Amazon SageMaker notebook instance is a fully managed service provided by Amazon Web Services (AWS) that allows users to create and manage Jupyter Notebook instances in the cloud.
It provides a scalable and flexible environment for data scientists, developers, and machine learning practitioners to build, train, and deploy machine learning models.
A notebook instance in Amazon SageMaker is associated with machine learning (ML) storage volume which serves as the storage for your notebooks, data, and other artifacts.
This volume is attached to the instance and provides persistent storage, allowing you to save your work and access it later.
To have more control over data in the cloud, and meet compliance requirements, it is recommended to encrypt the storage volumes attached to the Notebook instance with Customer managed Keys. This approach is also known as bring your own key (BYOK) encryption.
Our cloud data control (CDC) solution for AWS key management service (KMS) offers complete BYOK lifecycle management using Fortanix Data Security Manager (DSM).
To better understand CDC concepts and their benefits, I encourage you to read Fortanix DSM - Cloud Data Control - Getting Started
To determine the encryption status of your AWS SageMaker notebook instance, and to easily sync keys (BYOK) using Fortanix DSM, perform the following operations:
Part 1: Check status of encryption on AWS
- Sign-in to the AWS Console
- Navigate to Amazon SageMaker -> Notebook instances to list your notebooks.

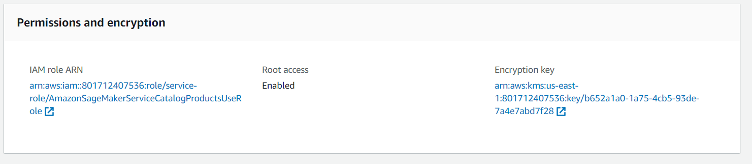
- Click on the instance of interest and scroll down to Permissions and encryption section. If the attribute Encryption key has no value, then the notebook instance is encrypted using default key (AWS managed) rather than Customer managed (BYOK).
Part 2: Sync keys between Fortanix DSM and AWS KMS
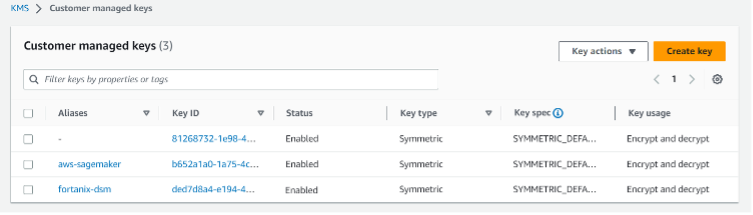
- Fortanix provides an option to generate a key in DSM and then copy the key material into the configured AWS KMS. Another option DSM provides is to create a virtual key by importing the key from AWS KMS to the DSM CDC group.
In the latter method, the virtual key only stores the key attributes, but not the key material itself in DSM. The following guides describe BYOK lifecycle management for AWS using DSM and the steps to import keys:
Fortanix DSM - AWS KMS BYOK (Bring Your Own Key)
Exporting Fortanix Data Security Manager keys to Cloud Providers for BYOK - AWS - Section Sync keys of DSM - AWS KMS BYOK guide mentions the steps to connect DSM to AWS KMS and sync keys between them to a virtual key in DSM CDC group.

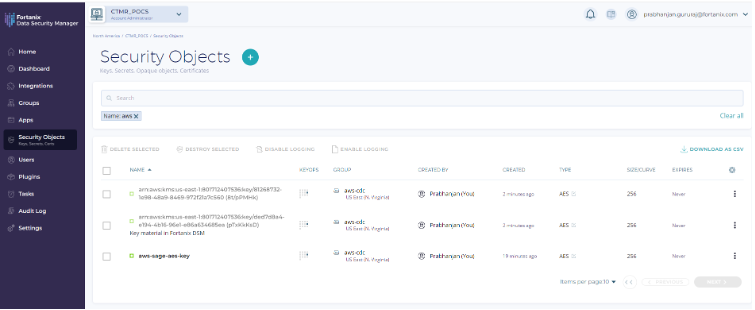
- Once the keys are synchronized, we should be able to see the list of virtual keys or secret objects on DSM. In the sample below, the AES 256 secret object aws-sage-aes-key in the aws-cdc group is of our interest, which will be used to encrypt the storage volume of notebook instance.
Part 3: Encrypt notebook with customer managed key
- Follow steps 1-2 above and click Create notebook instance, and fill the required attributes
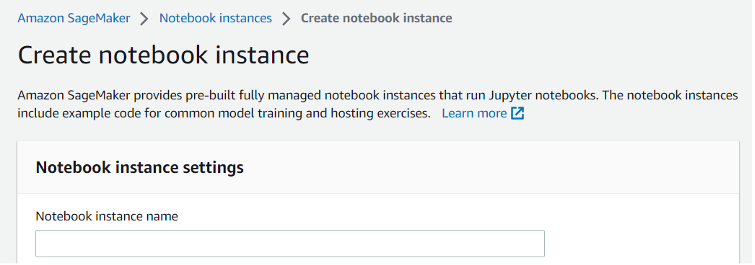
- In the Permissions and encryption section, select the name (alias) of KMS customer managed key (CMK)
of interest for the attribute Encryption key - optional, synced earlier with Fortanix DSM in step 6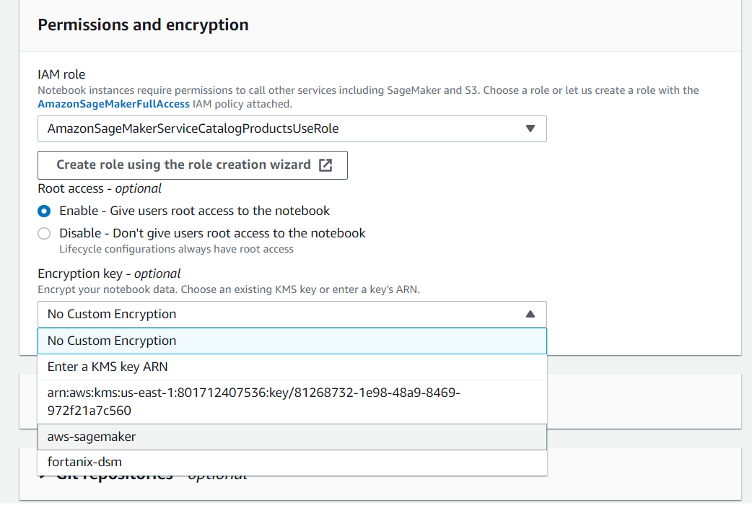
- Fill the other required and optional attributed in the page and click on Create notebook instance
- Repeat steps 1-3 above to view the Permissions and encryption section of the newly created notebook instance. The attribute Encryption key will specify the customer managed key providing additional control to users over notebook attached storage volumes.
 By protecting the storage volume attached to your Amazon SageMaker notebook instance with a customer managed key or BYOK, you add an additional layer of security and control over the data in AWS. For details on how to perform native key lifecycle management in AWS KMS using Fortanix DSM, refer to the User's Guide: Fortanix DSM AWS KMS Cloud Native Key Management.
By protecting the storage volume attached to your Amazon SageMaker notebook instance with a customer managed key or BYOK, you add an additional layer of security and control over the data in AWS. For details on how to perform native key lifecycle management in AWS KMS using Fortanix DSM, refer to the User's Guide: Fortanix DSM AWS KMS Cloud Native Key Management.










