) and a Key Management System (KMS).
- Flag keys that are overdue for rotation or renewal.
4. Contextual Metadata for Remediation
- Associate keys with relevant metadata such as key owner, project ID, or dependent service.
- Provide administrators with the context needed to remediate non-compliance effectively and plan migrations with minimal disruption.
5. Reporting and Auditability
- Generate reports suitable for auditors and regulators, providing evidence of compliance with BSI CON.1.
- Support historical records to demonstrate continuous governance.
Without automation, continuous compliance, and contextual insights, a crypto cadaster would remain a theoretical requirement instead of a practical, living tool for security and governance.
Fortanix Key Insight: The Perfect Match for the Crypto Cadaster
Fortanix Key Insight was designed to meet exactly these requirements - and more. It provides a holistic platform for discovering, analyzing, and governing cryptography across complex environments.
Capabilities
Key capabilities include:
- Comprehensive Discovery
Scans cloud and on-premises resources, databases, file systems, code repositories, and network traffic. Finds weak, misconfigured cryptographic assets without stressing the underlying systems. - Policy-Driven Compliance
User-defined policies can be tailored to international, national or, or internal crypto standards. Non-compliant cryptographic assets and services are automatically flagged. - Certificate Lifecycle Management (CLM)
Key Insight checks expiration and rotation status of keys and certificates. When integrated with a CLM and Fortanix Data Security Manager (DSM), it can remediate directly by rotating these keys. - Integration with Fortanix DSM
DSM acts as a powerful key management system (KMS) with a built-in FIPS 140-2 Level 3 compliant Hardware Security Module (HSM). Together, Key Insight and DSM provide not only visibility but also secure storage, management, and remediation of cryptographic keys. - Reporting and CBOM Support
Key Insight features report capabilities and can import and export Cryptographic Bill of Materials (CBOM), providing verifiable records of cryptographic assets. Reports and CBOMs can be archived for compliance history or analyzed by other applications, ensuring transparency across ecosystems. - PQC Central
A dedicated PQC Central dashboard identifies digital keys that are not quantum-resistant and helps organizations plan their migration. - Multi-Tenancy for Large Organizations
Enables secure separation and governance for multiple departments or organizational entities within one platform. - Metadata and Context for Keys
Cryptographic Assets can be enriched with metadata such as owner, project, or application, providing the necessary context for remediation and lifecycle management. - User Friendliness
All scanning for keys is useless, until the current situation is presented to the user with a clear overview where all problems are made obvious. Key Insight features a user-friendly user interface. One of the Key Insight panels is depicted in Figure 2.
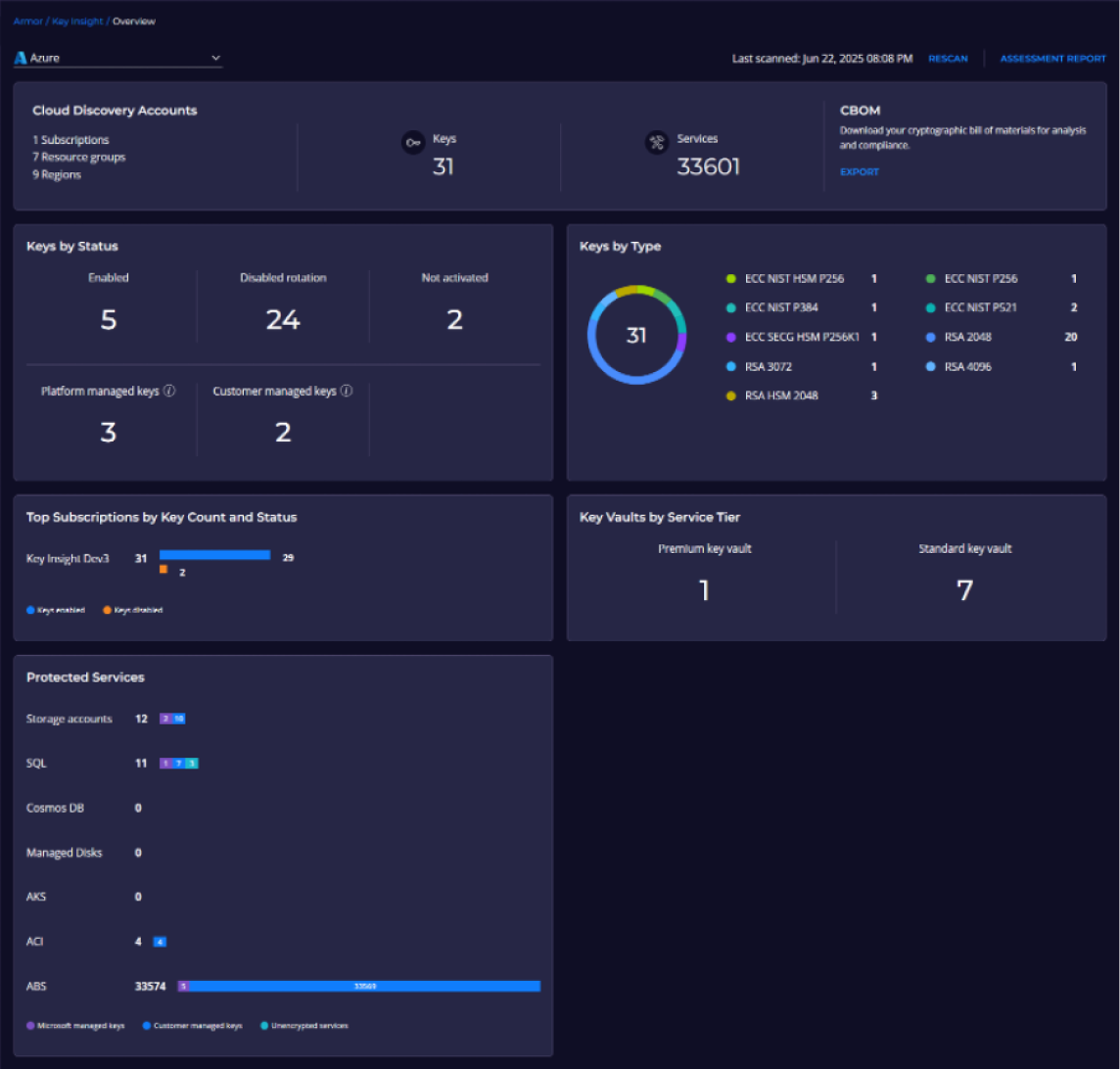
Figure 2: Key Insight User Interface
With these features, Fortanix Key Insight goes beyond simple inventory: it actively enables compliance, crypto agility, and PQC readiness.
High-Level Architecture
Key Insight is capable of scanning keys and resources in the cloud through the standard APIs the cloud service provider supports and of on-premises as depicted in Figure 3.
For the latter, Key Insight features an on-premises scanner that connects to each on-premises resource and retrieves information from these. This is either through standard APIs of the resources, like databases, containers or network components to provide or through an agent, which needs to be installed on the resource.
Typically, this is done for Windows and Linux operating systems. The on-premises scanner connects to Key Insight and asks for instructions, like performing scans on specific resources. On completion of this job, the scanner pushes the collected data to Key Insight for analysis. All the scanning is performed with Read Only permission.
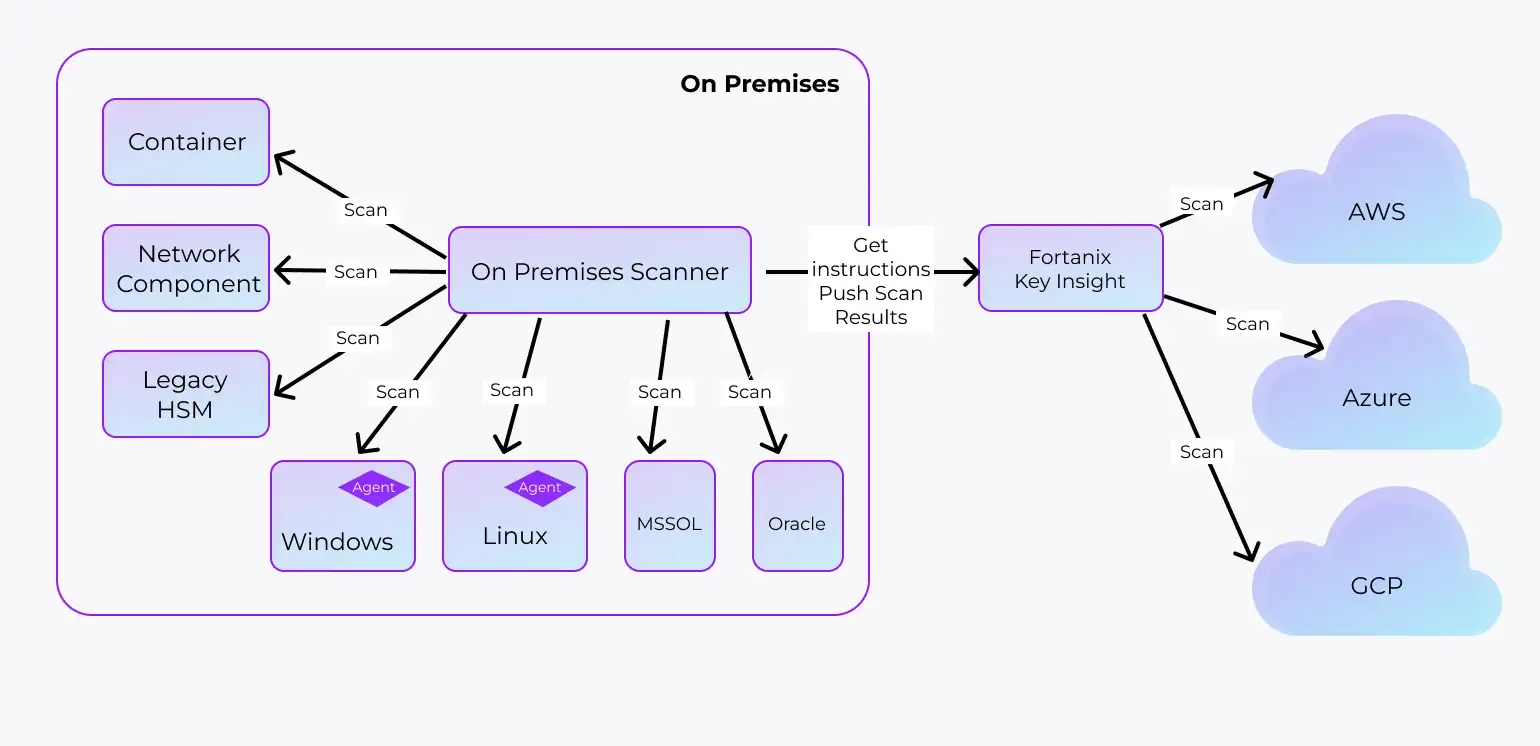
Figure 3: Key Insight High-Level Architecture
Fortanix Key Insight is the Ideal Crypto Cadaster Solution
The BSI’s IT-Grundschutz framework makes a crypto cadaster mandatory for German public authorities and KRITIS organizations (CON.1, A15, A19). This cadaster is more than a compliance requirement; it is the foundation of crypto agility and the path to PQC readiness.
Manual approaches cannot meet the scale and complexity of modern infrastructures. What organizations need is an automated, scalable, policy-driven solution that discovers, analyzes, and governs cryptography across the entire IT landscape.
Fortanix Key Insight is that solution. It combines automated discovery with compliance intelligence, lifecycle management, PQC readiness, and seamless integration with Fortanix DSM for secure key management and remediation.
With support for CBOMs, customizable policies, and multi-tenancy, Fortanix Key Insight transforms the crypto cadaster from a compliance burden into a strategic asset for long-term security
In short: Fortanix Key Insight is the perfect solution to meet the BSI crypto cadaster requirement - today and in the post-quantum future.
For more information, please contact Fortanix.











