The evolving landscape of data protection regulations and data security best practices requires organizations to deploy robust data encryption and cryptographic key management processes that are appropriate to a flexible HCI computing environment.
Primary challenges are:
- Encrypting data in a virtualized HCI environment with traditional key management systems (KMS) can be challenging and may reduce the resource management efficiencies of the HCI model. KMS often add network traffic and latency when processing encryption requests across VM clusters.
- As HCI resources scale to meet shifting workload demands, the encryption system must seamlessly scale alongside them. The solution must also support evolving data protection needs—such as the adoption of post-quantum cryptography—without requiring costly replacement of hardware security modules (HSMs).
- To adhere to regulations like GDPR, PCI DSS 4.0, and HIPAA, Security and IT teams must adapt quickly. This may include implementing file-level encryption, having inventory of cryptographic assets, being in control of encryption keys, and enforcing strict data access controls.
The Solution: Fortanix FSE and Nutanix AOS
With Fortanix Data Security Manager™ (DSM) for Nutanix Hyper-Converged Infrastructure (HCI), users can enhance their data security, apply fine-grained access controls, and manage encryption keys efficiently at scale to defend against malicious actors and maintain regulatory compliance. The integration delivers comprehensive data security capabilities for virtualized computing environments leveraging the Nutanix aggregated storage fabric, namely:

Consolidation of cryptographic key management within a single, scalable, cluster to support changing workload demand.
This eliminates the risks associated with distributed and fragmented solutions, where a single point of failure could compromise critical cryptographic keys and encrypted data.

Ability to protect sensitive data at the file level within virtualized workloads.
Designed for seamless integration, Fortanix File System Encryption (FSE) features an agent-based deployment with no kernel dependencies. The streamlined approach ensures easy management and scalability that complements the capabilities of Nutanix AHV.

Granular data security with Zero Trust principles.
Sensitive data remains accessible only to authorized users and processes, as defined by fine-grained, policy-driven controls, to maintain strict separation between data owners and consumers.
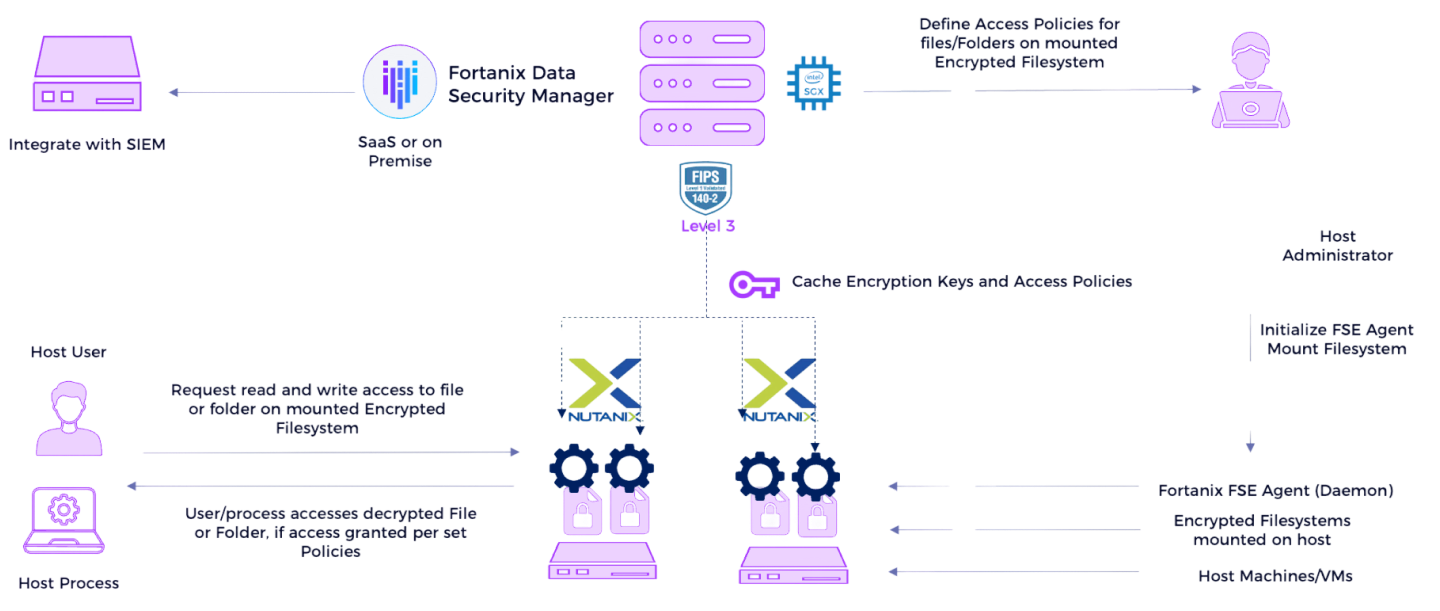
Solution Architecture
Fortanix FSE encrypts Nutanix mounted file systems on individual VMs to protect data specific to these files or folders. Supporting both Windows and Linux operating systems, Fortanix FSE agents provide continuous file-level encryption, comprehensive audit logging, and visibility into key management operations, ensuring compliance and traceability across the Nutanix HCI environment.
Benefits

Unify Security
Apply consistent security from a single UI and manage efficiently at scale.

Automate Data Protection
Automated VM encryption during generation and migration.

Validate and prove compliance
Be in control of your data and keys and keep immutable records.
Key Features

Central control of and visibility into key management across all HCI workloads from a single UI with enterprise-grade security controls.

Advanced key inventory and full key lifecycle management to adhere to security best practices.

Quorum Approvals to prevent accidental key deletion or unauthorized filesystem mounts.

Secure key store in FIPS 140-2 Level 3 HSM, available as SaaS or on-premises.

File System Encryption with scalable agent deployments, based on Open Policy Agent specification, with no kernel dependencies.

Fine-grain policy-driven access controls that restrict access to plain text data solely to authorized users and processes.

Audit logs for both key management and policy enforcement.

Built-in High Availability (HA) and Disaster Recovery (DR).











