2021’s SANS Cloud Security Survey has been released and is an important read for security stakeholders within an organization. It is also worth tuning into the panel discussion recording that presented and analyzed the findings if you missed it live.
In the panel discussion, Dave Shackleford, SANS analyst and CEO of Voodoo Security, and David Greene, Chief Revenue Officer, Fortanix, discusses the findings and share some security best practices. This blog highlights some of the findings of the survey and analysis from the panel discussion.
The goal of the SANS 2021 Cloud Security Survey is to provide insight into how organizations are using cloud today and how security is being handled by organizations. As more and more organizations shift their IT strategies to cloud-based infrastructure, security teams are also evolving to adopt new cloud security services that offer more effective controls and capabilities.
This SANS survey explored the types of services organizations are using, what types of controls and tools provide the most value, and how effective cloud security brokering is for a range of use cases. [source]
Finding 1: Go Ahead and Put Your Data in the Cloud, but it’s up to you to keep it secure:
The survey showed increasing amount of sensitive data in the cloud, suggesting that many companies are implicitly trusting their cloud providers.
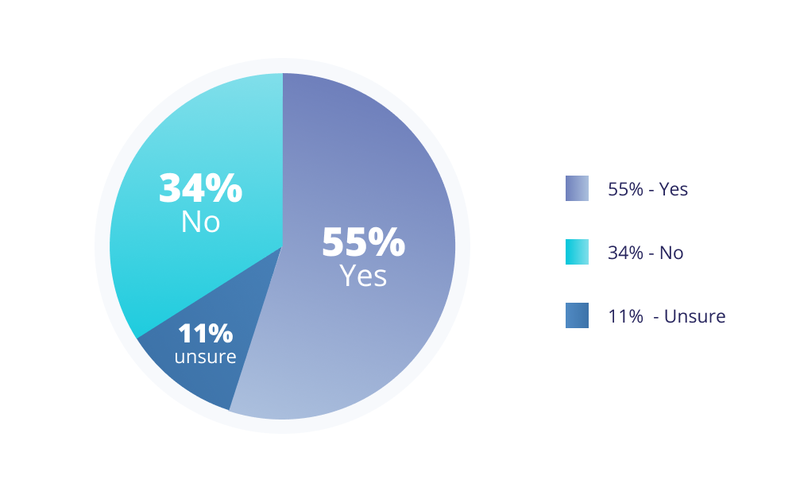
Question is should they be implicitly trusting cloud providers to move data to cloud?
The question of should you put your data in the cloud is separate from should you trust your cloud provider. There are lot of advantages to running in the cloud – scalability, ease of operations, great cloud native services. But none of that protects your data.
Organizations looking to move their workloads to cloud are often caught in a conundrum. With increasing need to move to cloud for flexibility, scalability, and agility, CISO’s also need to ensure that this is done without exposing sensitive data to increased cyber risks.
Security and data privacy continue to be the primary concern slowing down cloud adoption. For data security, cloud service providers offer best practices and resources, but it is a shared responsibility between cloud service provider and the organization.
Go ahead and put your data there but take the steps to keep it safe. Organizations need to take concrete measures to ensure data security as required by compliance regimes, government data breach regulations and to protect their confidential intellectual property.
Read this whitepaper: CISO Guide: The digital transformation of data security to understand some of the data security measures that can be taken to safeguard the sensitive data and how Fortanix can help.
Finding 2: If you think data security is expensive, look at the cost of data breaches.
SANS survey asked whether privacy regulations such as the General Data Protection Regulation (GDPR) were impacting existing or planned cloud strategies, and these were the results:

How is that changing how customers approach data security?
Much of the sensitive data is also governed by privacy regulations. There has been an explosion in activity from data privacy regulators, with regulations like General Data Protection Regulation (GDPR) and the California Consumer Protection Act (CCPA) increasing the cost of leaving this data unprotected.
Data breaches are now costlier than ever. For example, With CCPA businesses can be required to pay damages between $100 to $750 per resident, per incident, and can be fined up to $7,500 for each intentional violation and $2,500 for each unintentional violation.
This means that a data breach involving a million consumers, of which there have been many, could cost hundreds of millions of dollars in penalties per breach. Regulations, such as the GDPR and CCPA, have dramatically increased pressure on security and risk management (SRM) leaders.
Data breaches are now much more expensive, more visible, and more complicated. This has also led to compliance teams getting new power (but not necessarily new budget). Budget still wrests with the security and IT teams.
The Ebook ‘Data privacy in public cloud’ highlights some of the data privacy controls that can be implemented for public cloud and how Fortanix can help.
Finding 3: Cloud security controls are still focused on the perimeter, not the data
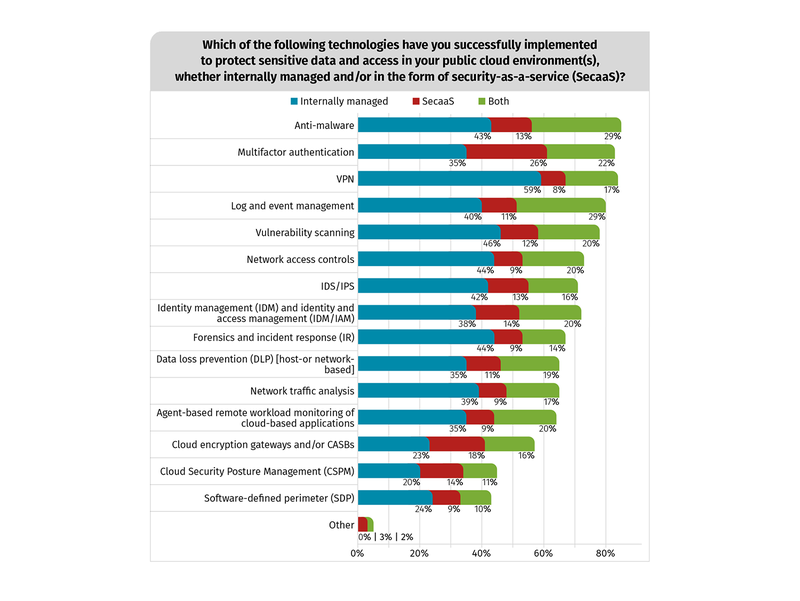
Why doesn’t encryption appear in the survey as a cloud control used to protect sensitive data?
This is not really surprising. Pretty typical list of what people have bought in the past, and there is certainly inertia in that. This clearly illustrates how thinking needs to change when going to the cloud. These are generally the same investments one would make for an on-prem data center.
Largely castle / moat defense. Keep bad guys out, then hunt them down when they get in. Fortanix believes data and identity are the new perimeter.
As simple as this sounds, it requires a fundamental shift in how we approach cybersecurity: from building network perimeters around data to assuming everything else is potentially compromised and securing the data itself.
Finding 4: You can still use Cloud Provider APIs and keep control of your data
As per the survey almost half of the respondents are using Cloud vendor APIs for security operations.
How should this work when using multiple cloud platforms?
The best option is to insert security upstream from the cloud APIs. This means integrate with cloud KMS but manage externally.
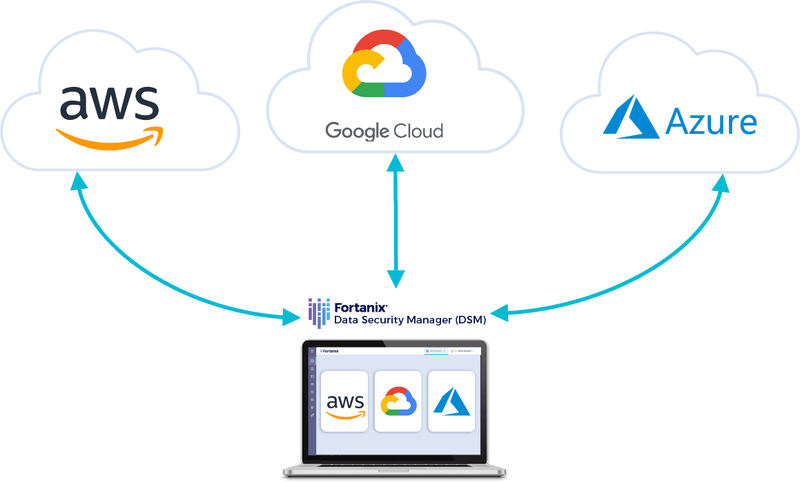
Increased adoption of multicloud has fragmented data across different public clouds. And that makes securing data in this multicloud world more complex. To guarantee universal protection of cloud data, security and cloud teams need to get control and visibility of all data from a single pane of glass.
This unified approach ensures absolute control over data across clouds by allowing organizations to store and manage all the cryptographic keys and secrets in one place and separate the data from the keys that it protects.
Here’s a webinar that discusses data security across multicloud environments.
Finding 5: Current solutions make it difficult to integrate between In-house environment and public cloud, but new solutions make it easier.
Survey points out that many customers are going to have some combination of on-premises and cloud applications and when it came to security encryption was low on this list. Quite simply, this is because it has been hard to use encryption to protect data in mixed environments.
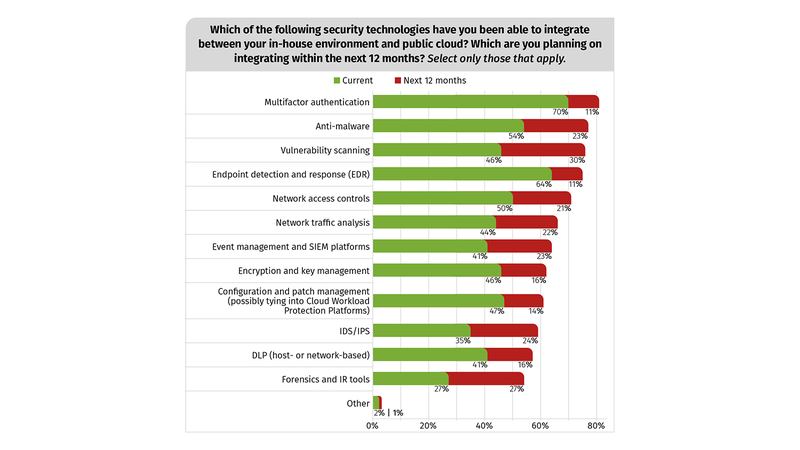
Why encryption is low on priority and what needs to be done?
Commercial data encryption was invented in 1976. You can still buy the successor to that product. But most of these HSM solutions have typically treated on-premises data security and cloud data protection as two separate problems with two separate solutions delivered on two separate technology stacks.
Moving from one to the other is difficult making cloud deployments almost impossible. These are not designed for cloud. Many organizations still rely on these legacy HSM solutions and find them inadequate to meet the security needs within hybrid environments.
This whitepaper “Five Step Guide to Modernizing Data Security” maps out a practical path to using Fortanix technology alongside your existing HSMs to improve on-premises, public cloud, and hybrid cloud data security.
Finding 6: Plan an API-driven automated security future
One of the key differences between cloud and on-prem environments is that cloud is significantly more automated.
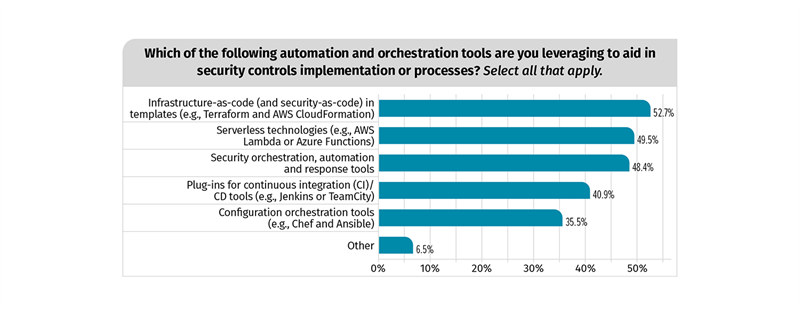
How does this impact strategies for data security?
This means you need to extend security to cloud APIs, credentials, and secrets. DevOps teams have enthusiastically adopted cloud tools, agile development methodologies, and API-driven “infrastructure as code”.
The push for speed and continuous delivery frequently collides with the more deliberate world of security, and certainly does not have thoughtful support of aging integrations.
When security teams do get visibility, they are often appalled to see widely shared passwords, unsecured databases, and PII in test files left sitting on public clouds. A collateral benefit of modernizing data security is the introduction of “DevOps-friendly” security tools.
Capabilities like RESTful APIs (just like the APIs DevOps uses for all the rest of its work), consistent cryptography services on-prem and in the cloud, and support for containers all make it easier to integrate data security into DevOps. Secrets management and tokenization are critical data security measures for DevOps.
Headwinds to continued or expanded cloud usage?
And with increased adoption towards cloud the most pertinent question is what should security and IT professionals do over the next 12 months?
The biggest challenge that security professionals are going to face is a lack of cybersecurity expertise to handle data security concerns. Even though organizations may know there is a problem they may not be able to find the right answers.
Data that you need to keep secure is literally everywhere – it's on public cloud platforms, in SaaS applications, your data warehouse, your storage infrastructure, back in your datacenter. The way to keep data protected everywhere is to encrypt it – encrypted data is as safe on your front lawn as it is in your data center.
Fortanix makes encryption at scale easy, centrally managed, and integrated right into your applications without having to be a cryptography expert. Key management, cloud data security, database encryption, tokenization all in one unified solution.
In this webcast, SANS analyst and survey author Dave Shackleford joins David Greene, Chief Revenue Officer, Fortanix for the deep-dive discussion and analysis of survey results. Tune in now!
How Fortanix Helps with Cloud Security?
According to Gartner, 81% of businesses are adopting a hybrid cloud and multi-cloud strategy to augment their internal datacentres. The challenges of protecting data and using encryption for multiple hybrid, public cloud, and on-premises environments increases complexity, cost, and security risk.
Organizations often end up with multiple proprietary Key Management Solutions (KMS), resulting in key sprawl. There is a high risk to lose track of where keys are, who accessed them, when, and from where.
The Fortanix solution seamlessly integrates with hybrid and multicloud key management services to enable organizations to centrally manage the lifecycle of all keys, from a single interface, no matter if these keys are used on-premises, or in the cloud.
- FIPS 140-2 level 3 HSMs: Encryption keys are always under organizations' control and can be stored on highly secure, FIPS 140-2 level 3-certified HSMs.
- Bring-Your-Own-Key/Key Management Service: This multi cloud SaaS key management solution offers Bring Your Own Key (BYOK) and Bring Your Own Key Management Service (BYOKMS), allowing organizations to segregate their keys from the data.
- Centralized policy management: With Fortanix, organizations can centrally define and enforce granular, uniform access control policies.
Related Read: Finding from RSA 2018 Cloud Security Survey
Reach out to us sales@fortanix.com.









